Windows [MS-NRPC]: Netlogon Remote Protocol
Netlogon Remote Protocol (MS-NRPC) ek Microsoft RPC-based protocol hai jo Windows domain environments mein authentication aur secure channel communication ke liye use hota hai. Ye domain controllers (DCs) aur domain-joined machines ke beech authentication requests ko process karta hai. Iska main purpose secure logon operations, trust relationships, aur password replication ko facilitate karna hai. MS-NRPC authentication ko enhance karne ke liye AES encryption aur signing mechanisms use karta hai. Zerologon (CVE-2020-1472) jaise vulnerabilities ne is protocol ki security concerns ko highlight kiya, jis wajah se Microsoft ne stronger security enhancements introduce kiye.
Zerologon Vulnerability
CVE-2020-1472 (Zerologon) ek privilege escalation vulnerability hai jo Microsoft ke Netlogon Remote Protocol (MS-NRPC) me payi gayi hai. Ye vulnerability attackers ko bina authentication ke domain controller (DC) par full control lene ki ability deti hai. Iska exploitation actively ho raha hai, jisme attackers Netlogon secure channel ko bypass karke administrator privileges gain kar sakte hain.
Agar ek attacker internal network me foothold bana leta hai, toh woh sirf ek click me Domain Admin ban sakta hai. Bas itna zaroori hai ki attacker ka system Domain Controller (DC) se connect ho sake. Zerologon vulnerability ka exploit karke, attacker bina kisi authentication ke Netlogon secure channel ko manipulate kar sakta hai aur full domain control le sakta hai.
Ye attack Netlogon authentication protocol ke flaws ka fayda uthata hai, jo domain-joined computers ki authenticity aur identity ko validate karta hai.
Netlogon ke kamzor cryptographic algorithm ki wajah se, attacker kisi bhi computer account (including DC ka account) ki identity spoof kar sakta hai aur uska password empty set kar sakta hai.
Jyada tar cases me, is vulnerability ka exploitation sirf Active Directory me machine account password ko change karta hai, jabki local registry-backed password same rehta hai. Is wajah se domain aur local system ke passwords out of sync ho jate hain, jo potential lockout scenario create kar sakta hai.
Attacker is temporary hurdle ko easily bypass kar sakta hai by manually restoring the original password from Active Directory. Yeh NTDS.dit file se recover kiya ja sakta hai, jisme domain ke sare hashes stored hote hain. Impacket ka secretsdump tool ka use karke attacker yeh information extract kar sakta hai.
Ek aur alternative attack vector hai jisme password reset ki zaroorat nahi hoti—attacker Spool Service aur NTLM Relay ka use karke Zerologon vulnerability ko exploit kar sakta hai.
Is vulnerability ko Tom Tervoort (Secura BV) ne discover kiya tha aur Microsoft ne August 11, 2020 ko iske liye patch release kiya.
Netlogon Protocol
Netlogon Remote Protocol ek Remote Procedure Call (RPC) interface hai jo domain-based networks me user aur machine authentication ke liye use hota hai.
Ye protocol Backup Domain Controllers (BDCs) ke liye database replication bhi karta hai, taki redundancy maintain rahe.
Netlogon ka main role domain relationships maintain karna hai:
✅ Domain Members → Domain Controller (DC)
✅ DCs ke beech (same domain me)
✅ DCs ke beech (alag domains me)
Ye RPC interface domain relationships discover aur manage karne ke liye bhi use hota hai.
Zerologon Problem
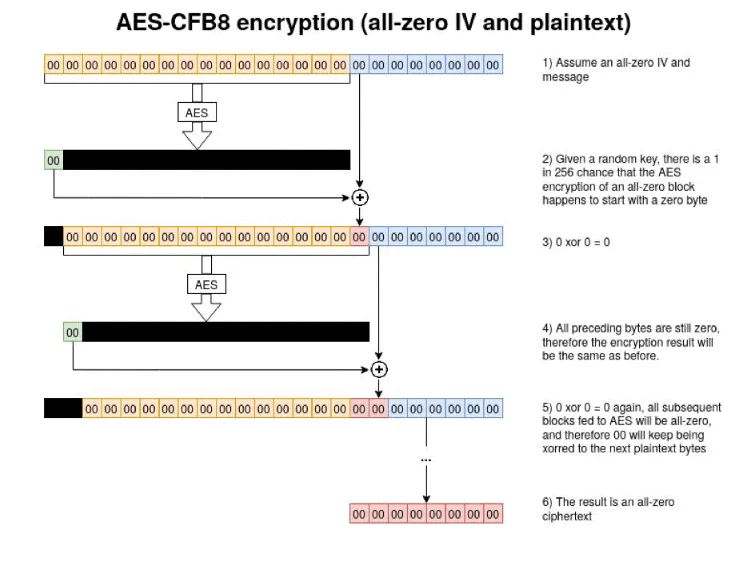
Netlogon Remote Protocol AES-CFB8 Encryption ka use karta hai. AES-CFB8 ek kamzor aur kam-use hone wali encryption mode hai kyunki ye zyada well-known ya well-tested nahi hai.
MS-NRPC me AES-CFB8 ka ek bada issue Initialization Vector (IV) se related hai, jo random number hona chahiye. AES-CFB8 ki security IV ke randomness par depend karti hai, lekin Netlogon RPC me IV ko 0 set kiya gaya hai (ComputeNetlogonCredential check ke under).
Is wajah se, har 256 attempts me ek baar, server ek aisa random key generate karega jo AES-CFB8 encryption ke baad zero byte produce karega, jo XOR operation ke liye use hota hai.
Zerologon Exploitation
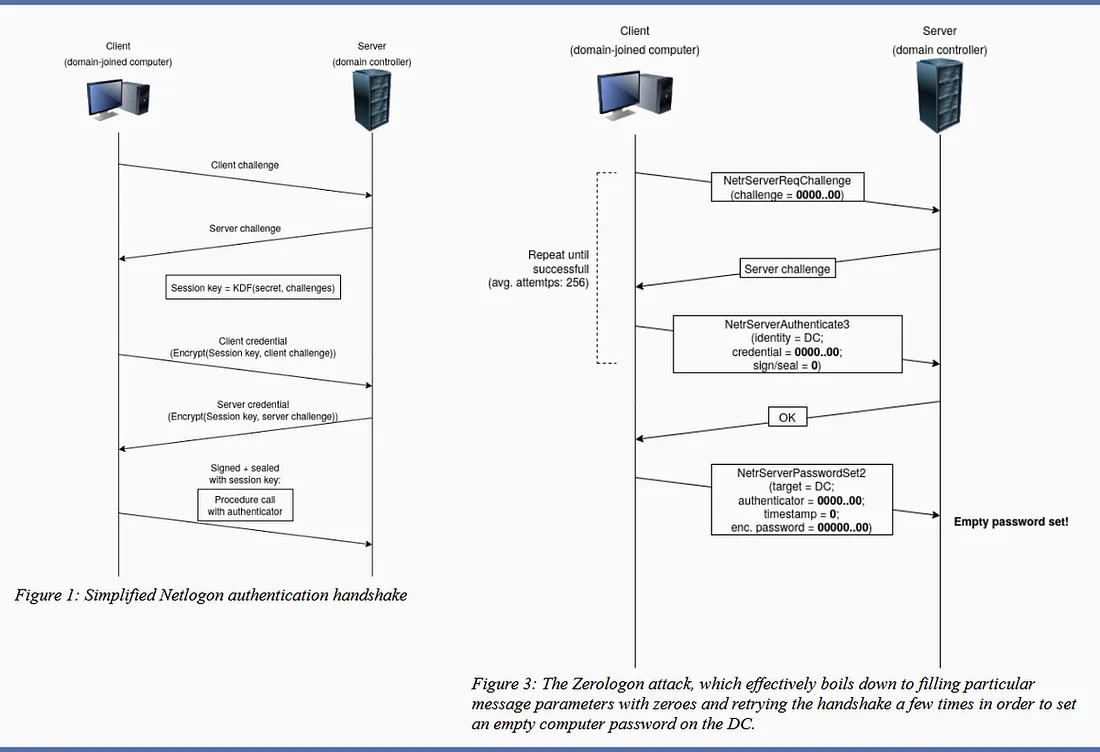
Netlogon Remote Protocol me NetrServerReqChallenge call, NetrServerAuthenticate3 function ka use karti hai, jo ek ClientCredential parameter leta hai.
ClientCredential ko NetrServerReqChallenge ke input se pass kiya jata hai, aur ye 8-byte value hoti hai jo kisi bhi arbitrary value ko accept kar sakti hai.
Attacker is value ko 0 (x8) set kar sakta hai aur agar woh bar-bar ye request send kare, toh ek iteration aisi hogi jab AES IV bhi 0 hoga aur NetrServerAuthenticate3 successfully execute ho jayega.
Zerologon Attack
Simple terms me, agar attacker bohot sare Netlogon messages bhejta hai jisme alag-alag fields ko zero se fill kiya gaya ho, toh woh Domain Controller (DC) ka computer password jo Active Directory me stored hota hai, usko change kar sakta hai.
Ye exploit Netlogon protocol ke cryptographic weakness ka fayda uthata hai, jisme AES-CFB8 IV = 0 hone par authentication bypass ho jata hai.
Impact of Zerologon
Ye attack bohot fast aur straightforward hai—sirf 3 seconds me execute ho sakta hai. Iska impact bohot dangerous hai, aur ransomware groups ne isse Ryuk ransomware jaise attacks me poore network me ransomware spread karne ke liye use kiya hai.
Agar kisi organization ne Microsoft ka August 11, 2020 security patch ab tak apply nahi kiya, toh unhe CVE-2020-1472 ka emergency patching karni chahiye.
Ab multiple public PoC exploits available hain, aur agar Active Directory (AD) servers patched nahi hain, toh businesses ko massive damage ho sakta hai.
Tervoort aur Secura ne GitHub par ek tool release kiya hai, jo check kar sakta hai ki aapke domain controllers patched hain ya vulnerable.
Zerologon Detection
Zerologon exploit ke baad kuch artifacts bante hain jo detection ke liye use kiye ja sakte hain. Hum teen important artifacts ko analyze karenge jo help karte hain Zerologon exploit detect karne me.
Windows Event Logs ke through Zerologon Detection
Windows apne Domain Controllers (DCs) me kuch relevant events create karta hai jo Zerologon exploit ko detect karne me madad karte hain. Zerologon exploit ko detect karte waqt, events ka set attacker ke exploitation method par depend karta hai.
Successful exploitation hone par, jo computer account password ko reset kiya gaya hota hai, uska record security logs me dikhega with Event ID 4742:
“A computer account was changed”
Password last set change
Performed by Anonymous Logon
Yeh logs indicate karte hain ki password change unauthorized source se kiya gaya hai, jo Zerologon exploitation ka result ho sakta hai.
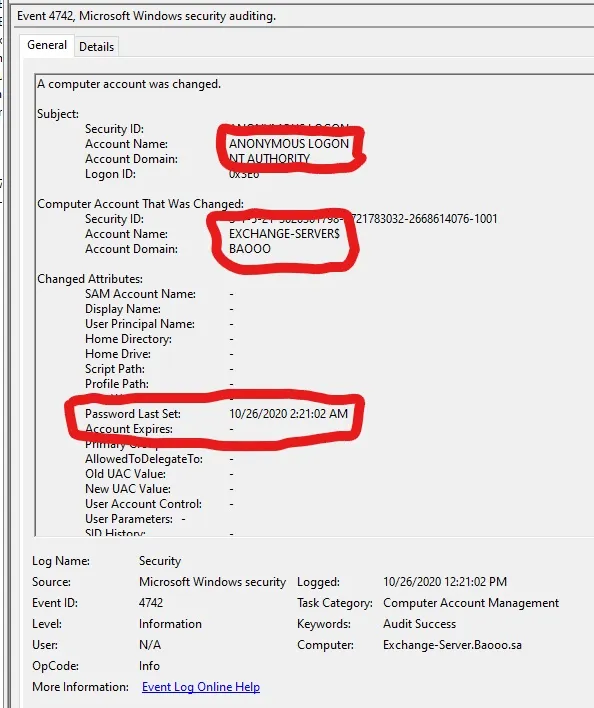
Event ID 4742 periodically hota hai, kyunki har 30 din mein Active Directory apne computer account passwords ko automatically reset karta hai. Isliye, yeh false positive detections lead kar sakta hai. Lekin isko dusre artifacts ke saath combine karna zaroori hai, jaise System Event ID 5805 “NETLOGON”, taaki accurate detection ho sake.
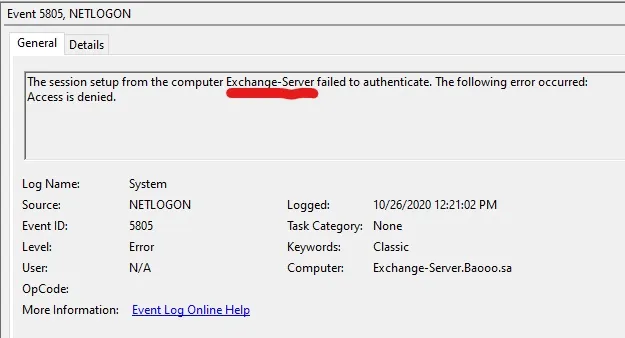
Aap System Event ID 5805 ko Security Event ID 4742 ke same timestamp pe dekh sakte hain, jo ki indicator of compromise ke roop mein kaam karta hai.
Next step hoga attacker ki authentication ko DC computer account ke through dekhna. Iske liye Impacket ka secretsdump tool use karke hashes dump kiye ja sakte hain. Yeh process Security Logs me Event ID 4624 ke saath dikhega:
“An account was successfully logged on”
Yeh event indicate karta hai ki attacker ne successfully logon kiya hai, jo Zerologon exploit ka ek aur evidence ho sakta hai.
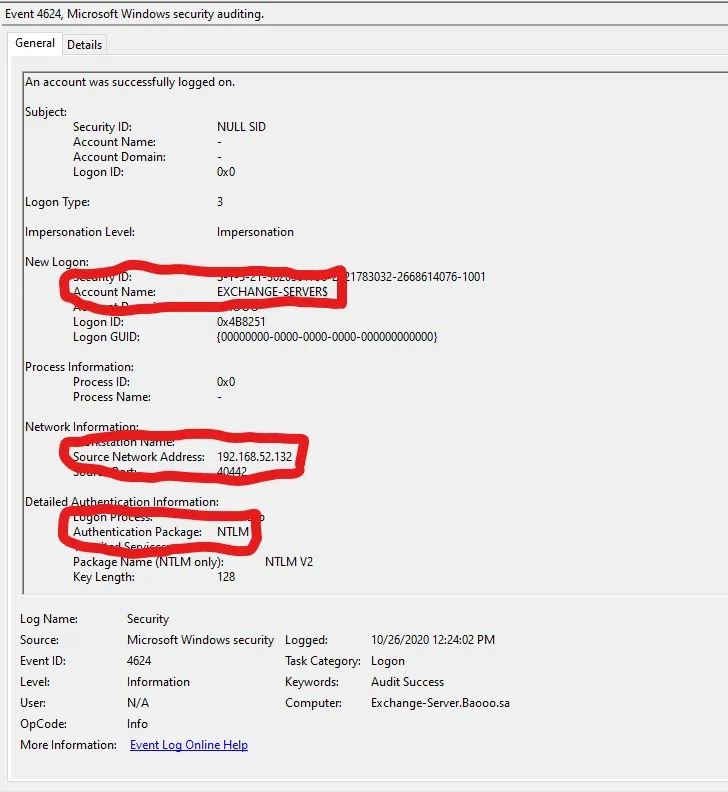
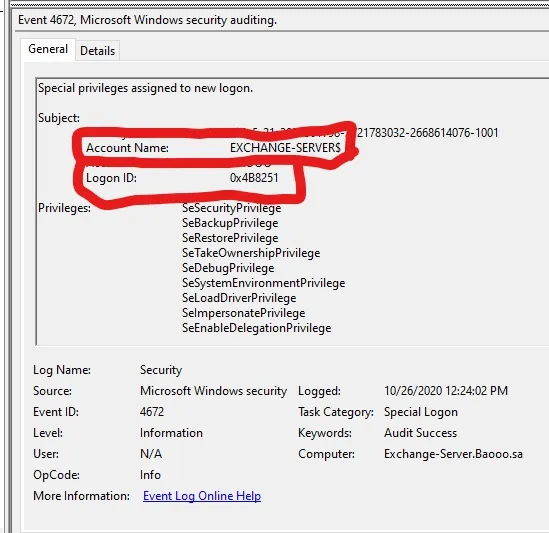
Same time pe, agar Windows Event ID 4672 bhi “Special privileges assigned to new logon” ke saath same Logon ID ke saath dikh raha ho, toh yeh strong indicator of compromise hai.
Iska matlab hai ki attacker ko special privileges assign kiye gaye hain, jo Zerologon attack ke baad escalated privileges ka sign ho sakte hain.
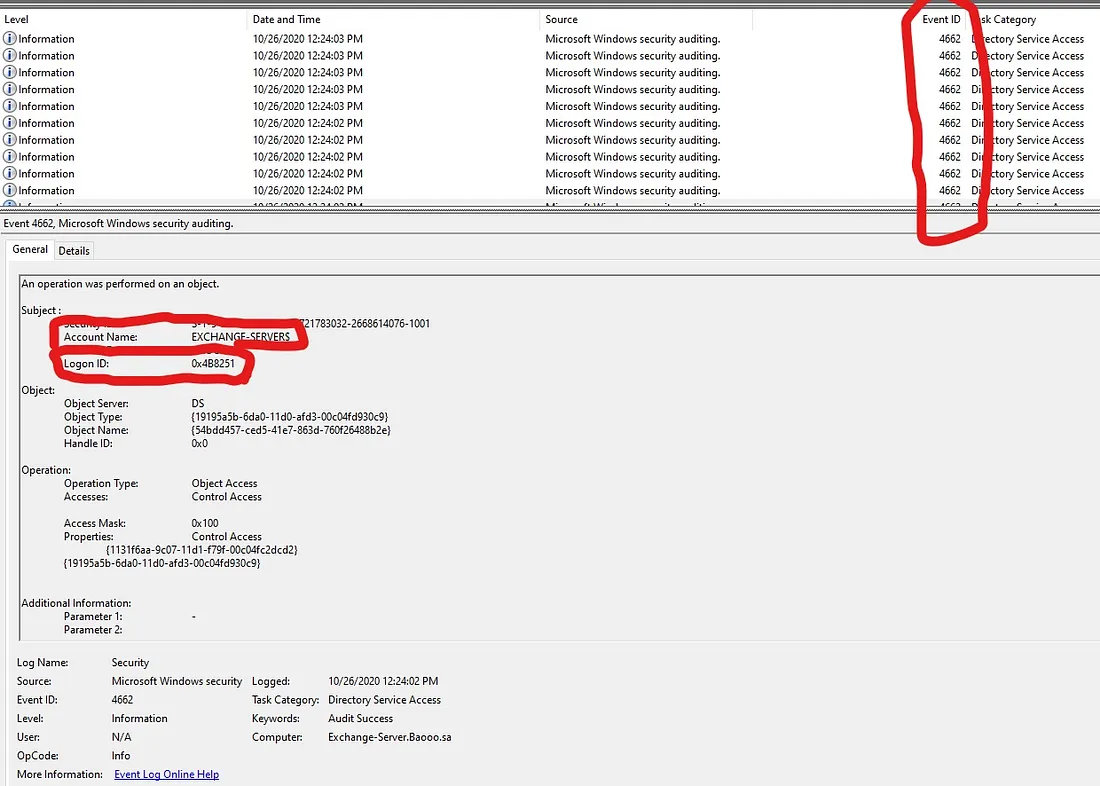
Iske alawa, multiple security logs generate honge with Event ID 4662:
-
-
“Directory Service Access”
-
Computer account aur same Logon ID ke saath.
-
Yeh logs indicate karte hain ki attacker ne directory service ko access kiya hai.
Windows security event ID 4742 aur system event ID 5805 “NETLOGON” already acche indicators hain Zerologon exploit ke liye environment mein.
Zerologon ko Netlogon debug file se detect karna:
Dusra method hai netlogon debug file, jo humein is vulnerability ke exploit hone ka significant sign de sakta hai. Dhyaan rakhein, yeh log file enable karna zaroori hai. Netlogon logging ko enable karne ke liye:
Ek Command Prompt window kholain (Windows Server 2008 aur baad ke versions ke liye administrative Command Prompt window).
Yeh command type karein aur Enter press karein:
Nltest /DBFlag:2080FFFF
Aapko detail Microsoft ke website par mil jayegi: Enable Debug Logging for Netlogon.
Jab hum exploit dobara launch karenge, to hum netlogon log file ko dekh sakte hain:
C:\Windows\debug\netlogon.txt
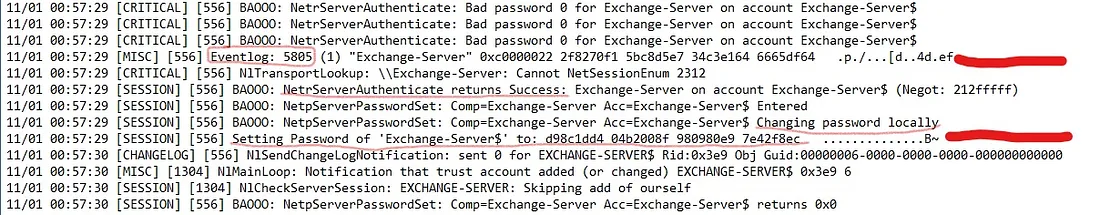
Pehle, humein kai failed netlogon attempts milenge, jo computer account par brute force hone ka indication denge.

Yahan hum wahi event log ID dekh sakte hain jo system logs mein trigger hui thi, aur computer account ka password bhi empty set hota hai.
Jab Zerologon exploit hota hai, to Netlogon debug file mein humein is tarah ke failed attempts aur empty password set hone ka clear indication milta hai. Yeh typical behavior hota hai jab attacker computer account ka password reset karne ki koshish karta hai, jo exploit ke successful hone ka sign hota hai.
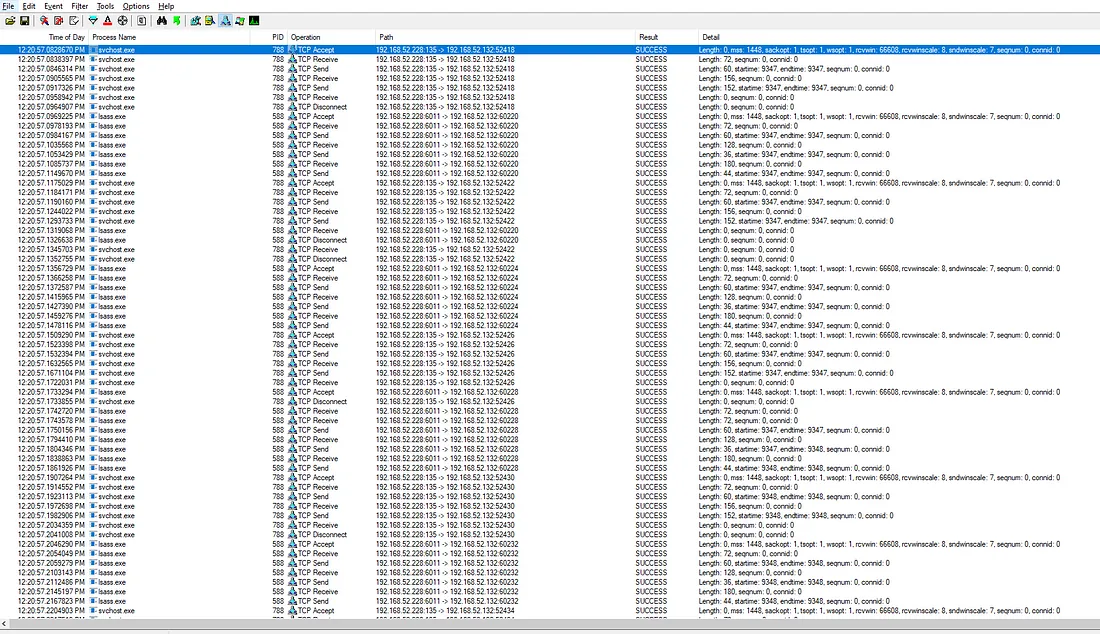
Zerologon ko Network ke zariye detect karna:
Zerologon ko detect karne ka teesra tareeka hai, jab network traffic mein abnormal spike dekhi jati hai, especially jab lsass aur svchost ke beech attacker ki taraf traffic increase hota hai. Yeh traffic key guessing step ka hissa hota hai exploit mein, jo brute force attempts jaise lagte hain.
Iska matlab hai, jab attacker exploit kar raha hota hai, to network traffic mein ek unusual spike aata hai, jo brute force tries ko resemble karta hai. Isse identify karke hum exploit ke hone ka pata laga sakte hain.
Conclusion:
Zerologon vulnerability ke publication ke baad, attackers ne environments ko compromise karna shuru kar diya hai aur apne tools ko spread kar rahe hain. Isliye, organizations ke liye CVE-2020-1472 ke liye patching karna zaroori aur important hai, taaki iss potential threat se combat kiya ja sake, aur yeh emergency basis par kiya jana chahiye.
References:
