
OWASP API Security Top 10 2019
- Table of Contents
- About OWAS
- Foreword
- Introduction
- Release Notes
- API Security Risks
- OWASP Top 10 API Security Risks – 2019
- API1:2019 Broken Object Level Authorization
- API2:2019 Broken User Authentication
- API3:2019 Excessive Data Exposure
- API4:2019 Lack of Resources & Rate Limiting
- API5:2019 Broken Function Level Authorization
- API6:2019 – Mass Assignment
- API7:2019 Security Misconfiguration
- API8:2019 Injection
- API9:2019 Improper Assets Management
- API10:2019 Insufficient Logging & Monitoring
- What’s Next For Developers
- What’s Next For DevSecOps
- Methodology and Data
- Acknowledgments
OWASP Ke Baare Mein
OWASP (Open Web Application Security Project) ek open community hai jo organizations ko secure applications aur APIs develop, purchase, aur maintain karne me madad karti hai.
OWASP me aapko yeh sab free aur open milega:
✅ Application security tools aur standards
✅ Application security testing, secure coding, aur code review par complete books
✅ Presentations aur videos
✅ Common security topics par cheat sheets
✅ Standard security controls aur libraries
✅ World me har jagah local chapters
✅ Cutting-edge research
✅ Large-scale security conferences
✅ Mailing lists
🔗 Aur jaanne ke liye: OWASP Official Website
OWASP Ki Philosophy
OWASP ka har tool, document, video, aur presentation free aur open-source hai, taaki koi bhi application security improve kar sake.
Hum application security ko ek people, process, aur technology problem maante hain, kyunki best security solutions in teeno areas me improvement maangti hain.
OWASP kisi bhi technology company se affiliated nahi hai, is wajah se hum unbiased aur practical security information dete hain. Lekin, hum commercial security technology ka informed use support karte hain.
OWASP collaborative, transparent, aur open tarike se materials produce karta hai.
OWASP Foundation
OWASP Foundation ek non-profit organization hai jo is project ki long-term success ensure karti hai.
- Zyada tar log jo OWASP se jude hain, volunteers hain, including board members, chapter leaders, aur project contributors.
- Hum innovative security research ko grants aur infrastructure support dete hain.
Foreword (Pehle Ka Sandesh)
Aaj ke app-driven world me Application Programming Interface (API) innovation ka ek foundational element hai. Chahe banks, retail, transportation, IoT, autonomous vehicles, ya smart cities ho, APIs har jagah critical role play karti hain. Ye mobile, SaaS, aur web applications ka ek essential part hain, jo customer-facing, partner-facing, aur internal applications me use hoti hain.
Lekin, APIs application logic aur sensitive data (jaise Personally Identifiable Information – PII) expose karti hain, is wajah se attackers ke liye APIs ek prime target ban chuki hain. Agar APIs secure na ho, toh rapid innovation impossible ho jata.
Kyun API-Specific Security Ki Zaroorat Hai?
Web applications ke liye ek broader security risks Top 10 list useful hai, lekin APIs ke unique nature ki wajah se API-specific security risks list bhi required hai. API security ka focus strategies aur solutions par hota hai jo unique vulnerabilities aur security risks ko samajhne aur mitigate karne me madad karein.
OWASP API Security Top 10 Ka Structure
Agar aap OWASP Top 10 Project se waqif ho, toh aapko is document me kuch similarities milengi—iska purpose readability aur easy adoption hai. Agar aap naye ho, toh API Security Risks, Methodology, aur Data sections pehle padhna better rahega, phir Top 10 list explore karna.
Aapka Contribution Welcome Hai!
Agar aapke paas questions, comments, ya ideas hain, toh aap in links par contribute kar sakte ho:
🔗 OWASP API Security Issues
🔗 Contributing Guidelines
OWASP API Security Top 10 Ke Links
📌 OWASP API Security Project
📌 GitHub Repository
Shukriya Contributors!
Ye project sabhi contributors ki mehnat se possible hua hai. Aap sabka naam Acknowledgments section me diya gaya hai. Aap sabhi ka dhanyavaad! 🙌
Introduction (Parichay)
🙏 Welcome to the OWASP API Security Top 10 – 2019!
Ye OWASP API Security Top 10 ka pehla edition hai. Agar aap OWASP Top 10 series se familiar ho, toh aapko kuch similarities milengi—iska maksad readability aur easy adoption hai. Agar aap naye ho, toh OWASP API Security Project wiki page pehle explore kar lena better rahega, uske baad aap sabse critical API security risks ko deeply samajh sakte ho.
APIs Ka Role Modern Applications Me
Aaj ke time me APIs modern applications ki architecture ka ek important part hain. Lekin security awareness aur innovation ek hi speed pe nahi badhte, isliye common API security weaknesses pe focus karna zaroori hai.
OWASP API Security Top 10 Ka Main Goal
Iska primary goal API development aur maintenance me involved logon ko educate karna hai, jaise:
👨💻 Developers
🎨 Designers
🏗️ Architects
📋 Managers
🏢 Organizations
Aap Kaise Contribute Kar Sakte Hain?
Agar aapko is pehle edition ki Methodology aur Data ke baare me aur jaana hai, toh uska dedicated section padh sakte ho. Future versions me, hum security industry ko involve karna chahenge aur public data contributions ke liye open call rakhenge.
🚀 Abhi ke liye, agar aapke paas questions, comments, ya ideas hain, toh aap yahan contribute kar sakte hain:
🔗 GitHub Repository
📩 Mailing List
Chaliye, API security aur strong banate hain! 🔐🔥
Release Notes
Ye OWASP API Security Top 10 ka pehla edition hai, jise hum har 3-4 saal me update karne ka plan kar rahe hain.
Future versions me, hum public call for data karenge aur security industry ko involve karenge, taaki ye effort aur strong ho sake. Methodology and Data section me aapko ye version kaise build kiya gaya, uske details milenge. Agar aapko security risks ke baare me aur jaana hai, toh API Security Risks section refer karein.
Pichle kuch saalon me, applications ki architecture kaafi change ho chuki hai. Aaj ke time me APIs microservices, Single Page Applications (SPAs), mobile apps, IoT aur naye architecture models ka ek important part hain.
OWASP API Security Top 10 ka purpose modern API security issues ke liye awareness create karna tha. Ye sab volunteers ki mehnat se possible ho saka, jinka naam Acknowledgments section me diya gaya hai.
API Security Risks (API Suraksha Jhokhim)
OWASP Risk Rating Methodology ka use risk analysis karne ke liye kiya gaya hai.
Risk Score Ki Terminology
| Threat Agents | Exploitability | Weakness Prevalence | Weakness Detectability | Technical Impact | Business Impact |
|---|---|---|---|---|---|
| API Specific | Easy (3) | Widespread (3) | Easy (3) | Severe (3) | Business Specific |
| API Specific | Average (2) | Common (2) | Average (2) | Moderate (2) | Business Specific |
| API Specific | Difficult (1) | Difficult (1) | Difficult (1) | Minor (1) | Business Specific |
⚠️ Note:
- Ye approach threat agent ki likelihood ko consider nahi karti.
- Application-specific technical details bhi include nahi kiye gaye hain.
- Ye rating aapke business pe actual impact ko nahi batati.
- Aapko apni organization ke culture, industry, aur regulatory environment ke hisaab se decide karna padega ki aap kitna security risk accept kar sakte hain.
📌 OWASP API Security Top 10 ka maksad yeh risk analysis aapke liye karna nahi hai, balki aapko proper guidelines dena hai.
References
📖 OWASP Sources:
🔹 OWASP Risk Rating Methodology
🔹 Article on Threat/Risk Modeling
🌍 External Standards:
📌 ISO 31000: Risk Management Standard
📌 ISO 27001: ISMS (Information Security Management System)
📌 NIST Cyber Framework (US)
📌 ASD Strategic Mitigations (AU)
📌 NIST CVSS 3.0
📌 Microsoft Threat Modeling Tool
OWASP Top 10 API Security Risks – 2019 (API Suraksha Ke Top 10 Jhokhim)
| Risk | Description (Vivaran) |
|---|---|
| API1:2019 – Broken Object Level Authorization | APIs object identifiers ko expose karti hain, jo attack surface ko bada deti hain. Object level authorization har function me implement honi chahiye jo user ke input se kisi data source ko access karta hai. |
| API2:2019 – Broken User Authentication | Authentication mechanisms agar galat tarike se implement kiye gaye hain, toh attackers authentication tokens ko compromise kar sakte hain ya flaws ka exploit karke kisi aur user ki identity le sakte hain. Agar system client/user ko sahi se identify nahi kar paata, toh poori API security compromise ho sakti hai. |
| API3:2019 – Excessive Data Exposure | Developers aksar generic implementations me saare object properties expose kar dete hain bina yeh soche ki kaun sa data sensitive hai. Yeh data filtering ka kaam client pe chhod dete hain, jo security risk create kar sakta hai. |
| API4:2019 – Lack of Resources & Rate Limiting | Kai baar APIs me size ya request limits ka koi restriction nahi hota, jiski wajah se API server overload ho sakta hai ya Denial of Service (DoS) attack ka shikar ho sakta hai. Iska authentication flaws jaise brute force attacks se bhi connection ho sakta hai. |
| API5:2019 – Broken Function Level Authorization | Complex access control policies (jisme different hierarchies, groups, aur roles hote hain) agar sahi se define nahi kiye gaye, toh attackers authorization flaws ka exploit karke dusre users ke resources ya administrative functions ko access kar sakte hain. |
| API6:2019 – Mass Assignment | Agar client ka diya hua data (e.g., JSON) bina proper filtering ke directly data models se bind kar diya jaye, toh Mass Assignment attack ho sakta hai. Attackers object properties guess karke, API endpoints explore karke, documentation padhke, ya extra object properties inject karke unauthorized changes kar sakte hain. |
| API7:2019 – Security Misconfiguration | Insecure default configurations, incomplete setups, open cloud storage, misconfigured HTTP headers, unnecessary HTTP methods, permissive CORS settings, aur verbose error messages ki wajah se security misconfigurations hoti hain, jo sensitive data expose kar sakti hain. |
| API8:2019 – Injection | SQL, NoSQL, Command Injection jaise injection flaws tab hote hain jab untrusted data ko interpreter me command ya query ke roop me bhej diya jata hai. Attackers malicious data inject karke unintended commands execute karwa sakte hain ya bina permission ke sensitive data access kar sakte hain. |
| API9:2019 – Improper Asset Management | APIs traditional web applications se zyada endpoints expose karti hain, is wajah se proper aur updated documentation bahut zaroori hai. Deployed API versions aur hosts ka sahi inventory maintain karna deprecated APIs ya debug endpoints ke exposure ko mitigate karne me madad karta hai. |
| API10:2019 – Insufficient Logging & Monitoring | Agar logging aur monitoring proper nahi hai, toh attackers bina detect hue system ko aur exploit kar sakte hain, persistence maintain kar sakte hain, aur zyada systems ko compromise kar sakte hain. Studies dikhati hain ki zyadatar data breaches detect hone me 200+ din lagte hain aur wo bhi internal monitoring ke bajaye external sources dwara detect hote hain. |
🔐 API Security ko strong banane ke liye in risks ko samajhna aur inhe mitigate karna bahut zaroori hai! 🚀
API1:2019 Broken Object Level Authorization
Threat Agents / Attack Vectors
- API Specific: Exploitability 3
- Prevalence: 3 | Detectability: 2
- Impacts: Technical 3 | Business Specific
Explanation
Attackers API ke endpoints ko exploit kar sakte hain jo Broken Object Level Authorization se vulnerable hote hain. Yeh attack object ke ID ko manipulate karke kiya jata hai jo request ke andar send hoti hai. Iska result unauthorized access ho sakta hai, jo sensitive data leak kar sakta hai.
API-based applications me yeh problem common hai kyunki server client ki state ko track nahi karta. Server object IDs jese parameters pe rely karta hai taaki decide kar sake ki user kaunse objects ko access kar sakta hai.
Authorization aur access control mechanisms kaafi complex hote hain. Agar application ek proper authorization infrastructure implement bhi karti hai, to bhi developers authorization checks lagana bhool sakte hain. Automated static ya dynamic testing se access control issues detect karna asaan nahi hota.
Impact
Unauthorized access se data disclosure, data loss, ya data manipulation ho sakti hai. Agar objects ka unauthorized access mil jaye, to full account takeover bhi ho sakta hai.
API Vulnerable Hai Ya Nahi?
Object level authorization ek access control mechanism hai jo code level par implement hota hai. Yeh ensure karta hai ki ek user sirf wahi objects access kare jo uske authorization level me aate hain.
Har API endpoint jo object ID accept karta hai, usko proper authorization checks implement karni chahiye taaki sirf authorized users hi kisi action ko perform kar sakein. Agar authorization checks fail ho jayein, to sensitive data exposed, modify, ya delete ho sakta hai.
Example Attack Scenarios
Scenario #1: E-commerce Store Data Breach
Ek e-commerce platform jo online stores host karta hai, ek page provide karta hai jisme revenue charts dikhte hain.
- Ek attacker browser requests inspect karta hai aur API endpoint ka pattern identify karta hai:
/shops/{shopName}/revenue_data.json
- Dusre API endpoint ka use karke attacker sabhi shop names ka list nikal leta hai.
- Ek simple script likhkar {shopName} ko replace karke thousands of stores ka sales data access kar leta hai.
- Ek attacker browser requests inspect karta hai aur API endpoint ka pattern identify karta hai:
Scenario #2: Wearable Device Account Takeover
Ek attacker wearable device ka network traffic monitor kar raha hai. Usko ek HTTP PATCH request dikhti hai jisme ek custom header hai.
X-User-Id: 54796
- Attacker X-User-Id value ko 54795 se replace karta hai.
- Usko successful HTTP response milta hai, jiska matlab hai ki wo dusre users ke account data modify kar sakta hai.
Prevention (Bachav Ke Tarike)
✅ Authorization mechanism implement karo jo user policies aur hierarchy pe based ho.
✅ Har function me authorization check lagao jo client se aayi request ke basis pe database ka record access karta hai.
✅ Random aur unpredictable values (GUIDs) ko records ke IDs ke liye use karo.
✅ Authorization mechanism ke liye tests likho taaki koi bhi vulnerable change deploy na ho.
References (External)
🔹 CWE-284: Improper Access Control
🔹 CWE-285: Improper Authorization
🔹 CWE-639: Authorization Bypass Through User-Controlled Key
API Security Kya Hai?
Aaj ke app-driven world me innovation ka ek basic element API (Application Programming Interface) hai. Chahe wo banking ho, retail, transportation, IoT, autonomous vehicles ya smart cities, APIs har jagah kaam aati hain. Yeh modern mobile, SaaS, aur web applications ka ek critical part hain, jo customer-facing, partner-facing aur internal applications me use hoti hain.
API ka kaam application logic aur sensitive data (jaise ki PII – Personally Identifiable Information) ko expose karna hota hai. Isi wajah se APIs hackers ke liye ek bada target ban chuki hain. Agar APIs secure na ho, toh rapid innovation impossible ho jata hai.
API Security ka focus un strategies aur solutions par hota hai jo API ki unique vulnerabilities aur security risks ko samajhne aur mitigate karne me madad karti hain.
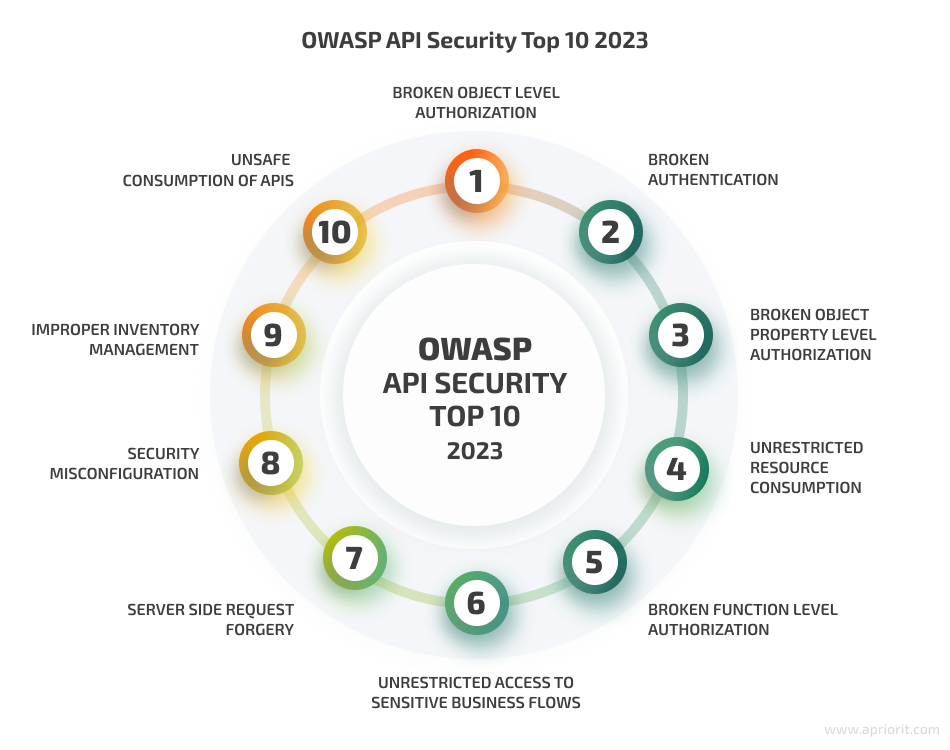
API Security Top 10 (2023)
API1:2023 – Broken Object Level Authorization
APIs endpoints expose karte hain jo object identifiers ko handle karte hain. Is wajah se Object Level Access Control ka bada attack surface banta hai. Har function jo kisi data source ko user ke ID ke through access karta hai, usme object level authorization check hona chahiye.
API2:2023 – Broken Authentication
Agar authentication mechanisms sahi se implement na ho, toh attackers authentication tokens ko compromise kar sakte hain ya flaws ka use karke kisi aur user ka identity assume kar sakte hain. Agar system client/user ko sahi se identify na kar paye, toh overall API security khatre me pad jati hai.
API3:2023 – Broken Object Property Level Authorization
Ye issue API3:2019 (Excessive Data Exposure) aur API6:2019 (Mass Assignment) ka combination hai. Iska root cause improper authorization validation hota hai, jo sensitive information ko expose kar sakta hai ya unauthorized parties ko data manipulate karne ka mauka de sakta hai.
API4:2023 – Unrestricted Resource Consumption
API requests ko process karne ke liye network bandwidth, CPU, memory, aur storage resources chahiye hote hain. Kabhi-kabhi APIs ke through email/SMS/calls ya biometrics validation bhi hoti hai, jo per request charge hoti hai. Agar attacker is vulnerability ka fayda uthaye, toh Denial of Service (DoS) attack ho sakta hai ya operational cost badh sakti hai.
API5:2023 – Broken Function Level Authorization
Agar APIs me access control policies complex ho (jaise ki different hierarchies, groups, aur roles), toh authorization flaws aa sakti hain. Attackers is vulnerability ka use karke doosre users ke resources ya administrative functions ka access le sakte hain.
API6:2023 – Unrestricted Access to Sensitive Business Flows
Kuch APIs aise business flows expose karti hain jo kisi bhi business ke liye critical hote hain (jaise ki ticket book karna ya comment post karna). Agar in functionalities par sahi se security implement na ho, toh attackers automated tareeke se business ko nuksan pahucha sakte hain.
API7:2023 – Server-Side Request Forgery (SSRF)
Agar API bina validation ke kisi remote resource ko fetch karti hai, toh SSRF vulnerability ho sakti hai. Iska fayda uthakar attacker API ko kisi unexpected destination par request bhejne ke liye force kar sakta hai, chahe woh firewall ya VPN ke peeche ho.
API8:2023 – Security Misconfiguration
APIs aur unke supporting systems me kayi complex configurations hoti hain. Agar DevOps engineers security best practices ko na follow karein, toh APIs attack ke liye vulnerable ho sakti hain.
API9:2023 – Improper Inventory Management
APIs me traditional web applications se zyada endpoints hote hain. Is wajah se proper aur updated documentation zaroori hoti hai. Agar API versions aur exposed debug endpoints ka dhyan na rakha jaye, toh attackers outdated versions ka misuse kar sakte hain.
API10:2023 – Unsafe Consumption of APIs
Developers third-party APIs se received data par user input ke comparison me zyada trust karte hain, jo security vulnerabilities create kar sakta hai. Attackers directly target API ko hack karne ke bajaye, uske third-party integrations ko attack kar sakte hain.
API Security Top 10 (2023) OWASP ne release kiya tha, jo batata hai ki APIs ko hack hone se kaise bachaya jaye. Isko aise samajhte hain ki ek school hai, jisme alag-alag darwaze (API endpoints) hain. Agar security tight nahi hai, to koi bhi andar ghus sakta hai.
1. Broken Object Level Authorization (BOLA)
💡 Problem:
API properly check nahi karti ki jo user request kar raha hai, uska permission hai bhi ya nahi.
Attacker dusre users ke private data access kar sakta hai.
🔍 Example (Real-Life Scenario):
Maan lo ki ek medical app hai jo patient ka data store karti hai. API request aise hai:
GET /patients/1001/record
Ab agar attacker ID change karke dusre patient ka data access kar le:
GET /patients/1002/record
Aur API authorization check na kare, to attacker kisi bhi patient ka private medical record dekh sakta hai! 😱
✅ Solution:
API me user authentication aur authorization check karo.
Object ID access control lagao (e.g., JWT tokens ya session-based checks).
Least privilege principle follow karo.
2. Broken Authentication
💡 Problem:
Agar authentication weak ho to attacker bina password ke bhi login kar sakta hai.
Iska phishing, brute force attack, session hijacking jese attacks me use hota hai.
🔍 Example:
Maan lo ek login API hai:
POST /login{
"username": "admin",
"password": "password123"
}
Agar password guessable hai ya brute force attack allowed hai, to hacker easily access le sakta hai. Ya agar JWT token expire nahi ho raha aur koi old token use kar sakta hai, to attacker usse bhi login kar sakta hai.
✅ Solution:
Strong password policies rakho (minimum 12 characters, uppercase, lowercase, numbers, special chars).
MFA (Multi-Factor Authentication) implement karo.
Rate-limiting aur CAPTCHA lagao taaki brute force attack na ho.
Session expiration aur token revocation implement karo.
3. Broken Object Property Level Authorization (BOPLA)
💡 Problem:
Koi bhi extra sensitive fields modify ya access kar sakta hai jo API me exposed hai.
🔍 Example:
Maan lo ek API me user profile update hota hai:
PUT /update-profile
{
"name": "Ravi",
"email": "ravi@example.com",
"role": "admin"
}
Agar user manually “role”: “admin” set kar de aur API isko validate na kare, to ek normal user admin ban sakta hai! 😨
✅ Solution:
API response me sirf authorized fields hi bhejo.
Backend me validate karo ki user sirf apne data ko modify kar sakta hai.
Role-based access control (RBAC) implement karo.
4. Unrestricted Resource Consumption
💡 Problem:
Agar API limit nahi karti ki ek user kitni baar request bhej sakta hai, to attacker DDoS attack kar sakta hai aur server crash ho sakta hai.
🔍 Example:
Maan lo ek API data fetch karti hai:
GET /fetch-heavy-data
Agar koi bot baar-baar request bheje bina limit ke, to server overloaded ho jayega aur slow ya crash ho sakta hai.
✅ Solution:
Rate limiting (e.g., 100 requests per minute per user) implement karo.
API quota aur resource consumption limits rakho.
Web Application Firewall (WAF) use karo taaki bots ko block kiya ja sake.
5. Broken Function Level Authorization
💡 Problem:
Koi bhi unauthorized function access kar sakta hai jo sirf admin ya specific users ke liye hona chahiye.
🔍 Example:
Ek normal user ke paas ek API call ka access hai:
DELETE /user/delete/102
Agar API proper role checking na kare, to koi bhi kisi bhi user ka account delete kar sakta hai. 😱
✅ Solution:
Role-Based Access Control (RBAC) lagao.
Least privilege principle follow karo (jo jitna kaam karega, utni hi access mile).
Endpoints ko authenticate aur authorize karo.
6. Unrestricted Access to Sensitive Business Flows
💡 Problem:
Agar API business logic ka protection nahi karti, to attacker business rules ka bypass karke financial ya logical advantage le sakta hai.
🔍 Example:
Maan lo ek shopping app hai jisme coupon apply hota hai:
POST /apply-coupon?code=FREE100
Agar attacker ye API baar-baar use kare bina limit ke, to wo unlimited free items le sakta hai!
✅ Solution:
Coupon ya discount codes me limit lagao.
Business logic security check karo (e.g., ek user ek hi baar free coupon use kare).
API ke abuse ko detect karne ke liye logging aur monitoring karo.
7. Server-Side Request Forgery (SSRF)
💡 Problem:
Agar API bina validation ke kisi bhi external/internal URL ko call kar sake, to attacker internal network access le sakta hai.
🔍 Example:
Ek API request me URL diya jata hai:
POST /fetch-data{
"url": "http://localhost/admin"
}
Agar attacker is URL ko modify karke internal services ko access kar le, to wo sensitive data nikal sakta hai.
✅ Solution:
External URL filtering aur allowlist use karo.
Internal IPs aur private endpoints ko block karo.
8. Security Misconfiguration
💡 Problem:
Agar API ka default debug mode enable hai ya extra data expose ho raha hai, to hacker easily exploit kar sakta hai.
🔍 Example:
Agar API error messages me internal details show ho rahe hain, jaise:
{
"error": "Database connection failed. Username: admin, Password: 12345"
}
To attacker is data ka misuse karke database hack kar sakta hai! 😨
✅ Solution:
Debug mode disable rakho.
Environment variables aur secret keys ko secure rakho.
Security headers implement karo.
9. Improper Inventory Management
💡 Problem:
Agar old APIs expose ho rahi hain jo deprecated ya unsecured hain, to hacker unka misuse kar sakta hai.
🔍 Example:
Agar ek old API api-v1 ab bhi active hai aur authentication ke bina access ho rahi hai, to attacker usko hack karke sensitive data nikal sakta hai.
✅ Solution:
Old APIs ko remove ya secure karo.
API inventory maintain karo aur regular audits karo.
10. Unsafe Consumption of APIs
💡 Problem:
Agar third-party APIs bina verify kiye use ki ja rahi hain, to security risk badh jata hai.
🔍 Example:
Agar ek third-party API compromised hai, aur tum uska data bina verify kiye use kar rahe ho, to malware ya malicious data system me aa sakta hai.
✅ Solution:
Third-party APIs ka review karo aur security check lagao.
Data validation aur sanitization implement karo.
🔥 Conclusion:
API security must hai! Har ek endpoint secure hona chahiye, authentication proper hona chahiye, aur rate-limiting aur authorization implement honi chahiye. 🚀
