Code-Based SSTI Detection
Code context me SSTI vulnerabilities detect karne ke liye, testers specially crafted payloads ka use karte hain jo ya toh server se error message retrieve kar sakein ya phir blank response generate karein.
Basic SSTI Testing Example
Agar ek application HTTP request me personal_greeting variable use kar rahi hai, toh tester is variable me SSTI payload inject karke response analyze kar sakta hai.
Normal Request:
GET /?personal_greeting=username HTTP/1.1 Host: victim-website.comResponse:
Hello user01HTML Tag Injection Test:
GET /?personal_greeting=username}}<tag> HTTP/1.1 Host: victim-website.comResponse:
Hello user01 <tag>Agar response me HTML tag inject ho raha hai, toh iska matlab hai ki input properly sanitized nahi hai, aur further testing se SSTI vulnerability confirm ki ja sakti hai.
Identifying the Template Engine
Jab injection point detect ho jaye, tab alag-alag template engines ke specific expressions ka use karke yeh confirm kiya jata hai ki backend kis template engine ka use kar raha hai.
Malicious Payload Injection
Testers malicious ya malformed payload inject karke yeh check karte hain ki server ka behavior kya hota hai. Agar server error message return kare jo template engine ka indication de, toh vulnerability confirm ho sakti hai.
Example Payload:
Possible Response (If Vulnerable):
Agar server ka response me error message template engine ka naam ya syntax error show karta hai, toh application SSTI vulnerable ho sakti hai.
Template Engine Identify Karna
Jab testers template injection detect kar lete hain, toh unhe yeh identify karna hota hai ki kaunsa template engine use ho raha hai. Yeh step simple ho sakta hai, jisme tester ek invalid syntax submit karta hai jo error message me template engine ka naam reveal kar sakta hai. Lekin kuch cases me, yeh technique kaam nahi karti kyunki error messages suppress ho sakte hain. Yeh automation ke liye bhi suitable nahi hoti.
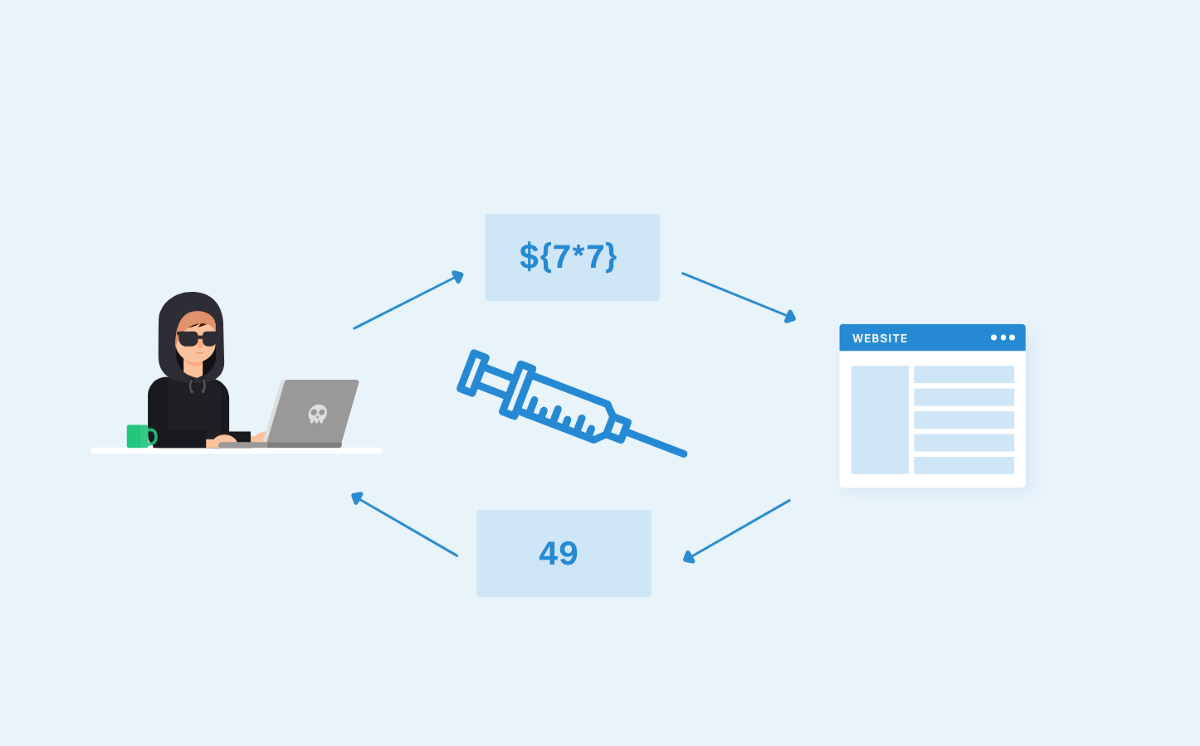
Dusre tareeke se, testers Burp Suite me decision tree ka use karke identification automate kar sakte hain. Yeh tree language-specific payloads ko map karta hai, jisme red arrows failure aur green arrows success indicate karte hain. Kabhi-kabhi ek payload multiple successful responses generate kar sakta hai, jaise {{7*’7’}} ka result Jinja2 me 7777777 aur Twig me 49 hota hai.