Honeypot
Introduction
In this write-up, I will show you how to install and use a program called Pentbox on a Kali Linux device to create a basic honeypot system and test it using a standard web browser to detect an intrusion. 📝🖥️
🏢 Enterprise networks are usually large and complex. The more devices you add to them, the more complexity you add. With the enterprise network, ensuring the highest levels of security is critical. It would be best to update security controls regularly to ensure optimal security. 🔒
A honeypot is a decoy, or a trap, created by organizations to attract hackers into a computer system. 🍯 One of the main objectives of using a honeypot is to monitor the hacker’s exploit of the system’s vulnerabilities. Subsequently, learn the system’s weaknesses and apply the necessary security measures to strengthen it from future attacks. 💪🏾 Another objective is to study the hacker’s methodology. 🎯 The final objective is to divert the hacker’s attention from the main network to the decoy system.
⚠️ Disclaimer
All information, techniques, and tools described in this write-up are for educational purposes only. Use anything in this write-up at your discretion; I cannot be held responsible for any damages caused to any systems or yourselves legally. Using all tools and techniques described in this write-up for attacking individuals or organizations without their prior consent is highly illegal. You must obey all applicable local, state, and federal laws. I assume and accept no liability and will not be responsible for any misuse or damage caused by using the information herein.
🖥️ Lab Setup
- VirtualBox
- Kali Linux
- Windows 10
- Parrot OS
- Pentbox Tool
Download and Install Pentbox on Kali Linux.
GitHub — technicaldada/pentbox: PentBox is a tool that allows us to create honeypot in our system this is written in ruby language.Pentbox is an application that can be configured as a honeypot. Penetration testers mainly use it as it has various tools available. Pentbox is written in Ruby language and installed on multiple operating systems, such as Windows, MacOS, and Linux.Use the following commands in the Kali Linux terminal:git clone https://github.com/technicaldada/pentbox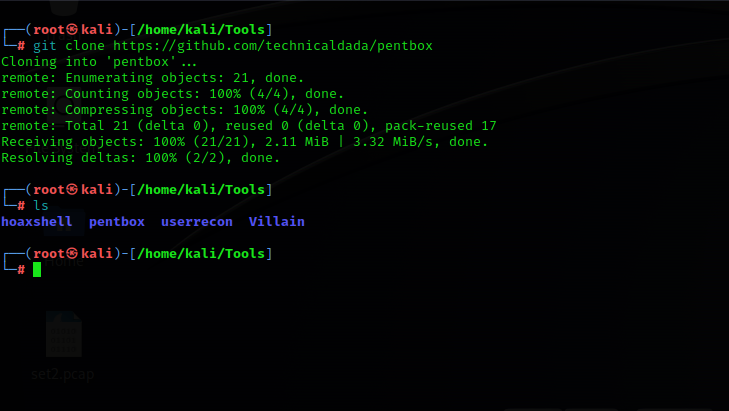
cd pentboxtar -zxvf pentbox.tar.gz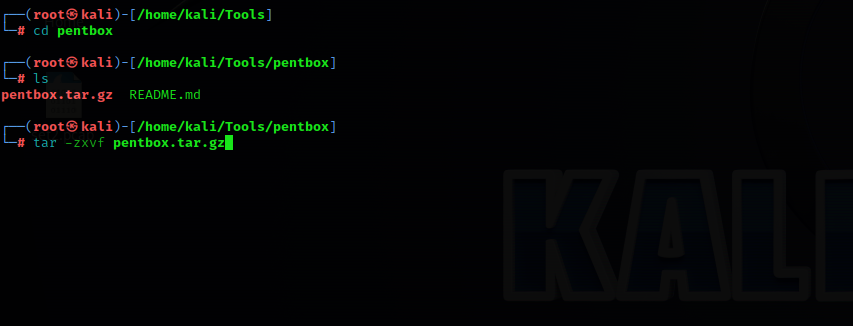
cd pentbox-1.8./pentbox.rb
Set up a Honeypot with Pentbox.
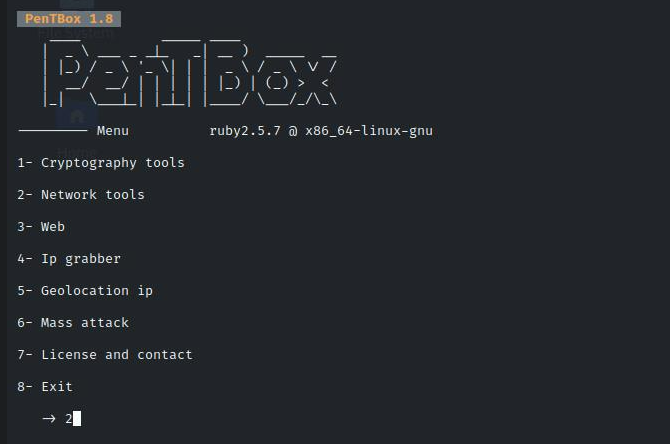
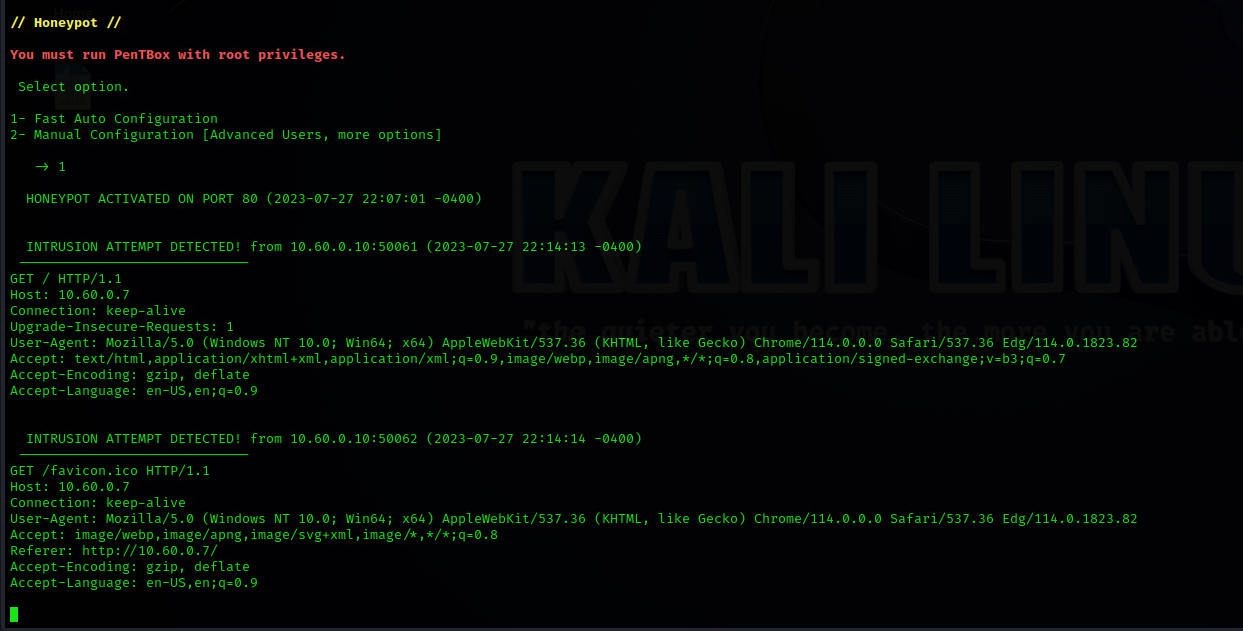
Run the following command to start Pentbox in Kali Linux:./pentbox.rb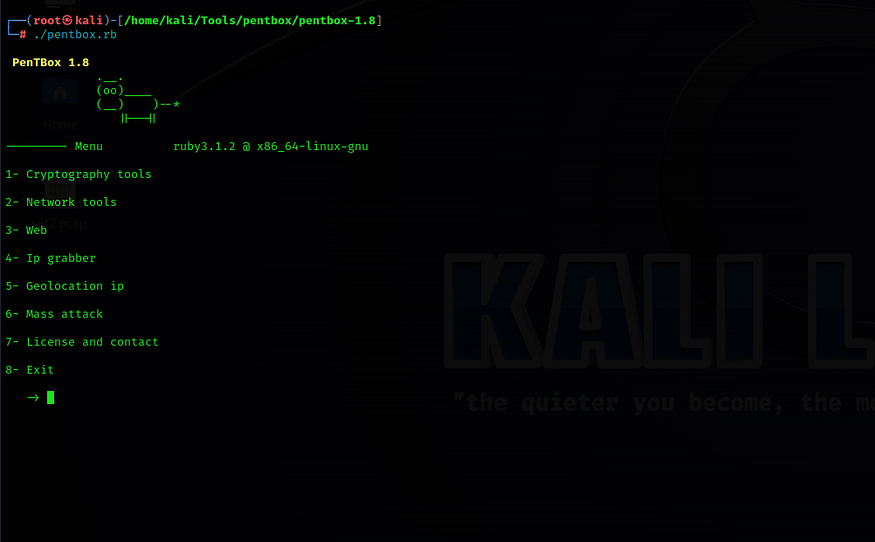
2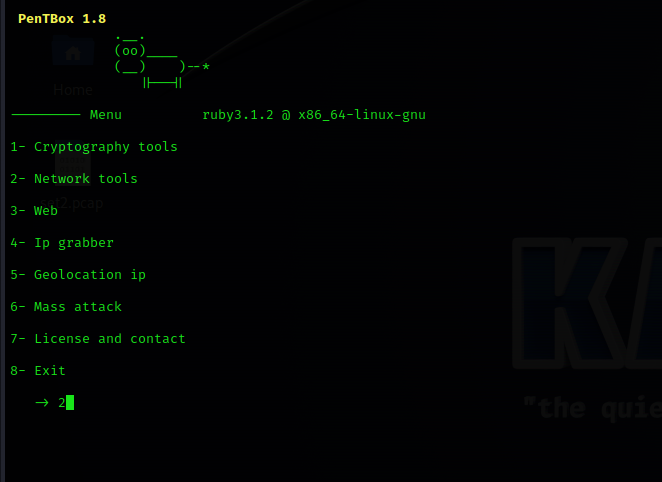
3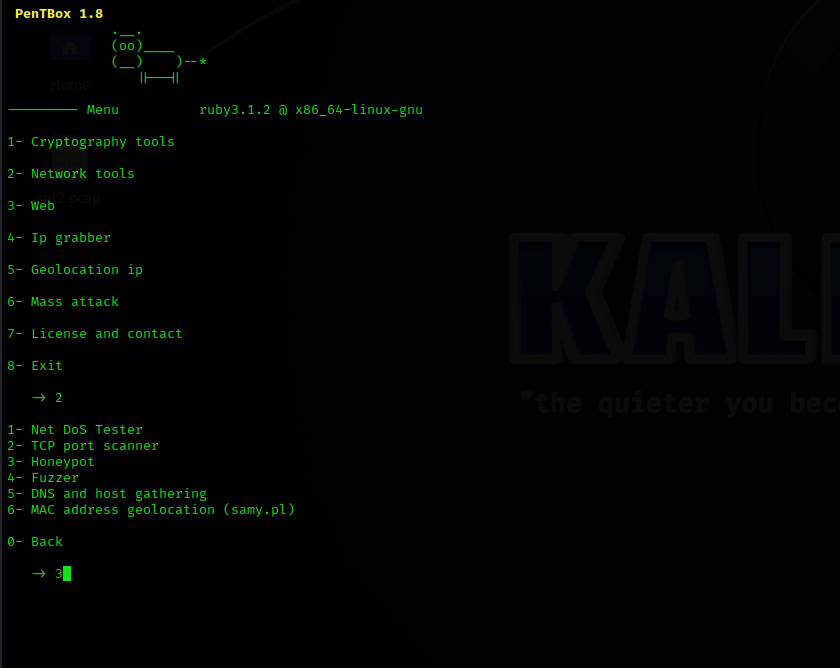
1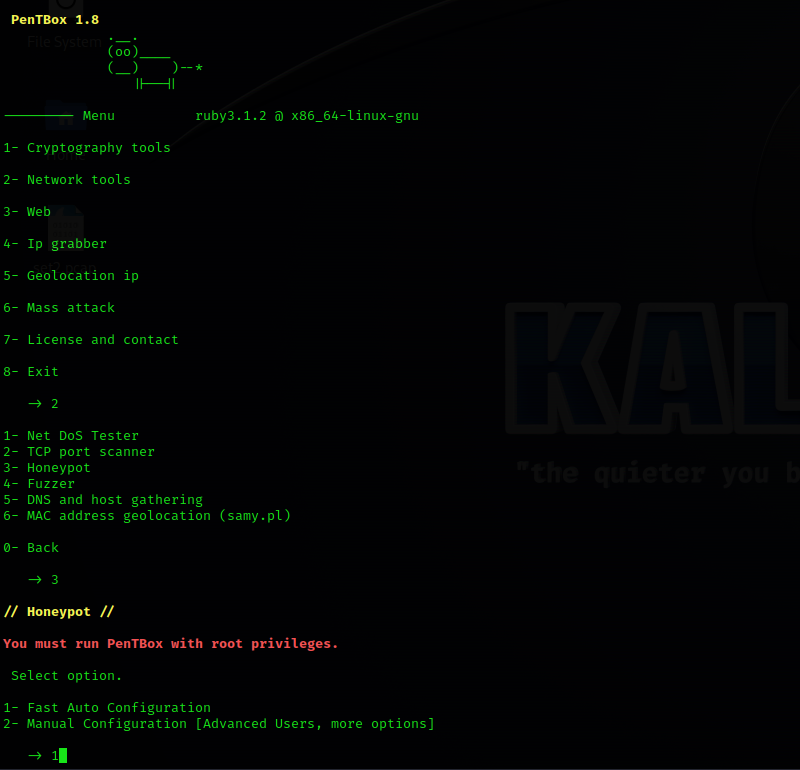
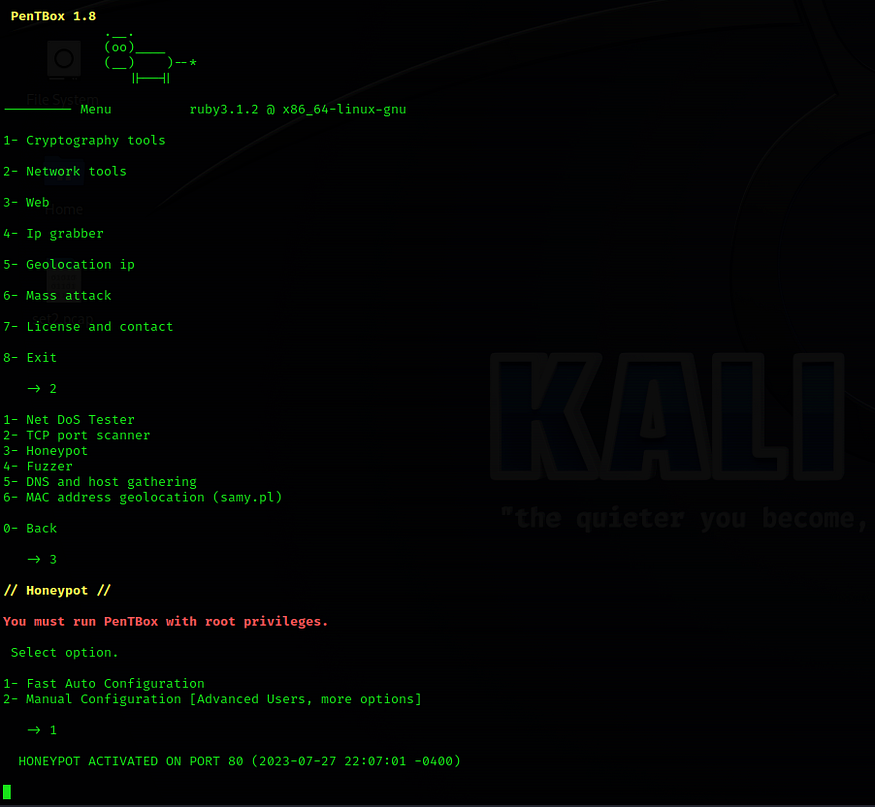
Test Honeypot Fast Auto Configuration Functionality with Windows.
IP Address of Windows 10 machine:10.60.0.10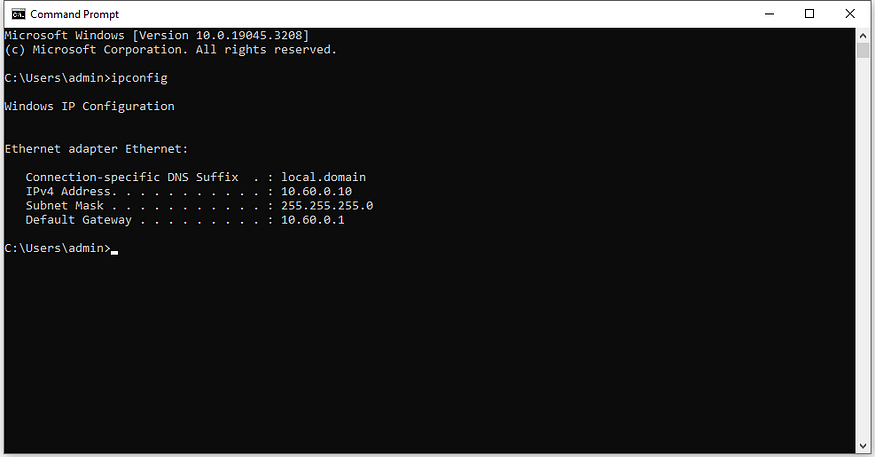
10.60.0.7.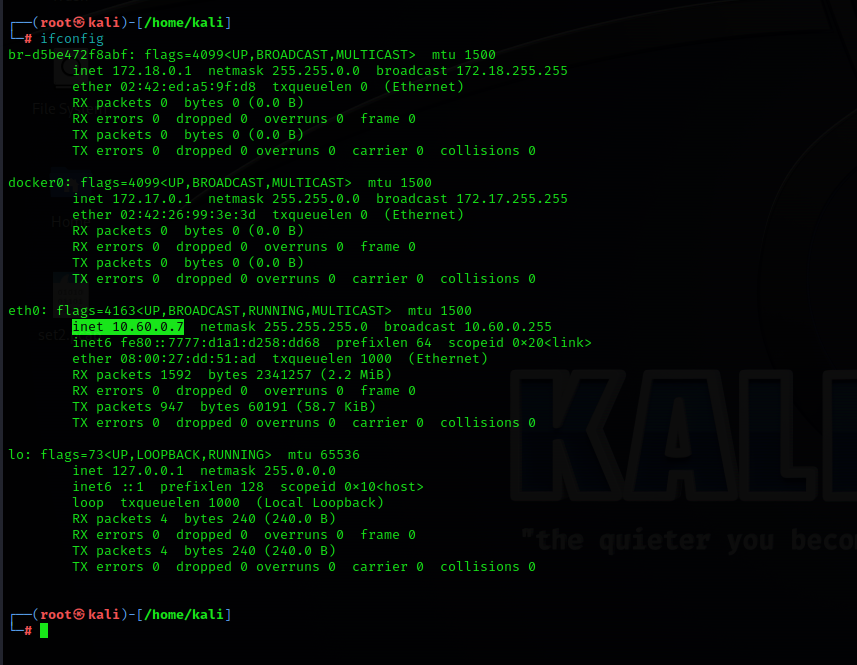
10.60.0.7Press Enter.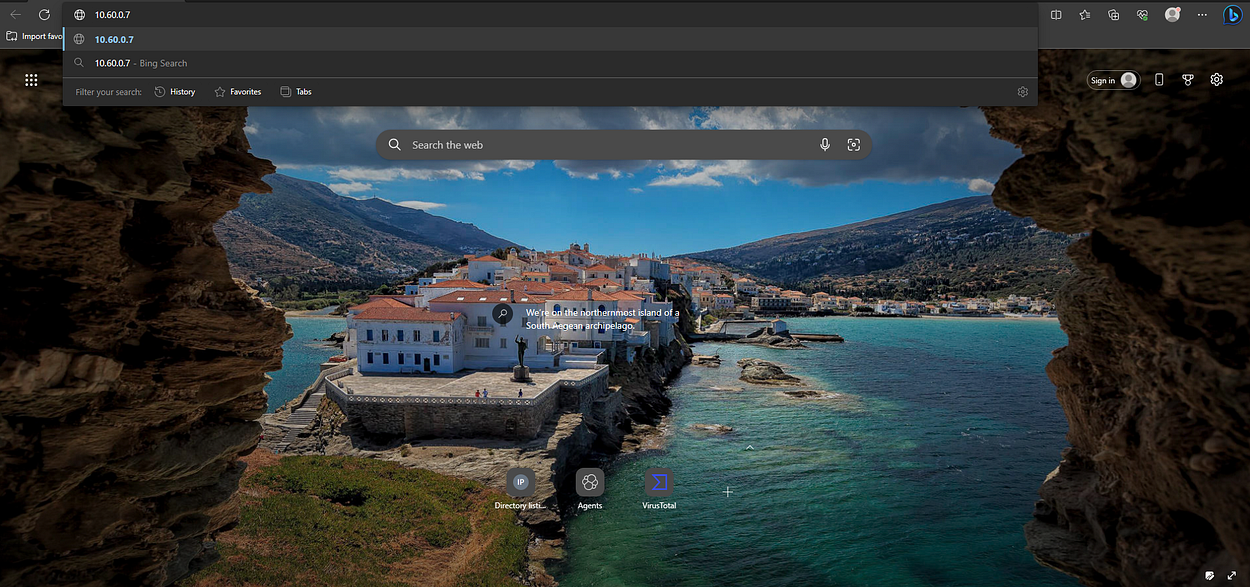
Test Honeypot Manual Configuration Functionality with Parrot.
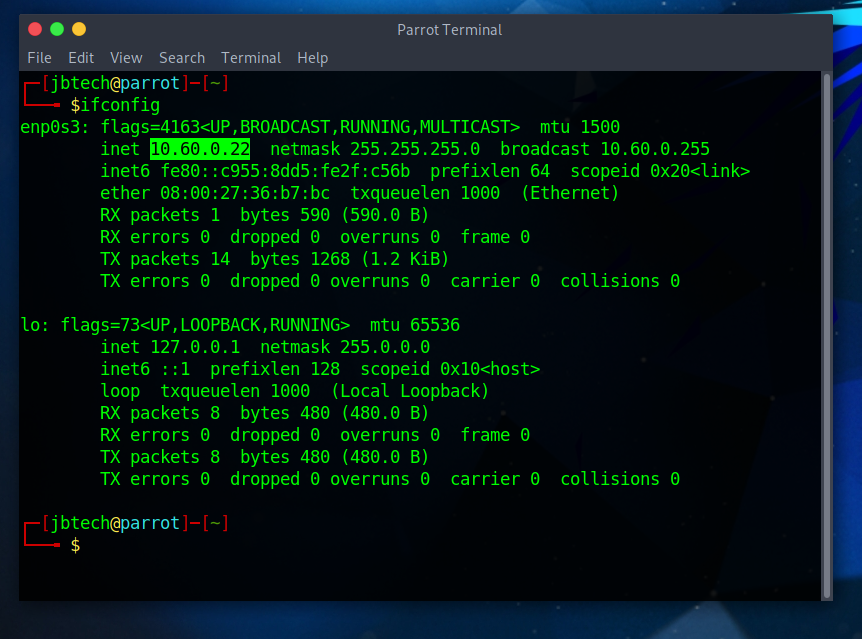
IP Address of Parrot machine:10.60.0.22
./pentbox.rbSelect the network tools section:2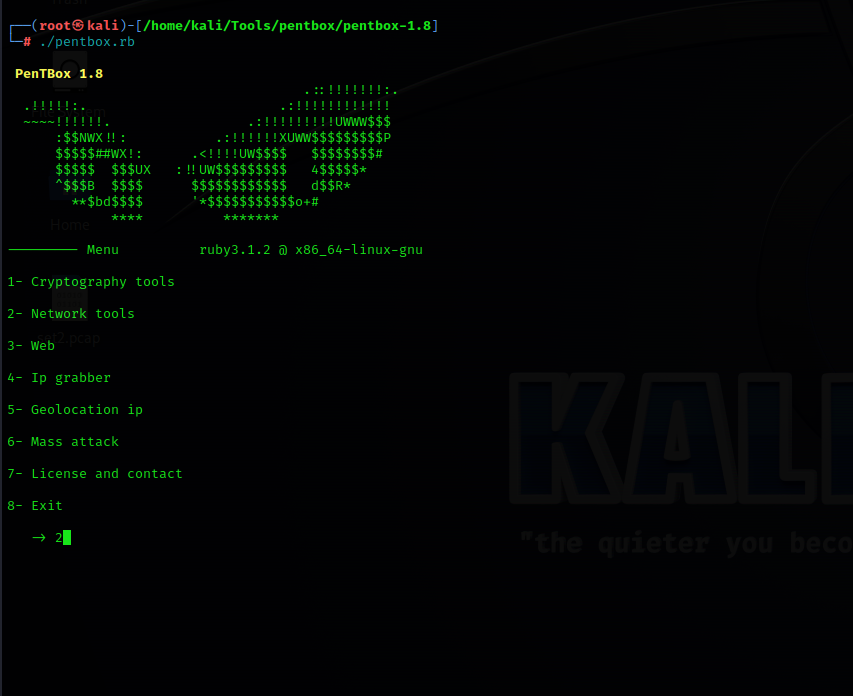
3Then select the Manual Configuration option on the run Pentbox screen by typing:2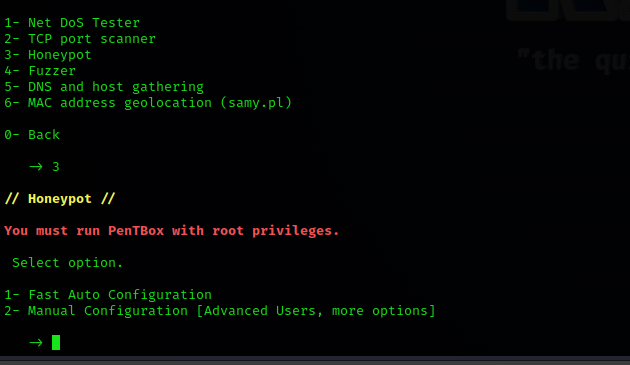
23Insert false message to show:You are not allowed to remotely access my system, so get the hell out of here!Save a log with intrusion?yPress Enter for Default: */pentbox/other/log_honeypot.txt.Activate beep sound?nYou will be notified that the HONEYPOT ACTIVATED ON PORT 23, the Telnet service.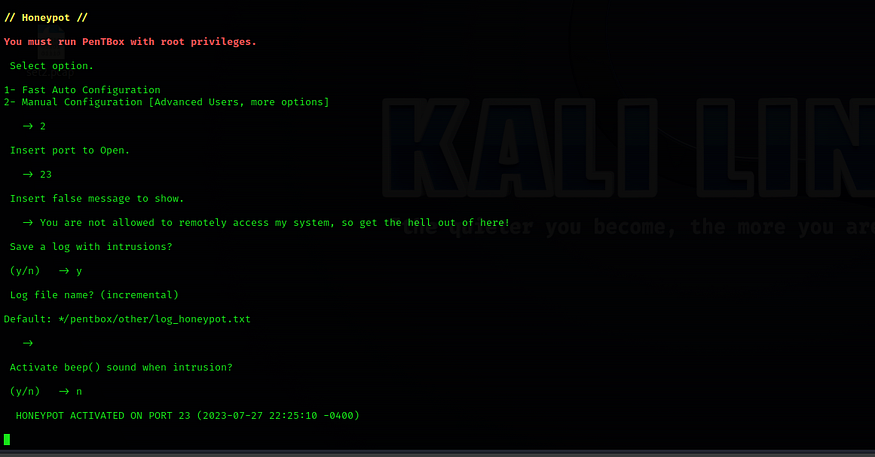
telnet 10.60.0.7 23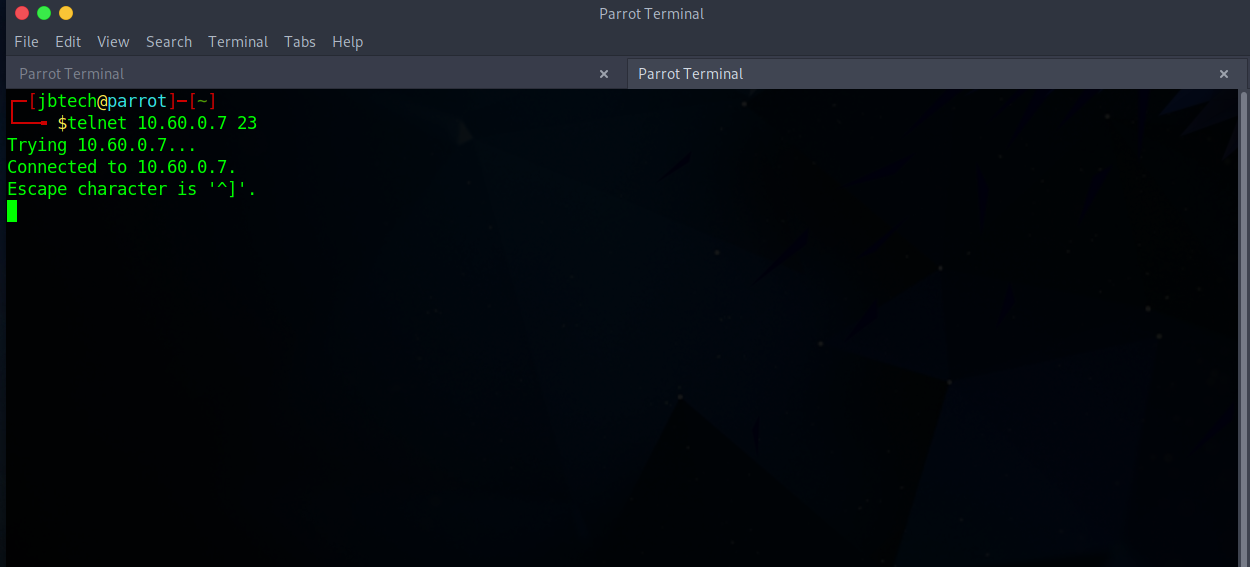
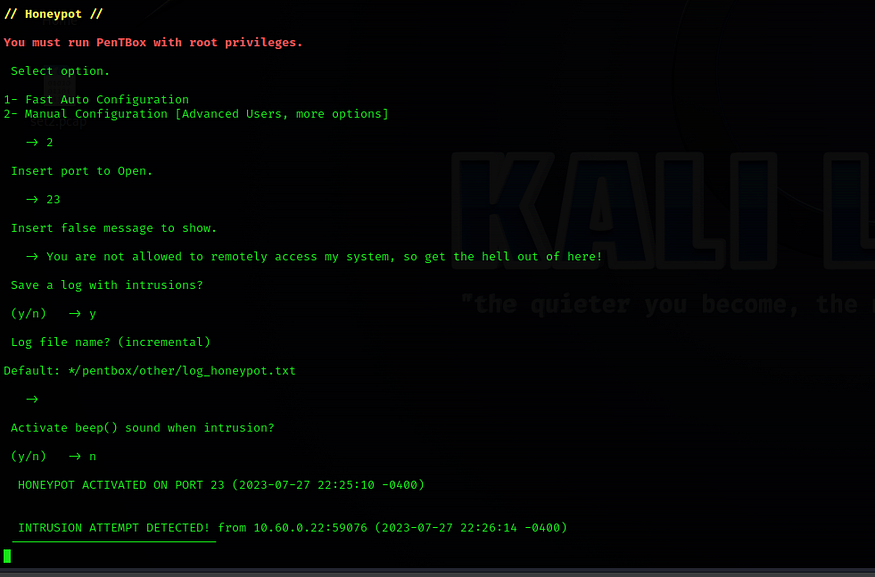
Test Honeypot Manual Configuration False message to show Functionality.
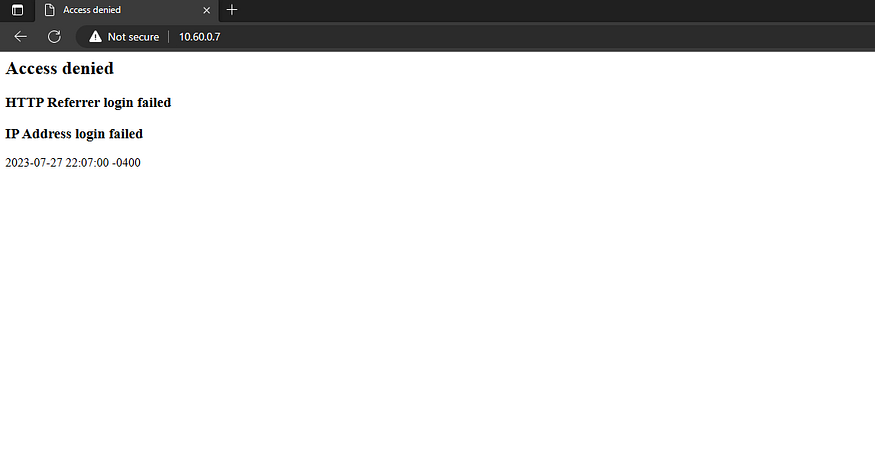
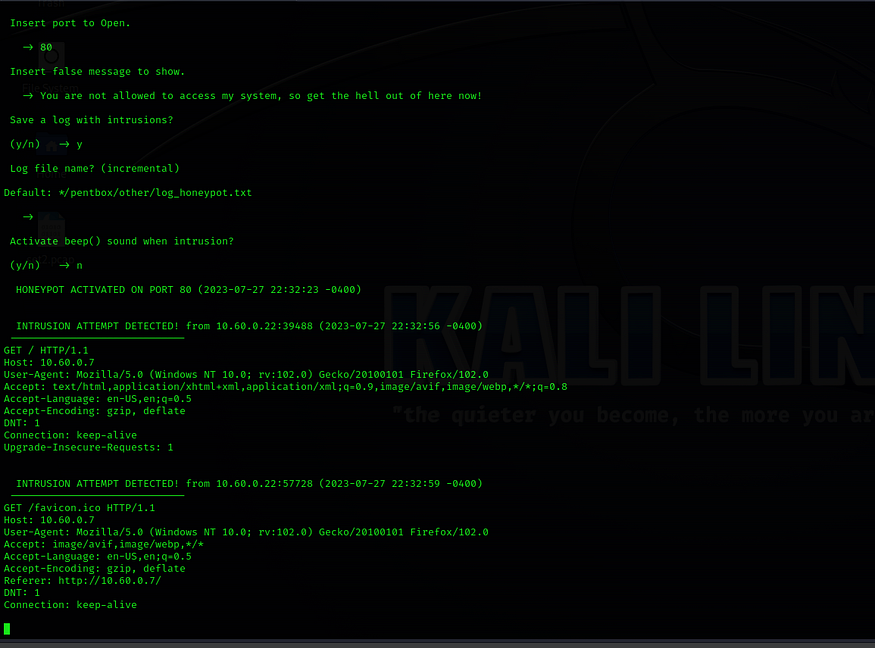
Apply the following manual configuration settings.Port number:80Insert false message to show:You are not allowed to access my system, so get the hell out of here now!Save a log with intrusion?yPress Enter for Default: */pentbox/other/log_honeypot.txt.Activate beep sound?nYou will be notified that the HONEYPOT ACTIVATED ON PORT 80.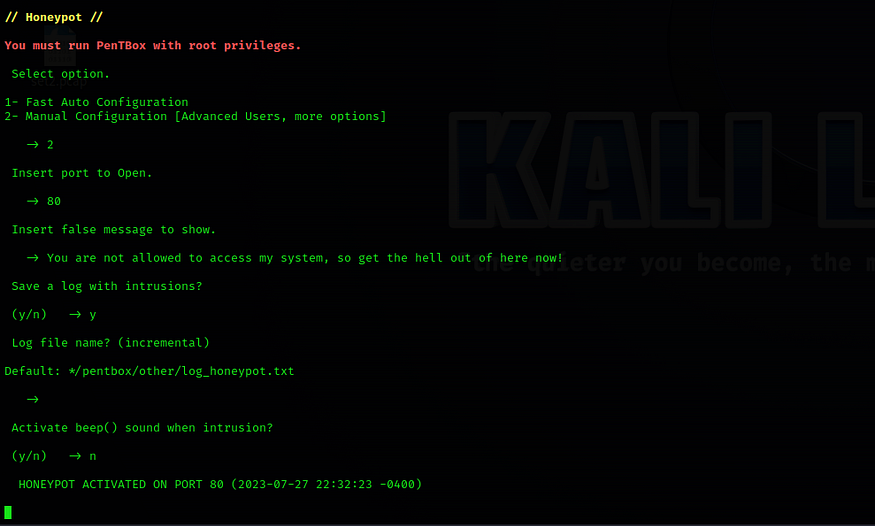
10.60.0.7The previously typed message appears on the web page as the access denied notice.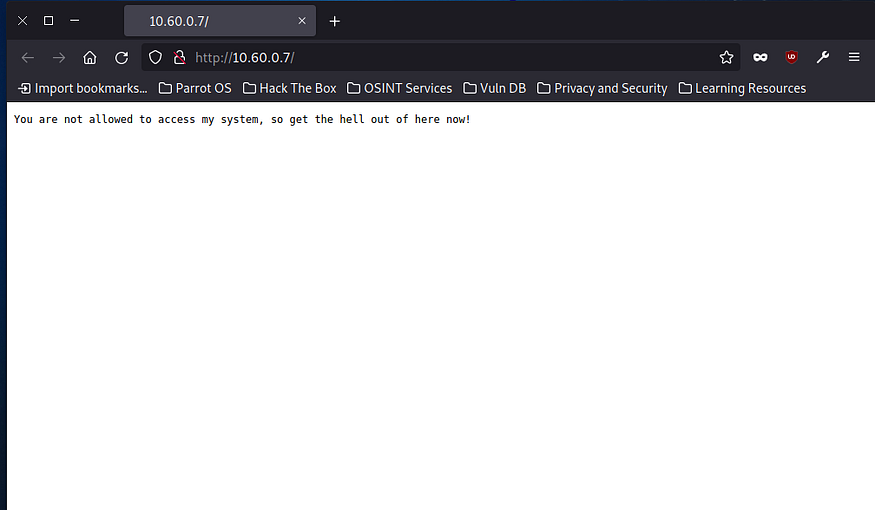
Conclusion
I appreciate you taking the time to read this article. Hopefully, the information presented has been helpful and valuable to you.
If you would like to access more articles, please follow me.
Also, don’t hesitate to leave feedback or suggestions for future topics. Thanks again for your interest and support!
