Access control vulnerabilities
Access Control Vulnerabilities aur Privilege Escalation
Is section mein hum cover karenge:
- Privilege Escalation kya hota hai.
- Access Control se related jo vulnerabilities hoti hain, unke types.
- Access Control Vulnerabilities ko kaise prevent karein.
Labs
Agar aapko Access Control Vulnerabilities ke basic concepts ka knowledge hai aur aap inhe realistic, deliberately vulnerable targets par exploit karna chahte hain, toh aap niche diye gaye link se labs access kar sakte hain.
Access Control Kya Hota Hai?
Access Control ka matlab hai constraints apply karna taaki ye ensure kiya ja sake ki kaun ya kya kisi action ko perform karne ya kisi resource ko access karne ke liye authorized hai.
Web Applications ke context mein, Access Control teen major cheezon par depend karta hai:
- Authentication: Ye confirm karta hai ki user wahi hai jo wo claim kar raha hai.
- Session Management: Ye identify karta hai ki konsi subsequent HTTP requests usi user dwara ki ja rahi hain.
- Access Control: Ye decide karta hai ki user jo action perform karna chahta hai, usko allow kiya jaana chahiye ya nahi.
Broken Access Control
Broken Access Controls bahut common hote hain aur ye critical security vulnerability create kar sakte hain.
Access Control ka Design aur Management ek complex aur dynamic process hai jisme business, organizational aur legal constraints ko technical implementation ke saath align karna hota hai.
Access Control ka design human decisions par depend karta hai, is wajah se errors hone ka chance high hota hai.
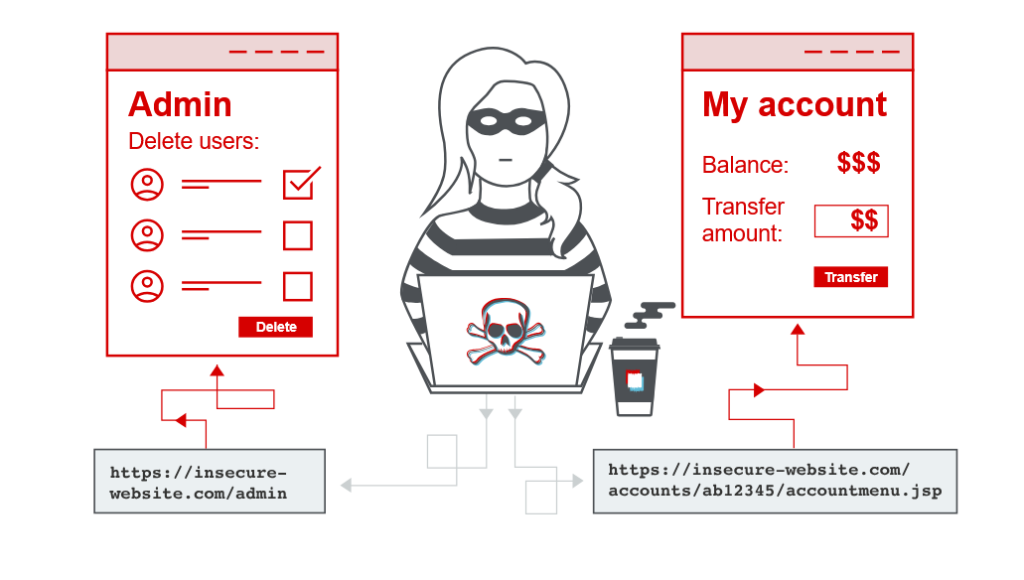
Vertical Access Controls
Vertical access controls aise mechanisms hote hain jo sensitive functionality ka access sirf specific types ke users tak limit karte hain.
Isme different types ke users ko alag-alag application functions ka access diya jata hai. Example ke liye, ek administrator kisi bhi user ka account modify ya delete kar sakta hai, jabki ek ordinary user ke paas ye permissions nahi hoti.
Vertical access controls security models ka ek fine-grained implementation hote hain jo business policies jaise ki separation of duties aur least privilege ko enforce karne ke liye design kiye jate hain.
Example of Vertical Access Controls
Maan lo ek banking application hai jisme teen types ke users hain:
- Customer – Apne account ka balance check kar sakta hai aur fund transfer kar sakta hai.
- Bank Employee – Customer ke account details dekh sakta hai aur unke transactions verify kar sakta hai.
- Administrator (Bank Manager) – Kisi bhi customer ka account modify, suspend ya delete kar sakta hai.
👉 Scenario:
Agar ek customer bank manager ka role access karne ki koshish kare, toh system usko access denied message dega kyunki uske paas required privileges nahi hain. Yehi Vertical Access Control ka kaam hai – har user ko sirf uske role ke hisaab se functions ka access milta hai.
Horizontal Access Controls
Horizontal access controls aise mechanisms hote hain jo resources ka access sirf specific users tak limit karte hain.
Isme same type ke resources hote hain, lekin har user ko sirf uske khud ke resources ka access milta hai.
Example:
Ek banking application me:
- User A sirf apne bank account transactions dekh sakta hai aur payments kar sakta hai.
- User B apne account ke transactions dekh sakta hai, lekin User A ke account ka access nahi hoga.
👉 Scenario:
Agar User A kisi dusre user (User B) ka account access karne ki koshish kare, toh system usko access denied message dega, kyunki uske paas authorization nahi hai.
Horizontal Access Controls ensure karte hain ki users ek hi type ke resources ka access karein, lekin sirf apne khud ke resources tak limited rahein. 🚀
Context-Dependent Access Controls
Context-dependent access controls aise controls hote hain jo application ke state ya user ke interaction ke basis par access ko restrict karte hain.
Ye controls ensure karte hain ki koi user galat order me actions perform na kare.
Example:
Ek retail website me:
- User shopping cart me items add kar sakta hai.
- Payment hone ke baad user shopping cart modify nahi kar sakta.
👉 Scenario:
Agar user payment karne ke baad cart me changes karne ki koshish kare, toh system modification allow nahi karega.
Context-Dependent Access Controls ensure karte hain ki users sirf allowed context me hi actions perform kar sakein. 🚀
Examples of Broken Access Controls
Broken access control vulnerabilities tab hoti hain jab koi user aise resources ya actions access kar sakta hai jo uske authorized nahi hote.
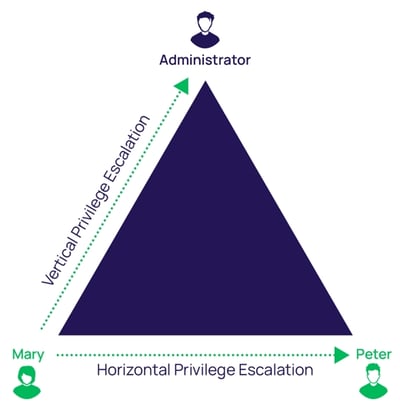
Vertical Privilege Escalation
Agar ek user aisi functionality access kar sake jo uske liye allowed nahi hai, to ise vertical privilege escalation kehte hain.
👉 Example: Agar ek non-administrative user kisi admin page ka access le sake jahan wo user accounts delete kar sakta hai, to ye vertical privilege escalation ka case hoga.
Unprotected Functionality
Basic level par, vertical privilege escalation tab hota hai jab application kisi sensitive functionality ke liye koi protection enforce nahi karti.
👉 Example: Ek website me admin functions sirf admin ke welcome page par dikhaye gaye hain, lekin ek normal user bhi direct URL se admin functions ko access kar sakta hai.
Kisi website ka sensitive functionality host karna kuch is tarah ho sakta hai:
🔗 https://insecure-website.com/admin
Agar ye URL kisi bhi user ke liye accessible hai, to ye security vulnerability hai.
Kahi baar ye robots.txt file me bhi disclose ho sakta hai:
🔗 https://insecure-website.com/robots.txt
Agar URL kahin disclosed nahi bhi hai, to attacker ek wordlist ka use karke brute-force kar sakta hai aur sensitive functionality locate kar sakta hai.
Security by Obscurity
Kayi cases me, sensitive functionality ko chhupane ke liye uska less predictable URL diya jata hai. Is technique ko “security by obscurity” kehte hain.
Lekin sirf URL ko obfuscate karna effective access control nahi deta, kyunki users alag-alag tareekon se is URL ko discover kar sakte hain.
👉 Example:
Agar ek application apni admin functionalities ko is URL par host karti hai:
🔗 https://insecure-website.com/administrator-panel-yb556
To ye directly guess karna mushkil ho sakta hai, lekin application khud hi users ko ye URL leak kar sakti hai.
Kayi baar, JavaScript code me bhi ye URL expose ho sakta hai. Example dekhiye:
var isAdmin = false;
if (isAdmin) {
…
var adminPanelTag = document.createElement(‘a’);
adminPanelTag.setAttribute(‘href’, ‘https://insecure-website.com/administrator-panel-yb556’);
adminPanelTag.innerText = ‘Admin panel’;
…
}
</script>
👉 Issue:
Ye script admin users ke UI me link add karti hai agar isAdmin = true ho.
Lekin ye script sabhi users ke liye visible hoti hai, chahe wo admin ho ya na ho.
✅ Solution: Proper access controls enforce karna zaroori hai, sirf URL chhupane se security ensure nahi hoti.
Parameter-based Access Control Methods
Kuch applications user ke access rights ya role ko login ke time determine karti hain aur fir is information ko user-controllable location me store karti hain, jaise ki:
- Hidden field
- Cookie
- Preset query string parameter
Fir application submitted value ke basis par access control decisions leti hai.
👉 Example:
🔗 https://insecure-website.com/login/home.jsp?admin=true
🔗 https://insecure-website.com/login/home.jsp?role=1
❌ Issue:
Ye approach insecure hai, kyunki user is value ko modify kar sakta hai aur unauthorized functionality access kar sakta hai, jaise administrative functions.
✅ Solution: Proper server-side access control implement karna zaroori hai, taaki user-controlled parameters manipulate karke unauthorized access na le sake.
Broken Access Control due to Platform Misconfiguration
Kuch applications platform level par access controls enforce karti hain. Ye user ke role ke basis par specific URLs aur HTTP methods restrict karne ka kaam karti hain.
👉 Example:
Ek application kisi rule ko is tarah configure kar sakti hai:
DENY: POST, /admin/deleteUser, managers
🔹 Iska matlab:
Ye rule managers group ke users ko /admin/deleteUser URL par POST request bhejne se rokta hai.
❌ Issue: Access Control Bypass
Is approach me galtiyan ho sakti hain, jisme attackers access controls bypass kar sakte hain.
Kuch application frameworks non-standard HTTP headers support karte hain jo original request ke URL ko override kar sakte hain, jaise:
- X-Original-URL
- X-Rewrite-URL
Agar ek website sirf front-end par strict URL restrictions lagati hai, lekin backend request headers allow karta hai URL override hone ko, to access control bypass ho sakta hai.
👉 Example Request:
POST / HTTP/1.1
X-Original-URL: /admin/deleteUser
...
✅ Solution:
1️⃣ Back-end level par strict access control implement karein.
2️⃣ Non-standard HTTP headers ka misuse hone se bachane ke liye validation karein.
3️⃣ Only server-side authentication and authorization mechanisms use karein.
Alternative Attack: HTTP Method Manipulation
Ek alternative attack HTTP method par depend karta hai jo request me use hoti hai.
Jo front-end controls pehle explain kiye gaye hain, wo URL aur HTTP method ke basis par access restrict karte hain.
Lekin kuch websites alag-alag HTTP request methods ko tolerate karti hain jab koi action perform kiya jata hai.
👉 Agar ek attacker restricted URL par GET (ya koi aur method) use karke action perform kar sake, to wo platform-level access controls bypass kar sakta hai.
Broken Access Control due to URL-Matching Discrepancies
Alag-alag websites incoming request ke path ko match karne ke tareeke me differ karti hain.
👉 Example:
Agar ek website capitalization tolerate karti hai, to /ADMIN/DELETEUSER request automatically /admin/deleteUser endpoint par map ho sakti hai.
❌ Issue: Agar access control mechanism strict na ho, to ye endpoints alag-alag treat ho sakte hain, aur restrictions sahi se enforce nahi hongi.
Spring Framework me Security Issue
Spring framework me agar useSuffixPatternMatch option enable ho, to koi bhi random file extension wali request ek valid endpoint se match ho sakti hai.
👉 Example:
🔗 /admin/deleteUser.anything
Ye request /admin/deleteUser se match ho jayegi.
💡 Spring 5.3 se pehle ye option by default enabled hoti thi!
Trailing Slash Bypass
Kuch systems /admin/deleteUser aur /admin/deleteUser/ ko alag treat karte hain.
Agar access control ek format par enforce ho raha hai, to dusre format me bypass ho sakta hai.
Horizontal Privilege Escalation
Agar ek user apne resources ke alawa kisi aur user ke resources access kar sake, to ise horizontal privilege escalation kehte hain.
👉 Example:
🔗 https://insecure-website.com/myaccount?id=123
Agar attacker id=123 ko id=456 se replace kare, to wo dusre user ka account access kar sakta hai.
📌 Ye ek IDOR (Insecure Direct Object Reference) vulnerability ka example hai!
IDOR (Insecure Direct Object References)
IDOR ek access control vulnerability hai jisme user-controlled parameters ko objects access karne ke liye directly use kiya jata hai.
⚠ Example Attack:
Predictable IDs: Agar website me sequential user IDs ho (123, 124, 125…), to attacker easily guess karke dusre users ke data ko access kar sakta hai.
GUIDs ka use: Agar random GUIDs use kiye jayein (
f5a3b9c7-8d12), to attackers ke liye guessing mushkil ho jati hai.
💡 Lekin agar application kahin aur GUIDs leak kar rahi ho (messages, reviews, etc.), to attackers inhe discover kar sakte hain!
Redirect Data Leakage
Kayi baar website unauthorized users ko login page par redirect karti hai, lekin redirect response me sensitive data leak ho sakta hai!
Horizontal to Vertical Privilege Escalation
Agar attacker kisi zyada privileged user ka account hack kar le, to horizontal escalation vertical escalation ban sakti hai.
👉 Example:
🔗 https://insecure-website.com/myaccount?id=456
Agar id=456 ek admin user ka hai, to attacker admin functionalities tak access le sakta hai.
Admin page par password reset ka option ho sakta hai.
Admin panel me sensitive data ya functionalities ho sakti hain.
Access Control in Multi-Step Processes
Kayi websites me multi-step processes hote hain, jaise:
1️⃣ Form load karna (user details show karna)
2️⃣ Changes submit karna
3️⃣ Changes review karna aur confirm karna
❌ Issue: Agar website pehle do steps me access control enforce kare, lekin last step me na kare, to attacker pehle steps skip karke direct last step me request bhej sakta hai.
Referer-Based Access Control Bypass
Kuch websites Referer header ke basis par access control enforce karti hain.
👉 Example:
Main admin page (
/admin) par proper access control hai.Sub-pages (
/admin/deleteUser) sirf Referer check karti hain.
❌ Issue: Attacker forged request bhejkar fake Referer header add kar sakta hai aur unauthorized access le sakta hai!
Location-Based Access Control Bypass
Kuch websites user ke geographical location ke basis par access control implement karti hain (banking apps, media services, etc.).
💡 Attackers ise bypass kar sakte hain:
✅ VPN ya proxy servers use karke
✅ Client-side geolocation modify karke
Access Control Vulnerabilities Ka Prevention
Access control vulnerabilities ko prevent karne ke liye defense-in-depth approach follow karein:
✅ Kabhi bhi sirf obfuscation (chhupane) par bharosa na karein.
✅ Jo resource public nahi hona chahiye, usko by default deny karein.
✅ Ek centralized access control mechanism use karein.
✅ Code level par access control rules enforce karein.
✅ Regularly audit aur test karein ki access controls sahi kaam kar rahe hain.
1️⃣ Question:
👉 Access Control kya hota hai? Kyu important hai?
✅ Answer:
Access Control ek security mechanism hai jo users ke access ko restrict karta hai based on their roles aur permissions. Iska main purpose unauthorized access ko prevent karna hota hai.
⚡ Types of Access Control:
Discretionary Access Control (DAC) – User apne data par control rakh sakta hai.
Mandatory Access Control (MAC) – Strict security policies enforced hoti hain (Military-grade).
Role-Based Access Control (RBAC) – Access based on user’s role (Admin, User, Guest, etc.).
Attribute-Based Access Control (ABAC) – Access dynamic attributes jaise time, location, and device ke basis par hota hai.
✅ Example:
Agar ek banking application me normal user admin panel access kar sake, to ye access control vulnerability hogi.
2️⃣ Question:
👉 IDOR vulnerability kya hoti hai? Iska real-world example do.
✅ Answer:
IDOR (Insecure Direct Object Reference) ek access control vulnerability hai jisme user-controlled input ka sahi validation nahi hota, jiske wajah se unauthorized data access ho sakta hai.
⚡ Example:
🔗 https://bank.com/myaccount?id=123
Agar ek attacker id=123 ko id=456 me change kare aur kisi aur user ka account details dekh sake, to ye IDOR vulnerability hogi.
✅ Real-World Example:
Facebook me ek bug mila tha jisme ek user dusre user ke private photos ko access kar sakta tha sirf URL manipulate karke.
3️⃣ Question:
👉 IDOR vulnerability ka detection kaise karte hain?
✅ Answer:
IDOR vulnerability ko detect karne ke liye manual testing aur automated tools dono use kiye jate hain.
🔹 Manual Testing:
Parameter Tampering: URL me ID change karke test karna.
Session Manipulation: Different user ke session se access check karna.
API Testing: API requests me input modify karke unauthorized access check karna.
🔹 Automated Tools:
✅ Burp Suite – ID tampering aur API fuzzing ke liye use hota hai.
✅ OWASP ZAP – Automated IDOR detection ke liye use hota hai.
4️⃣ Question:
👉 Access Control Bypass ka ek real-world scenario batao.
✅ Answer:
Agar ek website admin panel ka link directly user interface me na dikhaye, lekin actual admin URL accessible ho, to access control bypass possible ho sakta hai.
⚡ Example:
🔗 https://secure-website.com/admin
Agar ek non-admin user bhi direct URL access karke admin panel me ghus sake, to ye broken access control vulnerability hogi.
✅ Fix:
Proper authentication aur authorization check implement karna.
Server-side access controls enforce karna.
5️⃣ Question:
👉 Horizontal aur Vertical Privilege Escalation me kya difference hai?
✅ Answer:
🔹 Horizontal Privilege Escalation – Jab ek user kisi aur user ke resources ko access kar sake.
🔹 Vertical Privilege Escalation – Jab ek user higher privilege (admin) ka access le sake.
✅ Example:
Horizontal: Ek normal employee doosre employee ka payroll data dekh sake.
Vertical: Ek normal user admin panel access kar sake.
6️⃣ Question:
👉 Referer Header Bypass se Access Control kaise break ho sakta hai?
✅ Answer:
Kayi websites Referer header ke basis par access control enforce karti hain. Lekin attacker forged request me fake Referer header daal kar bypass kar sakta hai.
⚡ Example:
Agar ek website /admin/deleteUser ko sirf tab allow kare jab Referer /admin ho, to attacker manually forged request bhejkar access le sakta hai.
✅ Fix:
Referer-based access control use na karein.
Proper authentication aur authorization check enforce karein.
7️⃣ Question:
👉 Kya sirf Obfuscation Access Control enforce karne ke liye sahi hai?
✅ Answer:
❌ Nahi! Obfuscation access control enforce karne ka reliable method nahi hai.
⚡ Example:
Agar admin panel ka URL random aur non-guessable ho (/admin-panel-xyz123), to bhi attacker wordlist ya robots.txt file se isse discover kar sakta hai.
✅ Fix:
Proper authentication aur authorization check implement karein.
Direct admin access ko block karein aur role-based access control enforce karein.
8️⃣ Question:
👉 Access Control vulnerabilities ka prevention kaise hota hai?
✅ Answer:
Access control vulnerabilities ko prevent karne ke liye best security practices follow karni chahiye:
✅ Least Privilege Principle – Har user ko sirf utne permissions mile jitna required hai.
✅ Server-side Authorization Checks – Frontend pe sirf UI controls na ho, backend pe access validation zaroor ho.
✅ RBAC (Role-Based Access Control) – Har user role ke basis par access define karein.
✅ Access Control Testing – Regular penetration testing aur security audits karein.
🎯 Conclusion
Agar aap cybersecurity interview ke liye prepare kar rahe hain, to Access Control aur IDOR vulnerabilities ke concepts, real-world examples aur prevention techniques ache se samajhna zaroori hai.
