Network Penetration Testing – VAPT
Vulnerability Assessment and Penetration Testing (VAPT) ek broad term hai jo alag-alag tarah ki security assessment services ko refer karta hai. Inka main goal hota hai organization ke IT infrastructure mein cyber security risks ko identify karna aur unko kam karna.
Yeh samajhna bahut important hai ki VAPT ke different types kya hain aur unke beech kya differences hote hain, taaki aap apne company ke needs ke hisaab se sahi assessment choose kar paayen.
Kyuki VAPT assessments depth, breadth, scope, aur price ke mamle mein kaafi alag hote hain, isliye yeh knowledge zaroori hai taaki testing se aapko best value for money mil sake.
Network Penetration Testing ek specific process hai jisme security experts actively network ke vulnerabilities ko exploit karte hain jaise ki hackers karte, lekin controlled environment mein. Iska main goal hota hai weaknesses ko dhoondhna aur samajhna ki unka real-world impact kya ho sakta hai.
VAPT ka full form hai Vulnerability Assessment and Penetration Testing. Ye ek broader process hai jo do phases mein divide hota hai:
Vulnerability Assessment (VA): Is phase mein network ko scan karke vulnerabilities ko identify kiya jata hai jaise outdated software, misconfigurations, aur missing patches. Yahan sirf vulnerabilities find ki jaati hain, unko exploit nahi kiya jata.
Penetration Testing (PT): Is phase mein identified vulnerabilities ko actively exploit karke dekha jata hai ki unse kitna bada risk hai.
Simple words mein, Penetration Testing VAPT ka ek hissa hai. VAPT complete testing cycle cover karta hai — pehle vulnerabilities ko identify karna (VA), fir unko exploit karke unka asar dekhna (PT).
Dono ka aim hota hai organization ke network ko secure karna before real hackers koi attack karen. Regular VAPT karwana companies ke liye important hai compliance, data protection, aur trust maintain karne ke liye.
What is Vulnerability Assessment and Penetration Testing?
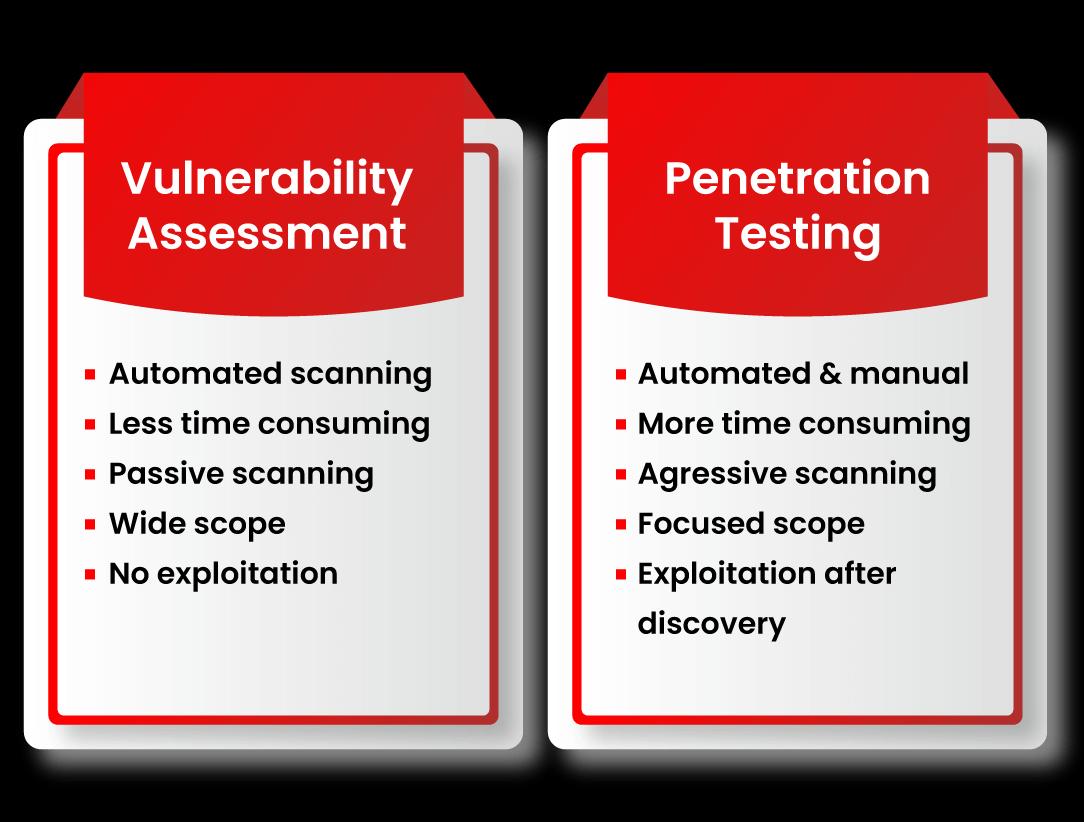
Vulnerability Assessment (VA) aur Penetration Testing (PT) dono methods hain jo systems, networks, ya online applications ke flaws detect karne ke liye use hote hain. Lekin, dono mein kuch important differences hote hain.
Vulnerability Assessment (VA)
Vulnerability Assessment ka kaam hota hai system ke known vulnerabilities ko examine, discover, aur report karna.
VA ek detailed report generate karta hai jisme vulnerabilities ka categorization aur unki priority mention hoti hai — jaise kaunsi vulnerability zyada dangerous hai aur kaunsi kam.
Agar aap apna career VAPT mein grow karna chahte ho aur professional banna chahte ho, to aapko “VAPT Training” course join karna chahiye. Ye course aapko is field mein excellence achieve karne mein madad karega.
Penetration Testing (PT)
Dusri taraf, Penetration Testing ka goal hota hai vulnerabilities ka exploit karna taaki pata chale ki ek attacker kitni door tak jaa sakta hai.
Ye system ki defense level ko test karta hai.
Agar simple example dein, to VA ek darwaze ke paas jaake uska inspection karna hai — jaise ki dekhna lock weak hai ya nahi. Jabki PT mein actually try kiya jata hai darwaza todne ya unlock karne ki, dekhne ke liye ki andar ghusna kitna aasan ya mushkil hai.
Generally, VA mostly automated hota hai, jabki PT ek security expert manually perform karta hai.
What is VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) ek tarah ka security testing process hai jisme applications, networks, endpoints, ya cloud infrastructure mein flaws detect kiye jaate hain.
Vulnerability Assessment aur Penetration Testing dono ke alag-alag advantages hote hain, aur usually in dono ko combine karke ek comprehensive security analysis banaya jaata hai.
What is the purpose of VAPT?
Kyuki hackers ke tools, techniques aur methods din-ba-din advance ho rahe hain, isiliye kisi bhi organization ke cyber security ka frequently assess karna zaroori hota hai.
VAPT aapki organization ko secure banane mein help karta hai by providing insights about security flaws aur unko fix karne ke solutions batakar.
Jo organizations GDPR, ISO 27001, aur PCI DSS jaise standards ko comply karna chahti hain, unke liye VAPT ab aur bhi zyada important ban gaya hai.
What are the deliverables from a VAPT?
VAPT ke dauraan, defined scope ke according network devices, security devices, servers, applications, websites, aur other systems ka assessment kiya jaata hai.
Iske saath-saath vulnerabilities ka analysis aur unko fix karne ke suggestions bhi diye jaate hain.
VAPT Activity ke Deliverables mein hota hai:
Critical vulnerabilities ka closure verify karna.
Ensure karna ki saari findings properly close hui hain.
Pehle ek draft VAPT report milti hai, fir final report di jaati hai.
(Optional) Compliance verification bhi ki ja sakti hai.
VAPT Report mein kya-kya included hota hai:
Auditee ka address aur contact information.
VAPT ka schedule aur locations.
Terms and conditions.
Testing confirmation as per International Best Practices aur OWASP Web/Mobile Security Guidelines.
Vulnerabilities aur related issues ka detailed analysis.
Problems ko resolve karne ke recommendations.
Audit mein participate karne wale personnel ka detail.
What are the benefits of performing VAPT?
VAPT aapko aapke application ka ek thorough (poora detailed) assessment provide karta hai.
Yeh aapko security flaws ya faults identify karne mein madad karta hai jo kisi major cyber-attack ka reason ban sakte hain.
VAPT se aapko apne network ya application ke dangers ka ek complete picture milta hai.
Yeh businesses ko apne data aur systems ko harmful attacks se defend karne mein help karta hai.
Compliance standards jaise GDPR, ISO 27001, PCI DSS, etc. mein VAPT karna zaroori hota hai.
VAPT aapke company ko data loss aur unauthorized access ke against protect karta hai.
Yeh aapko external (baahar ke) aur internal (andar ke) dono types ke threats se apne data ko secure karne mein madad karta hai.
How to Evaluate Vulnerability?
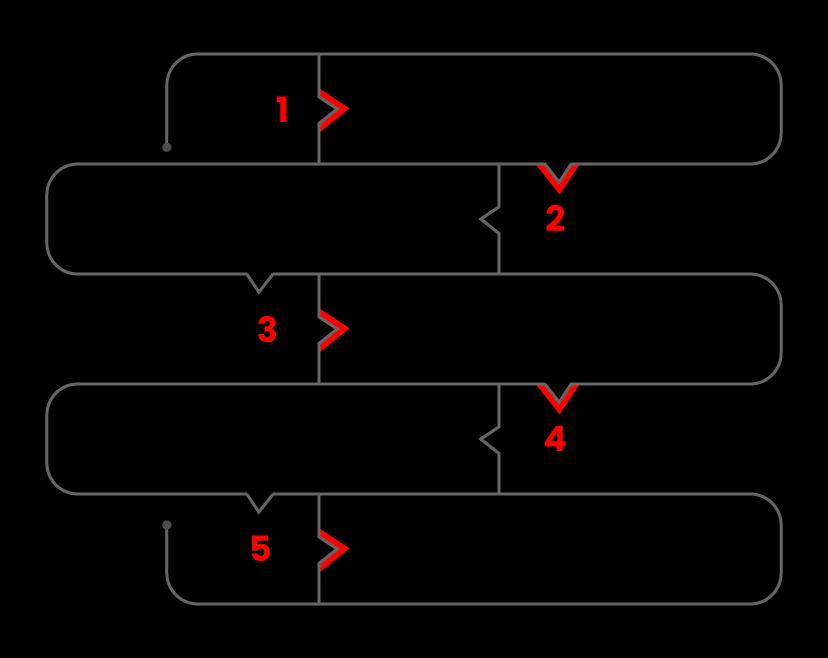
Neeche diya gaya hai ek step-by-step guide jo aapko vulnerability assessment karne mein madad karega:

Step 1: Set up
Documentation process shuru karo.
Permissions secure karo.
Step 2: Tool Setup
Test Execute Karna:
Tools ko execute karo.
Apne jo data packet save kiya tha, usko run karo.
(Ek packet ek data unit hota hai jo origin se destination tak route hota hai.) Jab koi file internet pe transfer hoti hai, jaise email message, HTML file, ya URL request, TCP layer isse multiple “chunks” mein todta hai taaki efficiently route kiya ja sake. Har chunk ko unique number diya jaata hai aur destination ka Internet address hota hai. Jab assessment tools chal rahe hote hain, toh receiving end pe TCP layer packets ko reassemble karke original file banata hai.
Step 3: Vulnerability Analysis
Network aur system resources ko identify aur categorize karo.
Resources ko prioritize karo (Jaise High, Medium, Low).
Har resource ko jo danger ho sakta hai, usko identify karo.
Sabse pehle urgent issues ko tackle karne ke liye strategy banaye.
Attack ka impact kam karne ke liye strategies define karo aur implement karo.
Step 4: Reporting
Step 5: Remediation
Flaws ko repair karne ka process.
Har vulnerability ko test kiya gaya tha.
What is a VAPT Tool, exactly?
VAPT tool ek VA (Vulnerability Assessment) perform karta hai vulnerabilities detect karne ke liye aur PT (Penetration Testing) karta hai access gain karne ke liye un flaws ko exploit karke. Ek VA, jaise, poor encryption ko detect karne mein madad kar sakta hai, lekin PT usko decode karne ki koshish karega. VAPT tools vulnerabilities scan karte hain, PA (Penetration Analysis) report banate hain, aur kuch situations mein code ya payloads bhi run karte hain. VAPT products PCI-DSS, GDPR, aur ISO27001 compliance mein madad karte hain.
Top VAPT Tools
Netsparker Security Scanner
Ek powerful vulnerability scanning aur management tool jo specially businesses ke liye design kiya gaya hai. Yeh SQL injection aur XSS jaise flaws ko detect aur exploit kar sakta hai. Netsparker koi bhi online application scan kar sakta hai, chahe woh platform ya programming language kuch bhi ho. Yeh unique hai kyunki Netsparker web application security scanner jo discovered vulnerabilities ko read-only aur secure tareeke se exploit karke validate karta hai. Iske saath yeh evidence bhi provide karta hai taaki aapko manually validate karne mein waqt na lage.Acunetix Scanner
Ek web app vulnerability scanner jo small aur medium-sized businesses ke liye hai, par yeh bade organizations ke liye bhi scale ho sakta hai. Yeh SQL injection, XSS, aur dusre threats ko detect kar sakta hai. Acunetix Web Vulnerability Scanner ek automated web application security testing tool hai jo aapke web applications ko vulnerabilities ke liye analyse karta hai, jaise SQL Injection, Cross-Site Scripting, aur dusre exploitable flaws.Intruder
Yeh ek web vulnerability assessment tool hai jo automated online web vulnerability testing tool ka use karke wide range of threats detect karta hai. Intruders woh attackers hote hain jo network ki security ko compromise karne ki koshish karte hain, aur unauthorized access lene ke liye network ko attack karte hain.Metasploit
Ek powerful framework jisme ready-to-use exploits code hota hai. Metasploit project vulnerabilities aur associated exploits ke baare mein information provide karta hai. Metasploit se pen testing team ready-made ya custom code use kar sakti hai aur network mein introduce karke weak spots probe kar sakti hai. Jab defects mil jate hain aur record ho jaate hain, toh yeh knowledge systemic weaknesses ko address karne aur remedies prioritize karne ke liye use ho sakta hai.
Notable Mentions
Nexpose, OpenVAS, Nmap, Wireshark, BeEF, aur John the Ripper aur bhi tools hain jo VAPT process mein madad karte hain.
Penetration Testing ke paanch significant types kya hain?
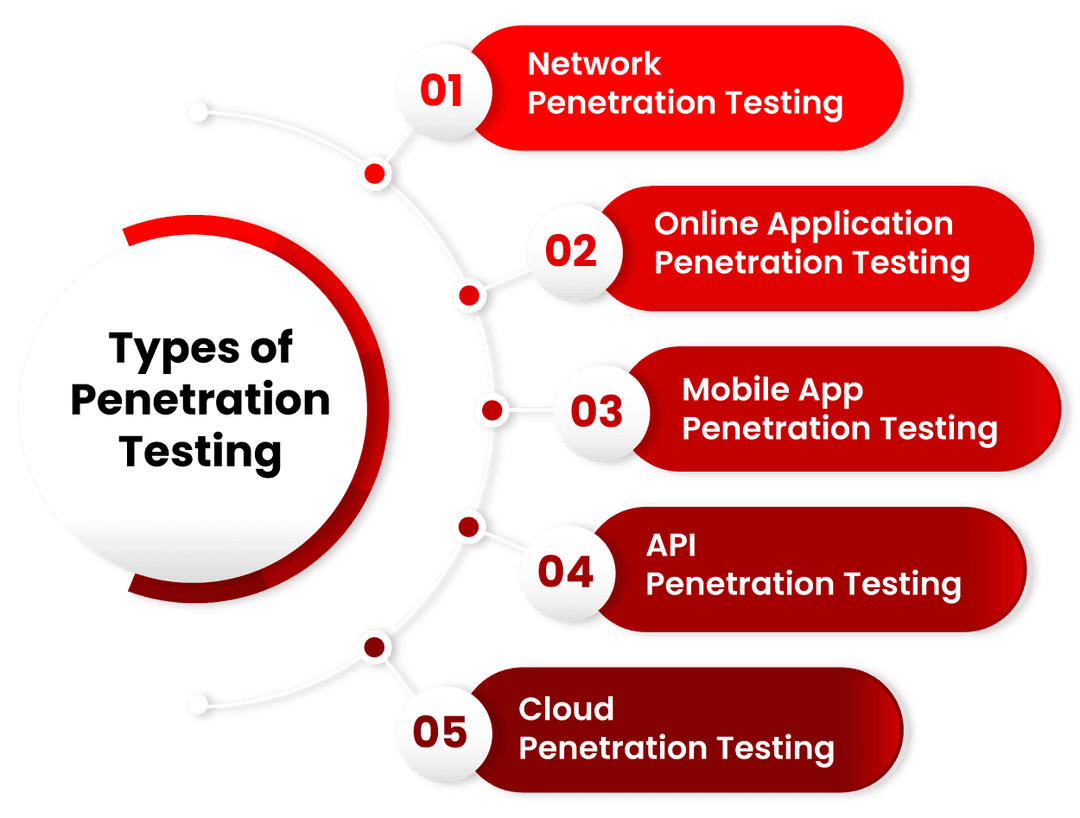
Network Penetration Testing
Ek organization ki cyber security kaafi had tak uske infrastructure pe depend karti hai. Data breach ke financial penalties ko dekhte hue, frequent internal aur external penetration testing karna zaroori hai taaki vulnerabilities ko discover karke unhe remedy kiya ja sake.
Network penetration test ek security assessment hota hai jo ethical hacking firms karte hain taaki cyber security flaws ko detect kiya ja sake jo on-premises aur cloud systems ko infiltrate karne ke liye exploit ho sakte hain. Isme perimeter security policies aur equipment jaise routers aur switches ko evaluate kiya jata hai.
Internal Network Penetration Testing
Internal network pen test yeh dekhne ke liye hota hai ki agar ek attacker ko initial network access mil jaye, toh wo kitna damage kar sakta hai. Insider threats, jaise employees ka malicious hona, chahe wo intentional ho ya accidental, ko bhi internal network pen test se mirror kiya ja sakta hai.
External Network Penetration Testing
External network pen test ka main goal perimeter security policies ki efficiency ko evaluate karna hai, taaki attacks ko prevent aur detect kiya ja sake, aur internet-facing assets jaise web, mail, aur FTP servers mein flaws find kiye ja sake.
Online Application Penetration Testing
Yeh testing ek set of processes hoti hai jo target system ke baare mein information gather karti hai, vulnerabilities ko identify karti hai, aur un flaws ko exploit karne ke liye research karti hai jo web application ko breach kar sakti hain. Web apps mein sensitive data hota hai, isliye unhe hamesha secure rakhna zaroori hai, khas taur par kyunki yeh publicly accessible hoti hain.
Mobile App Penetration Testing
Yeh testing mobile applications ki cyber security flaws ko identify karti hai. iOS aur Android apps ko sabse zyada assess kiya jata hai. Mobile app penetration testing apps ko protect karne mein madad karti hai aur fraud, viruses, malware infections, data leaks, aur doosri security breaches ke chances ko reduce karti hai.
API Penetration Testing
APIs ne cloud, IoT, aur mobile/web apps mein ek nayi digital transformation shuru ki hai. Har din log APIs ke saath interact karte hain bina iske pata chale. APIs data ko ek system se doosre system tak transfer karne ka kaam karti hain. Lekin kai baar, deployed APIs ko thorough security testing se nahi guzara jata, agar wo test kiye bhi jaye toh. Poorly protected APIs security flaws ko expose kar sakti hain jo unse connected systems ko compromise kar sakti hain. API ki security utni hi zaroori hai jitni applications ki.
Cloud Penetration Testing
Cloud penetration testing ek authorized simulated cyber-attack hota hai jo cloud providers jaise Amazon AWS ya Microsoft Azure pe hota hai. Iska primary goal system ke flaws aur strengths ko identify karna hai taaki uski security posture ko accurately assess kiya ja sake.
How often one should conduct VAPT?
VAPT ki frequency company ke diye gaye pen testing services pe depend karti hai. Yeh wahi wajah hai ki organizations apne goals achieve nahi kar paati. Wo sirf ek ya do baar saal mein ya kuch mahine ke gap pe yeh tests karte hain.
Compliance Standards and Certifications of VAPT
VAPT ke do types hote hain: Vulnerability Assessment aur Penetration Testing (VAPT)… Penetration tests ka aim system defects ko exploit karke yeh dekhna hota hai ki unauthorized access ya koi aur malicious activity ho sakti hai ya nahi, aur yeh assess karna ki faults application ke liye threat hai ya nahi.
VAPT Certification ek technology-based tareeka hai jo organization ki IT infrastructure (application, software system, network, etc.) mein security flaws ko address karta hai. Vulnerability Assessment ka purpose yeh hota hai ki vulnerabilities ko find kiya jaaye taaki koi loophole miss na ho.
Conclusion
VAPT testing businesses ke liye ek kaafi useful tool ho sakti hai. Yeh unki security level ko raise karti hai taaki wo cyber-attacks aur criminal activities se bacha ja sake. Isi liye, kai organizations ise seriously leti hain taaki valuable security benefits mil sake.
